How to Reduce Operational Costs: A Framework for Facilities and Operations Leaders
Your operational costs are leaking money. It’s not a question of if, but how much. For most multi-site organizations, the answer is a staggering 10-15% of their total operational budget, lost to a combination of billing errors, unused services, and inefficient processes.
This isn’t just a line item on a spreadsheet; it’s a direct hit to your company’s profitability. The pressure to reduce operational costs is immense, but traditional cost-cutting measures often feel like a blunt instrument, threatening service quality and team morale.
This guide offers a different approach. It provides a surgical framework for facilities and operations leaders to identify and eliminate waste without disrupting the business.
We will dissect the key drivers of operational costs, provide a step-by-step methodology for gaining control through enhanced spend visibility, and introduce the transformative power of centralized telecom expense management in achieving sustainable operational efficiency.
Key Categories Driving Your Operational Costs
To effectively manage costs, you must first understand where your money is going. For most multi-site organizations, operational expenses are concentrated in four main areas:
| Cost Category | Examples |
|---|---|
| Facility-Related Expenses | Utilities (electricity, water, gas), maintenance and repairs, rent, and property taxes. |
| Vendor and Service Costs | Waste management, landscaping, security services, telecom and connectivity, and software subscriptions. |
| Labor and Workforce Costs | Salaries, benefits, and outsourced operational support. |
| Administrative and Overhead | General and administrative (G&A) expenses that are not tied to a specific operational function. |
Without a centralized system, tracking these expenses across dozens or even hundreds of locations is a nearly impossible task, leading to missed savings and uncontrolled spending.
A 4-Step Framework for Reducing Operational Costs
A sustainable cost reduction program is not about across-the-board budget cuts. It is about making strategic decisions based on data. This framework provides a structured approach to identifying and acting on optimization opportunities.
Step 1: Establish a Cost Baseline and Spend Visibility
You cannot control what you cannot see. The first step is to aggregate all your operational spend data into a single, centralized platform. This creates a comprehensive cost baseline that allows you to analyze spending patterns by location, vendor, and service category. This is the foundation of spend visibility.
Step 2: Categorize Costs by Need and Performance
With a clear view of your spending, you can begin to categorize expenses. A simple but effective method is to classify costs as “essential,” “value-add,” or “non-essential.” This allows you to prioritize reduction efforts on areas that will not impact core operations.
Step 3: Define Cost Reduction Goals and KPIs
Set specific, measurable, achievable, relevant, and time-bound (SMART) goals for your cost reduction initiatives. Key performance indicators (KPIs) are essential for tracking progress. Examples include:
- Cost per square foot
- Energy consumption per location
- Vendor spend as a percentage of revenue
Step 4: Build Cross-Functional Collaboration
Operational cost reduction is a team sport. It requires collaboration between facilities, operations, finance, and procurement. By sharing data and aligning on goals, you can ensure that cost-saving measures are implemented effectively and do not create unintended consequences for other departments.
Practical Strategies to Reduce Operational Costs
With a framework in place, you can begin to implement practical strategies to lower your expenses.
- Streamline and Standardize Processes: Implement consistent procurement and payment processes across all locations to eliminate rogue spending and ensure compliance.
- Right-Size Vendor Services and Contracts: Analyze your vendor contracts to identify opportunities for consolidation, renegotiation, or elimination of underutilized services.
- Improve Asset and Resource Utilization: Track your assets to ensure you are not paying for services at closed or inactive locations.
- Automate Manual Financial Tasks: Automating invoice processing and payment workflows reduces labor costs, minimizes errors, and frees up your team to focus on more strategic activities.
The Role of Centralized Expense Management in Cost Reduction
Achieving sustainable cost optimization is nearly impossible with manual processes and disconnected systems. A centralized telecom expense management platform like RadiusPoint’s ExpenseLogic provides the technology backbone for your cost reduction program.
RadiusPoint helps you:
- Gain 100% Spend Visibility: Aggregate all your operational invoices into a single platform for a complete view of your spending.
- Automate Invoice Processing: Eliminate manual data entry and ensure invoice accuracy through automated validation and auditing.
- Optimize Vendor Management: Track all your vendor contracts and service agreements in one place to identify savings opportunities.
- Drive Actionable Insights: Use real-time dashboards and reporting to monitor your KPIs and make data-driven decisions.
By providing a single source of truth for all your operational expenses, ExpenseLogic empowers facilities and operations leaders to move from reactive firefighting to proactive cost optimization.
From Cost Center to Value Center
By implementing a structured approach to cost reduction, facilities and operations leaders can transform their departments from cost centers into strategic value drivers. Gaining control over your operational costs not only improves your company’s profitability but also frees up capital to invest in growth and innovation.
If you are ready to take control of your operational spending and drive sustainable cost optimization, contact RadiusPoint today to learn how RadiusPoint can provide the visibility and control you need to succeed.
How to Optimize P2P Invoice Processing: A Guide for AP and Finance Leaders
The accounts payable department is often seen as a tactical, back-office function, a necessary cost center focused on the repetitive task of paying bills. This outdated view misses the strategic importance of P2P invoice processing. In reality, the AP function is a goldmine of financial data and a critical control point in the procure-to-pay (P2P) cycle.
When optimized, it can drive significant cost savings, improve cash flow, and provide the spend visibility that finance leaders need to make informed decisions. However, for most organizations, this potential remains untapped, buried under a mountain of paper invoices and manual processes.
This guide is for the finance or AP leader who is ready to challenge the status quo and transform their accounts payable function. We will provide a detailed blueprint for optimizing your P2P invoice processing workflow, from invoice capture to payment authorization. We will also explore how centralized automation can help you reduce your cost per invoice, accelerate your invoice cycle time, and turn your AP team into a strategic asset for-profit engine for your business.
The Procure-to-Pay Lifecycle and the Role of Invoice Processing
The procure-to-pay lifecycle encompasses every step from the initial purchase requisition to the final vendor payment. Invoice processing is the critical link that connects procurement with payment, and it typically involves these five core components:
- Invoice Capture and Data Extraction: Receiving invoices from vendors (whether paper or electronic) and extracting the key data, such as invoice number, date, amount, and line-item details.
- Verification and Matching: Validating the invoice against the corresponding purchase order (PO) and proof of receipt. This is often referred to as three-way matching.
- Workflow Routing and Approval: Routing the invoice to the appropriate business owner for review and approval.
- Exception Handling: Managing and resolving discrepancies, such as price or quantity mismatches, that arise during the verification process.
- Payment Authorization: Authorizing the invoice for payment and scheduling it in the accounting or ERP system.
Why Manual P2P Invoice Processing Fails at Scale
For many organizations, these five steps are managed through a combination of email, spreadsheets, and manual data entry. This approach is not only inefficient but also fraught with risk.
| Pain Point | Financial Impact |
|---|---|
| High Processing Costs | Manual labor for data entry, validation, and approval routing can drive the cost per invoice to $15 or more. |
| Late Payment Penalties | Inefficient approval workflows and lost invoices lead to missed payment deadlines and unnecessary fees. |
| Lack of Spend Visibility | When invoice data is trapped in paper or disconnected systems, finance leaders have no real-time view of cash flow or budget performance. |
| Increased Risk of Fraud | Manual processes make it difficult to enforce financial controls, increasing the risk of duplicate payments and fraudulent invoices. |
A 5-Step Framework for P2P Invoice Optimization
Transforming your P2P invoice processing requires a systematic approach. This five-step framework provides a clear path to achieving greater efficiency and control.
Step 1: Capture All Invoices Efficiently
The foundation of AP automation is centralized invoice capture. By converting all incoming invoices (paper, PDF, EDI) into a single digital format, you create a standardized starting point for your workflow.
Step 2: Automate Matching Rules
Implement automated three-way matching to validate invoices against POs and receipts. This eliminates the need for manual review of compliant invoices, allowing your team to focus on exception handling.
Step 3: Streamline Approval Workflows
Configure automated invoice approval workflows to route invoices to the correct approvers based on business rules, such as department, GL code, or invoice amount. This accelerates the approval process and eliminates bottlenecks.
Step 4: Resolve Exceptions Quickly
Create a dedicated process for managing invoice exceptions. A centralized platform allows for clear communication and collaboration between AP, procurement, and business owners to resolve discrepancies quickly.
Step 5: Generate Insights and Metrics
Track key AP metrics to measure the performance of your P2P invoice processing function. This includes:
- Cost Per Invoice
- Invoice Cycle Time
- Exception Rate
- Early Payment Discounts Captured
The Role of Centralized Automation in P2P Excellence
Achieving true P2P invoice processing optimization is impossible without the right technology. A centralized AP automation platform like RadiusPoint’s ExpenseLogic provides the end-to-end capabilities you need to streamline your entire workflow.
RadiusPoint helps you:
- Automate Invoice Capture and Data Extraction: Eliminate manual data entry with intelligent OCR and machine learning.
- Enforce Financial Controls: Implement automated matching and approval rules to ensure compliance and prevent overpayments.
- Gain Real-Time Visibility: Use customizable dashboards to monitor your AP metrics and get a clear view of your cash flow.
- Integrate with Your ERP: Seamlessly connect with your existing accounting system to ensure data consistency and a single source of truth.
By automating your P2P invoice processing with telecom expense management, you can reduce your cost per invoice by up to 80%, shorten your invoice cycle time from weeks to days, and provide your finance team with the spend visibility they need to make strategic, data-driven decisions.
If you are ready to transform your accounts payable function and unlock the full potential of your procure-to-pay process, contact RadiusPoint today to learn how RadiusPoint can help.
What Is Operational Financial Management? A Guide for CFOs and Finance Leaders
The modern CFO is expected to be more than a financial steward; they are expected to be a strategic partner to the business. However, the reality for many finance leaders is that they are bogged down in the tactical details of financial operations.
The promise of data-driven decision-making is lost in a sea of spreadsheets, manual processes, and a fundamental lack of spend visibility. This is the challenge of operational financial management: aligning the day-to-day execution of financial processes with the long-term strategic goals of the organization.
This guide is designed for the strategic CFO who is ready to transform their financial operations from a reactive cost center into a proactive value driver.
We will explore the core principles of operational financial management, dissect the common challenges that stand in the way of financial excellence, and provide a roadmap for implementing the systems and processes needed to achieve true financial governance and control.
Operational vs. Strategic Financial Management
Understanding the distinction between operational and strategic financial management is crucial. While both are essential, they operate on different time horizons and with different objectives.
| Aspect | Strategic Financial Management | Operational Financial Management |
|---|---|---|
| Time Horizon | Long-term (3-5 years) | Short-term (daily, weekly, monthly) |
| Focus | Growth, profitability, capital structure | Liquidity, cash flow, cost control |
| Key Activities | Mergers and acquisitions, capital budgeting, dividend policy | Accounts payable, vendor payments, budgeting |
Operational financial management is the engine that powers your company’s strategic plan. Without effective financial operations, even the most brilliant strategy will fail due to poor execution.
Core Components of Operational Financial Management
A robust operational financial management framework is built on five key pillars:
- Cash Flow and Working Capital Management: Ensuring the business has sufficient liquidity to meet its short-term obligations. This includes managing receivables, payables, and inventory.
- Budgeting and Cost Control: Establishing departmental budgets, monitoring actual spend against those budgets, and implementing financial controls to prevent overspending.
- Accounts Payable and Vendor Payments: Managing the end-to-end process of receiving, approving, and paying vendor invoices accurately and on time.
- Accounts Receivable and Revenue Tracking: Ensuring that customer payments are collected on time to maintain healthy cash flow.
- Financial Reporting and Operational Visibility: Providing timely and accurate financial reporting to give stakeholders a clear view of the company’s performance and financial position.
Common Challenges in Operational Financial Management
Many organizations struggle to achieve excellence in their financial operations due to a common set of challenges:
- Limited Spend Visibility: Without a centralized system for tracking expenses, it is impossible to get a complete picture of where money is being spent, leading to missed savings opportunities and a lack of financial governance.
- Manual and Disconnected Processes: Manual invoice processing, approval routing, and data entry are time-consuming, error-prone, and create bottlenecks in the procure-to-pay cycle.
- Vendor and Contract Complexity: Managing thousands of vendor contracts, service agreements, and pricing structures in spreadsheets is a recipe for overpayments and missed renewal deadlines.
- Risk and Compliance Gaps: Manual processes make it difficult to enforce financial controls and create a clear audit trail, increasing the risk of fraud and non-compliance.
Best Practices for Strengthening Financial Operations
As a CFO, you can drive significant improvements in your company’s operational financial management by focusing on these best practices:
- Centralizing Financial Data: Consolidate all your operational spend data into a single platform to create a single source of truth and enable comprehensive financial reporting.
- Standardizing Workflows and Controls: Implement consistent processes for procurement, invoice approval, and payment across the entire organization to improve efficiency and strengthen financial governance.
- Automating Manual Tasks: Leverage technology to automate repetitive tasks like data entry, invoice validation, and payment scheduling to reduce costs and free up your team for more strategic work.
- Fostering Cross-Department Alignment: Break down silos between finance, procurement, and operations to ensure that financial decisions are made with a full understanding of their operational impact.
The Role of Technology in Modernizing Financial Operations
Technology is a critical enabler of effective operational financial management. A centralized expense management platform like RadiusPoint’s ExpenseLogic provides the tools you need to transform your financial operations.
RadiusPoint helps you:
- Achieve Real-Time Spend Visibility: Gain a complete, up-to-the-minute view of your operational spending across all locations and departments.
- Automate the Procure-to-Pay Cycle: Streamline your entire invoice management process, from receipt to payment, with automated workflows and controls.
- Strengthen Financial Governance: Enforce your financial controls and create a complete audit trail for every transaction.
- Unlock Actionable Insights: Use powerful analytics and reporting to identify cost-saving opportunities and make more informed financial decisions.
By embracing technology and adopting these best practices, you can transform your financial operations from a tactical, back-office function into a strategic asset that drives business value.
If you are ready to take your company’s operational financial management to the next level, contact RadiusPoint today to learn how RadiusPoint can help you achieve your goals.
Telecom Cost Optimization: A 6-Step Framework for IT and Finance Leaders
Your telecom bills are a black box. For most organizations, telecom spend is a significant and growing operational expense, yet it remains one of the least understood and most poorly managed cost categories.
The complexity of telecom services, with their myriad of vendors, contracts, and billing formats, creates a perfect storm for overspending. Billing errors, charges for unused services, and suboptimal contract terms are the norm, not the exception.
Telecom cost optimization is the process of shining a light into this black box, and for most companies, it represents one of the largest and most immediate opportunities to impact the bottom line.
This guide is for the IT, finance, or procurement leader who is ready to take control of their company’s telecom spend. We will provide a proven, six-step framework for telecom cost optimization, moving from reactive bill payment to proactive telecom expense management (TEM).
We will also show how a centralized platform can provide the spend visibility and control you need to eliminate waste and drive sustainable savings.
Key Cost Drivers in Your Telecom Environment
To effectively manage your telecom spend, you must first understand the primary factors that drive your costs. For most organizations, these fall into three main categories:
| Cost Driver | Description |
|---|---|
| Service Complexity | A mix of fixed-line, mobile, and data services from multiple vendors, each with its own contract terms, pricing, and billing cycles. |
| Lack of Visibility | Decentralized management of telecom services across different departments and locations, leading to a fragmented and incomplete view of total spend. |
| Inefficient Processes | Manual processes for invoice validation, auditing, and payment, which are time-consuming, error-prone, and prevent proactive management. |
These challenges are compounded by the sheer volume and complexity of telecom invoices, which are often riddled with errors, hidden fees, and charges for services that are no longer in use.
A 6-Step Framework for Telecom Cost Optimization
A successful telecom cost optimization program is a continuous cycle of analysis, action, and monitoring. This six-step framework provides a structured path to gaining control over your telecom spend.
Step 1: Establish a Spend Baseline
The first step in any telecom expense management initiative is to create a complete and accurate inventory of all your telecom services and assets. This involves aggregating all your telecom invoices into a single, centralized platform to establish a comprehensive spend baseline.
Step 2: Audit and Validate Invoices
Once you have a complete view of your spending, you can begin to audit your telecom invoices for errors and discrepancies. This includes verifying rates against your vendor contracts, identifying charges for unused services, and flagging any unauthorized fees.
Step 3: Analyze Usage vs. Services
Compare your actual usage data with the services you are paying for. This analysis often reveals significant savings opportunities, such as right-sizing data plans, eliminating underutilized phone lines, and identifying employees with multiple devices.
Step 4: Optimize Contracts and Vendors
Armed with data from your audit and analysis, you can begin to optimize your vendor contracts. This may involve consolidating services with a single provider, renegotiating rates based on your usage patterns, or terminating contracts for redundant or unnecessary services.
Step 5: Implement Governance and Policy Controls
Establish clear policies for the procurement, use, and management of telecom services. This includes creating a standardized process for adding or removing services, setting guidelines for mobile device usage, and implementing approval workflows for all telecom-related expenses.
Step 6: Monitor and Improve Continuously
Telecom cost optimization is not a one-time project. It is an ongoing process of monitoring your telecom spend, tracking your key performance indicators (KPIs), and continuously identifying new opportunities for savings and efficiency.
The Role of a Centralized Platform in Telecom Expense Management
Attempting to manage the complexities of telecom spend with spreadsheets and manual processes is a losing battle. A centralized telecom expense management platform like RadiusPoint’s ExpenseLogic is essential for achieving sustainable cost optimization.
RadiusPoint provides the tools you need to:
- Automate Invoice Management: Centralize all your telecom invoices in a single platform and automate the process of invoice validation, auditing, and payment.
- Gain Complete Spend Visibility: Use real-time dashboards and reporting to get a clear, consolidated view of your telecom spend across all vendors, locations, and service types.
- Optimize Your Wireless and Mobile Spend: Effectively manage your mobile device inventory, track usage, and identify opportunities to reduce costs in your wireless environment.
- Streamline Vendor and Contract Management: Keep all your vendor contracts and service agreements in one place to ensure you are getting the services and pricing you negotiated.
By providing a single source of truth for all your telecom expenses, RadiusPoint empowers you to take control of your spending, eliminate waste, and drive significant savings for your organization.
If you are ready to move beyond the chaos of manual telecom expense management and build a sustainable cost optimization strategy, contact RadiusPoint today to learn how RadiusPoint can help you achieve your goals.
Why Businesses Conduct Energy Audits and What They Reveal
For most businesses, energy is one of the largest and most unpredictable operating expenses. Utility bills are rising, budget pressure is increasing, and there’s a growing demand for sustainable business practices.
In response, many leaders are asking a critical question: “We know our energy costs are high, but we don’t have clear visibility into our usage.
Where do we even start?”
The answer is an energy audit.
An energy audit is the first and most important step in taking control of your organization’s energy consumption. It’s a systematic review of how, where, and when your business uses energy, and it provides a clear roadmap for reducing costs and improving efficiency.
What Is a Business Energy Audit?
A business energy audit is a comprehensive analysis of your energy consumption and billing data to identify opportunities for cost savings and efficiency improvements. It goes far beyond a simple walkthrough of your facility.
A proper commercial energy assessment involves a detailed examination of your utility invoices, rate structures, and consumption patterns to uncover hidden inefficiencies and billing errors.
The primary purpose of an energy audit is to answer three key questions:
- How much energy is our business using?
- Where are we wasting energy and money?
- What are the most cost-effective ways to reduce our consumption and costs?
Why an Energy Audit Is a Strategic Imperative
Conducting a thorough energy audit is not just an exercise in data collection. It’s a strategic initiative that delivers significant benefits across the entire organization.
Unlock Hidden Cost Savings
This is the most immediate and compelling benefit. A detailed audit can uncover billing errors, identify overcharges, and reveal opportunities to switch to more favorable rate plans. The result is immediate and ongoing cost savings that flow directly to your bottom line.
Boost Operational Efficiency
An energy audit often reveals operational inefficiencies that go beyond energy consumption. By understanding how and when you use energy, you can optimize processes, improve equipment performance, and reduce maintenance costs, leading to a leaner, more efficient operation.
Strengthen ESG and Sustainability Goals
For companies with ESG (Environmental, Social, and Governance) goals, an energy audit provides the foundational data needed to measure, manage, and report on their environmental impact. It’s a critical first step in any credible sustainability program, providing the verifiable data that stakeholders demand.
The Hidden Hurdles in Conducting an Energy Audit
While the benefits are clear, many businesses struggle to conduct effective energy audits. The challenges are often rooted in the complexity and fragmentation of energy data.
- The Data Deluge: For multi-location businesses, energy data is often scattered across hundreds of PDF invoices from dozens of different utility providers. There is no centralized system to aggregate and analyze this information, making a comprehensive audit nearly impossible.
- The Resource Drain: In-house teams are already stretched thin. They rarely have the time or specialized expertise to conduct a detailed audit of complex utility bills, which are notoriously difficult to decipher.
- The Accuracy Trap: Manual data entry is prone to errors, leading to an inaccurate picture of your energy consumption. Without consistent, reliable data, it’s impossible to benchmark facilities or track the impact of efficiency initiatives.
- The Action Gap: An audit is only as valuable as the actions you take based on its findings. Many businesses lack the resources to implement the recommended changes and track the resulting savings, leaving money on the table.
How Centralized Data Transforms Energy Audits
The solution to these challenges is to centralize your energy data. By automating the collection and processing of your utility invoices, you can create a single source of truth for your energy consumption and costs.
This is where a technology-driven partner like RadiusPoint can make a significant impact.
Our ExpenseLogic platform ingests, processes, and audits all your utility invoices, regardless of the provider or format.
This provides the clean, accurate, and centralized data needed to conduct a thorough and effective energy audit. Instead of spending weeks or months manually collecting data, you can get instant visibility into your energy spend and identify savings opportunities in a fraction of the time.
What Happens After an Energy Audit?
An energy audit is not the end of the journey; it’s the beginning. The audit report will provide a list of recommended actions, from simple operational changes to more significant capital investments.
The next step is to prioritize these actions based on their cost, potential savings, and alignment with your business goals.
This is where a partner like RadiusPoint can provide ongoing support. We not only help you conduct the initial audit, but we also provide the ongoing monitoring and reporting needed to track your progress, measure your savings, and ensure that your energy management program delivers long-term value.
Final Thoughts
In today’s competitive landscape, businesses can no longer afford to treat energy as an uncontrollable expense. An energy audit is the first step in transforming your energy management from a reactive, administrative task into a proactive, strategic discipline.
By leveraging technology and expert support to overcome the common data challenges, you can unlock the full potential of an energy audit and turn valuable insights into measurable bottom-line savings.
Ready to uncover your hidden energy savings?
Contact RadiusPoint today to learn more about our energy audit services.
Vendor Contract Management: A Complete Guide for Modern Organizations
In today’s interconnected business landscape, organizations rely on a complex web of third-party vendors for everything from software and telecom services to utilities and office supplies.
A contract governs each of these relationships – a legally binding document that outlines deliverables, timelines, and costs. But as the number of vendors grows, so does the complexity of managing these contracts.
This is where vendor contract management becomes a critical business discipline.
For many leaders, the common concern is a lack of visibility: “We have contracts in place, but no clear visibility into what we’re actually paying for.” This isn’t just a minor administrative headache; it’s a significant source of financial risk and operational inefficiency.
Explore RadiusPoint Vendor Cost Recovery solution.
What Is Vendor Contract Management?
Vendor contract management is the process of creating, negotiating, storing, and tracking contracts with third-party suppliers. It’s a comprehensive approach that covers the entire lifecycle of a contract, from initial creation to final renewal or termination. The goal is to ensure that both parties fulfill their contractual obligations, maximize the value of the contract, and minimize any associated risks.
This process is distinct from procurement, which focuses on sourcing and purchasing goods and services. This management concerns the ongoing relationship and the legal agreement that governs it.
Why Vendor Contract Management Is Important for Businesses
Effective contract management is not just about good record-keeping. It’s a strategic function that delivers tangible benefits across the organization.
- Cost Control and Spend Visibility: By centralizing all your vendor contracts, you gain a clear view of your financial commitments. This helps you identify opportunities for cost savings, eliminate redundant services, and negotiate better terms with your suppliers.
- Risk and Compliance Management: Every contract comes with its own set of risks, from data security and privacy to regulatory compliance. A formal contract management process ensures that these risks are identified, assessed, and mitigated.
- Operational Efficiency: When contracts are managed in an ad-hoc manner, it leads to wasted time, missed deadlines, and strained vendor relationships. A streamlined process automates key tasks, frees up internal resources, and ensures that your vendors are delivering on their promises.
Common Challenges in Vendor Contract Management
Despite its importance, many organizations struggle with effective contract management. The challenges are often rooted in a lack of process and visibility, creating significant operational friction.
The Problem of Contract Sprawl
As companies grow, contracts get scattered across different departments, locations, and even individual employees’ hard drives. This “contract sprawl” makes it impossible to get a unified view of your vendor relationships. Without a central repository, you can’t know what you’ve agreed to, when renewals are due, or where your risks lie.
Poor Visibility Into Usage vs. Contract Terms
Are you actually using all the software licenses you’re paying for?
Is your telecom provider billing you at the agreed-upon rate?
For many businesses, the answer is a resounding “we don’t know.” Without a system to track usage against contract terms, you’re likely overspending on services you don’t need or paying more than you should.
Missed Renewal and Renegotiation Opportunities
Many contracts have auto-renewal clauses that lock you into unfavorable terms if you don’t act in time. A proactive contract management process ensures that you never miss a renewal deadline and that you have the data you need to renegotiate from a position of strength. Missing these opportunities is like leaving money on the table.
Vendor Contract Management for Telecom, Utilities, and Mobility
Nowhere are these challenges more acute than in the management of telecom, utility, and wireless contracts. These services are essential for modern businesses, but their contracts are notoriously complex, and their invoices are often riddled with errors.
- Telecom Vendor Contracts: These contracts are filled with technical jargon, complex service level agreements (SLAs), and a dizzying array of fees and surcharges. Auditing these invoices against the contract terms requires specialized expertise.
- Utility Vendor Contracts: With a mix of regulated and deregulated markets, utility contracts can be incredibly confusing. Optimizing these contracts requires a deep understanding of tariff rates, energy markets, and local regulations.
- Mobility and Wireless Vendor Contracts: Managing contracts for hundreds or even thousands of mobile devices is a logistical nightmare. A centralized contract management system is essential for tracking assets, optimizing plans, and controlling costs.
Explore the RadiusPoint service for more precise solutions
The Role of Technology in Vendor Contract Management
For multi-location and enterprise businesses, managing vendor contracts manually is simply not feasible. Technology is the key to creating a scalable and efficient process.
A modern vendor contract management platform can:
- Centralize all your contracts in a single, searchable repository.
- Automate key tasks like renewal reminders and performance tracking.
- Provide real-time visibility into your spending and usage.
- Integrate with your accounting and procurement systems to create a seamless, end-to-end process.
At RadiusPoint, we specialize in managing the most complex vendor contracts—telecom, utility, and wireless. Our ExpenseLogic platform, combined with our team of expert auditors, provides a complete BPO solution for vendor contract management. We handle the complexity so you can focus on your core business.
Final Thoughts
Vendor contract management is no longer a back-office administrative task. It’s a strategic discipline that can drive significant cost savings, reduce risk, and improve operational efficiency.
By embracing a proactive, technology-driven approach, you can transform your vendor contracts from a source of complexity into a source of competitive advantage.
Ready to take control of your vendor contracts? Contact RadiusPoint today to learn how we can help.
What Is ESG Reporting? A Practical Guide for Modern Businesses
Not long ago, Environmental, Social, and Governance (ESG) goals were a “nice-to-have” for many organizations, a footnote in an annual report or a small section on the company website. Today, that has fundamentally changed.
ESG reporting has moved from the periphery to the core of business strategy, driven by intense pressure from investors, regulators, and customers who demand transparency and accountability.
But for many executives, a common concern has emerged: “We have ESG goals, but no clear way to report on them accurately.”
This isn’t a failure of ambition; it’s a data problem.
So, what is ESG reporting, and why has it become one of the most critical challenges for businesses today?
What Is ESG Reporting?
ESG reporting is the process of publicly disclosing an organization’s data related to its environmental, social, and governance performance. It’s a framework for measuring a company’s impact beyond its financial results. Unlike traditional financial reporting, which focuses on profit and loss, this reporting provides a holistic view of a company’s sustainability and ethical footprint.
Let’s break down the three pillars:
- Environmental (E): This pillar covers a company’s impact on the planet. The data required includes energy consumption, water usage, greenhouse gas (GHG) emissions (Scope 1, 2, and 3), waste management, and resource depletion.
- Social (S): This pillar addresses how a company manages relationships with its employees, suppliers, customers, and the communities where it operates. Key data points include employee health and safety, labor standards, diversity and inclusion metrics, and data privacy.
- Governance (G): This pillar deals with a company’s leadership, executive pay, audits, internal controls, and shareholder rights. It’s about ensuring the company is managed ethically, transparently, and in the best interests of its stakeholders.
While often confused with Corporate Social Responsibility (CSR) or sustainability reports, ESG reporting is distinct. It is a data-driven, formal disclosure process tied to specific frameworks (like GRI, SASB, or TCFD) and is increasingly scrutinized by investors and regulators.
Read RadiusPoint Case Study on ESG for an in-depth understanding.
Why ESG Reporting Is No Longer Optional
The shift toward mandatory and standardized reporting is being driven by three powerful forces:
- Investor and Financial Pressure: Investors and lenders no longer see ESG as a non-financial issue. They recognize that strong ESG performance is a proxy for good management and long-term financial resilience. They are increasingly using ESG data to assess risk, allocate capital, and make investment decisions.
- Regulatory and Compliance Expectations: Governments worldwide are introducing regulations that mandate ESG disclosure. The European Union’s Corporate Sustainability Reporting Directive (CSRD) and the U.S. Securities and Exchange Commission’s (SEC) proposed climate disclosure rules are just two examples. Compliance is quickly becoming non-negotiable.
- Brand Trust and Customer Expectations: Modern consumers want to buy from and work for companies that align with their values. A strong, transparent ESG report is a powerful tool for building brand trust, attracting and retaining talent, and differentiating your business in a crowded market.
Why Is ESG Reporting So Hard?
If the importance of ESG is so clear, why do so many companies struggle with it? The answer lies in the data. It is fundamentally a data collection, aggregation, and validation challenge. The traditional approach is often a logistical nightmare.
- Manual Data Collection: Key data, especially for the “Environmental” pillar, is often trapped in thousands of PDF utility bills, spreadsheets, and disparate vendor portals. Collecting this information manually is a monumental task, prone to human error.
- Accuracy and Consistency Issues: Without a centralized system, ensuring data is accurate, consistent, and auditable across dozens or hundreds of locations is nearly impossible. How can you be sure the energy consumption data from one facility is measured the same way as another?
- Time and Resource Drain: The manual effort required to gather, clean, and report on ESG data consumes thousands of hours from finance, operations, and sustainability teams, pulling them away from their core responsibilities.
Read how RadiusPoint eliminated 800 hours of manual data collection for ESG reporting.
How Technology Simplifies ESG Data Collection
The biggest hurdle in this reporting is often the “E” in ESG, specifically, gathering accurate data on energy consumption, emissions, and other environmental metrics. This is where technology and specialized services can make a transformative impact.
At RadiusPoint, we support organizations by automating the most challenging part of this process. Our core business is processing and auditing complex, location-based invoices, including telecom, utility, and waste. This provides a direct, automated, and auditable data stream for your reporting needs.
Instead of manually chasing down hundreds of utility bills, our platform captures, validates, and centralizes all your energy and utility data. This means that when it’s time to report on your Scope 2 emissions or overall energy consumption, the data isn’t just available, it’s accurate, consistent, and ready for your ESG framework.
Conclusion: From Burden to Business Intelligence
ESG reporting is evolving from a burdensome compliance exercise into a powerful source of business intelligence that can unlock cost savings, mitigate risk, and enhance brand value. The key to success is moving beyond manual processes and embracing a data-driven approach.
By automating the collection of foundational data, like your energy and utility consumption, you can transform reporting from a source of frustration into a strategic advantage. It allows you to focus less on chasing data and more on using it to build a more resilient, sustainable, and profitable business. Ready to streamline your ESG data collection?
Learn how RadiusPoint can provide the accurate, auditable data you need to power your ESG reporting.
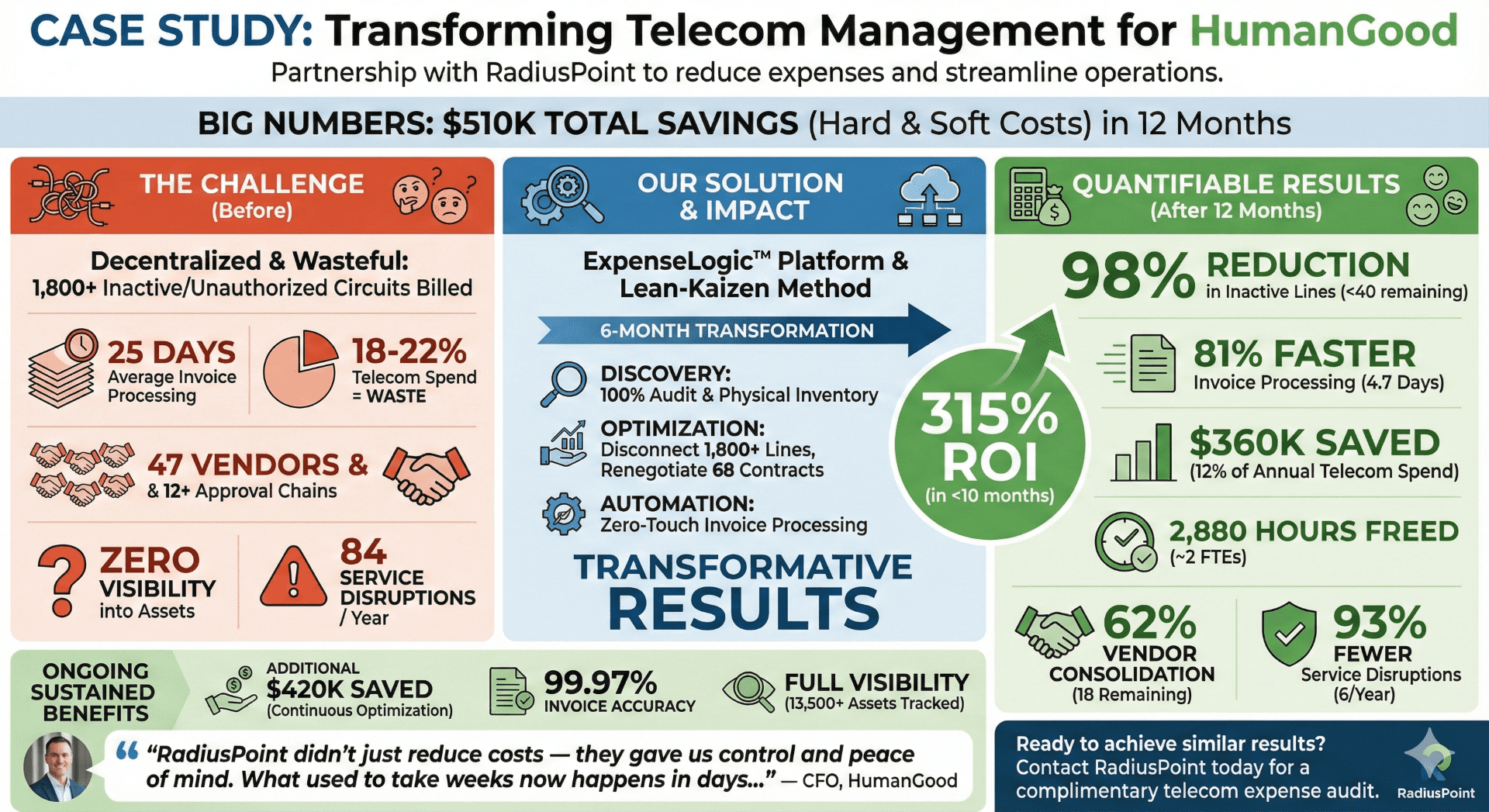
How Human Good Achieved a 315% ROI with RadiusPoint
Discover how one of America’s largest nonprofit senior living providers partnered with RadiusPoint to eliminate operational waste, drive significant savings, and establish a new benchmark for nonprofit efficiency through a technology-enabled shared services model.
Executive Summary
HumanGood, the sixth-largest nonprofit owner and operator of senior living communities in the U.S., was grappling with a decentralized and inefficient telecom expense management process. This system created significant financial leakage, operational burdens, and service disruptions that impacted over 9,200 residents.
By partnering with RadiusPoint, HumanGood undertook a strategic transformation, leveraging the ExpenseLogic platform and a shared services model to centralize and automate its entire telecom lifecycle.
The initiative delivered transformative results, proving that strategic automation can drive immense value in the nonprofit sector.
Key Metrics at a Glance:
- $360,000 in Annual Hard-Dollar Savings (12% of total spend)
- $150,000 in Annual Labor Efficiencies (soft savings)
- 315% Average Monthly Return on Investment (ROI)
- Invoice Cycle Time Reduced from 30 Days to 5 Days
- 99.9% Invoice Processing Accuracy
The Client: A Mission-Driven Leader in Senior Living
HumanGood stands as a pillar in the nonprofit sector, dedicated to helping older adults live with purpose and joy. Operating over 100 affordable housing communities and 22 life plan communities across five states, the organization serves more than 9,200 residents. As a nonprofit, HumanGood operates with a profound sense of fiduciary responsibility.
Every dollar saved is a dollar that can be reinvested into its core mission: enhancing the quality of life for its residents.
This commitment to stewardship was the driving force behind its decision to address long-standing operational inefficiencies.
The Challenge: A Fractured System Undermining a Noble Mission
Before partnering with RadiusPoint, HumanGood’s approach to managing its vast telecom infrastructure was fragmented and manual. Lacking a centralized system, the organization faced a cascade of challenges that created a significant financial and operational drag.
1. Severe Financial Leakage
The decentralized process was rife with uncontrolled spending. Without proper oversight, unauthorized service orders were common, and inactive services often remained connected and billed for months.
The absence of a unified repository for invoices and contracts made it impossible to audit costs effectively, leading to substantial and unnecessary financial waste.
2. Crippling Operational Inefficiency
The Accounts Payable department was mired in a paper-based workflow that took 20 to 30 days to process a single telecom invoice. This involved manually chasing down data, seeking approvals, and coding invoices, a workload that consumed the equivalent of three full-time staff members.
The process was not only slow but also prone to errors, frequent delays, and misplaced invoices, creating frustration for both staff and vendors.
3. Complete Lack of Visibility
With no central database, HumanGood had no clear view of its telecom assets, services, or contractual obligations. This lack of visibility made it impossible to manage inventory, ensure compliance with vendor agreements, or make informed, data-driven decisions about its telecom spend.
4. Negative Impact on Residents and Staff
The operational shortcomings had real-world consequences. Service disruptions caused by missed or delayed payments directly impacted residents’ connectivity and well-being.
Internally, the frustrating and repetitive manual tasks led to low morale and diverted skilled finance professionals from more strategic, value-added work.
The Solution: A Strategic Partnership for End-to-End Transformation
RadiusPoint introduced a comprehensive, technology-enabled shared services solution designed to address HumanGood’s challenges from the ground up.
This was not merely a software installation but a strategic partnership focused on redesigning processes, aligning technology, and empowering people.
The core of the solution was RadiusPoint’s proprietary ExpenseLogic platform, which served as the engine for automation and centralization.
The multi-faceted solution included:
- End-to-End Invoice Lifecycle Automation: RadiusPoint assumed full responsibility for HumanGood’s telecom invoice lifecycle. The ExpenseLogic platform automated everything from invoice receipt and processing to validation and payment, creating a single, streamlined workflow and reducing the cycle time to just five days.
- Comprehensive Audit and Cost Optimization: The engagement began with a deep-dive audit of all existing telecom services and contracts. This process immediately identified and disconnected inactive services and optimized vendor contracts, yielding immediate hard-dollar savings.
- Centralized Order and Inventory Management: Recognizing a critical gap, the project expanded to include full order management. All requests for new services or disconnections were centralized through ExpenseLogic, complete with automated approval paths and clear audit trails. This eliminated unauthorized orders and created a reliable, real-time inventory of all telecom assets.
- Advanced Analytics and Real-Time Reporting: The ExpenseLogic platform provided HumanGood with on-demand access to dashboards and advanced analytics. For the first time, leadership could see a clear, accurate picture of telecom spend, track performance metrics, and make strategic decisions based on reliable data.
The Methodology: A Framework for Lasting Change
RadiusPoint’s success was underpinned by a hybrid Lean-Kaizen methodology. This dual approach focused on Lean principles to identify and eliminate non-value activities (waste) and Kaizen principles to foster a culture of continuous, team-driven improvement.
The implementation followed a structured six-month roadmap, ensuring a smooth transition without disrupting critical operations.
A cornerstone of the methodology was a robust change management and stakeholder engagement strategy.
RadiusPoint recognized that technology alone is not enough. To ensure adoption and long-term success, they focused on winning the trust of key stakeholders.
- Overcoming Resistance: Resistance from IT middle management, who feared a loss of control, was addressed through education and by demonstrating how automation would serve as an enabler, not a replacement. Once they saw how the platform enhanced visibility and reduced repetitive tasks, they became strong advocates.
- Building Internal Champions: The Accounts Payable team, initially burdened by the manual process, became the most supportive group. Freed from tedious tasks, they championed the new automated system, helping to educate their peers and build momentum for the initiative.
- Data-Driven Communication: The most effective tool for winning support was a “What If” business case presentation that quantified the financial and productivity losses of maintaining the status quo. This, combined with weekly progress reviews and customized dashboards, made the benefits of the transformation tangible and undeniable for all stakeholders.
The Results: A New Standard for Nonprofit Efficiency
The partnership delivered results that exceeded all initial targets, creating a powerful ripple effect across the entire HumanGood organization.
| Metric | Before Transformation | After Transformation with RadiusPoint | Impact |
| Annual Hard-Dollar Savings | Uncontrolled Spending | $360,000 | 12% reduction in total spend from service optimization. |
| Annual Labor Efficiencies | 3 FTEs on Manual Tasks | $150,000 | Staff reallocated to higher-value strategic work. |
| Average Monthly ROI | N/A | 315% | Demonstrates exceptional and sustainable value creation. |
| Invoice Cycle Time | 20–30 Days | 5 Days | 80% reduction, eliminating delays and service disruptions. |
| Invoice Processing Accuracy | Prone to Human Error | 99.9% | Near-perfect accuracy, ensuring financial integrity. |
Beyond these impressive numbers, the initiative transformed HumanGood’s operational culture. It fostered a commitment to continuous improvement, improved cross-functional collaboration between IT, Finance, and Operations, and established a repeatable model for automation-driven efficiency.
This success has not only strengthened HumanGood’s financial position but has also solidified its ability to deliver on its core mission for years to come.
Client Testimonial:
“The transformation was a major value-add, improving cost control, data integrity, and resident satisfaction. The outcome was a fully integrated, end-to-end telecom management process that enhanced financial accuracy, operational visibility, and strategic alignment with our shared services objectives. RadiusPoint’s expertise and technology were pivotal in achieving this success.”
— HumanGood Stakeholder
Transform Your Organization’s Potential into Performance
HumanGood’s story is a powerful testament to what is possible when a mission-driven organization embraces strategic automation.
If your organization is facing similar challenges with expense management, RadiusPoint can help.
Ready to see how much you could save?
- Schedule a Demo – Get a personalized tour of the ExpenseLogic platform.
- Contact Sales – Speak with one of our experts to discuss your specific needs.
What is Vendor Governance?
Vendor governance is called the structured framework organizations use to manage relationships with their third-party vendors, ensuring accountability, compliance, and value delivery. It’s not just about contract management – it’s about enforcing standards, reducing risks, and ensuring each vendor’s performance aligns with the company’s strategic goals.
In an era where businesses rely on dozens (sometimes hundreds) of external vendors, from software providers to utilities, vendor governance serves as the backbone of operational reliability and financial integrity. Without proper governance, organizations face higher risks of compliance breaches, cost leakages, and inconsistent service delivery.
Understanding the Basics of Vendor Governance
It establishes the rules, processes, and oversight mechanisms that ensure vendors perform according to defined business, legal, and ethical standards.
At its core, it covers:
- Contract compliance: Ensuring vendors meet the obligations and terms outlined in service agreements.
- Performance management: Measuring and monitoring service levels through KPIs and audits.
- Risk and compliance control: Reducing exposure to data breaches, financial errors, or non-compliance with regulations.
- Financial visibility: Tracking spend, invoices, and cost optimization across multiple vendor categories.
- Strategic alignment: Ensuring vendors support business outcomes, innovation goals, and sustainability initiatives.
When properly executed, vendor governance transforms vendor management from a reactive function into a proactive, strategic discipline that strengthens enterprise-wide resilience.
Why Vendor Governance Matters More Than Ever
The past few years have redefined vendor dynamics. With rising outsourcing, supply chain diversification, and increasing ESG accountability, it’s no longer optional; it’s essential.
Increased Compliance Pressure
Organizations face mounting scrutiny from regulators, auditors, and investors. Frameworks like GDPR, SOC 2, and ISO 27001 require consistent vendor oversight. A well-structured governance model ensures every vendor relationship adheres to security, privacy, and sustainability mandates.
2. Cost and Performance Accountability
Without governance, vendor costs can spiral unchecked. Rogue spending, hidden fees, and overlapping contracts are common. Governance introduces systematic invoice validation, performance benchmarking, and audit readiness – reducing unnecessary expenditure.
3. Risk Mitigation
Vendors handle sensitive data, infrastructure, or utilities that directly impact business continuity. Governance reduces risks associated with vendor failure, compliance violations, or service disruptions by maintaining continuous visibility and defined escalation protocols.
4. ESG and Sustainability Reporting
With environmental and social governance (ESG) rising in importance, enterprises now evaluate vendors based on ethical sourcing, carbon impact, and labor standards. Governance frameworks help integrate these metrics into vendor assessments and performance reviews.
The Core Elements of a Strong Vendor Governance Framework
A robust governance program typically includes five foundational pillars:
- Vendor Onboarding and Qualification: Verifying vendor credentials, certifications, and financial stability before engagement.
- Performance Management: Defining KPIs and SLAs, conducting periodic evaluations, and documenting scorecards.
- Risk and Compliance Monitoring: Performing risk assessments and ensuring compliance with internal and regulatory policies.
- Contract and Spend Management: Centralizing contracts, validating invoices, and automating billing error detection.
- Continuous Improvement: Using performance analytics to drive efficiency, negotiate better terms, and enhance vendor collaboration.
Organizations that implement these elements consistently reduce operational risks, optimize spend, and build stronger vendor partnerships.
Challenges in Implementing Vendor Governance
Despite its benefits, many organizations struggle to operationalize this governance due to fragmented systems, limited visibility, and a lack of specialized expertise.
Common challenges include:
- Siloed data across departments (procurement, finance, IT).
- Manual invoice validation and reporting processes.
- Reactive dispute resolution instead of preventive controls.
- Poor documentation and audit readiness.
- Limited oversight for non-strategic vendors (like utilities).
These pain points highlight why specialized vendor governance solutions are becoming increasingly critical.
RadiusPoint: Smart Vendor Management
As organizations refine their vendor governance frameworks, one area consistently emerges as a critical blind spot-utility expense management. Utilities represent a substantial portion of indirect spend, often dispersed across multiple locations, service types, and billing entities. These vendors are high in volume but low in visibility, making them a prime source of billing errors, duplicate payments, and compliance risks.
RadiusPoint bridges this operational gap. With decades of expertise in Utility Expense Management (UEM) and technology-driven vendor oversight, RadiusPoint transforms how enterprises control, monitor, and optimize utility-related vendor relationships. Its governance-focused approach converts complex billing data into actionable intelligence, strengthening both financial accuracy and compliance assurance.
RadiusPoint’s governance model is built around precision, automation, and partnership. Each engagement is designed to minimize administrative burden while maximizing accountability and savings.
Key advantages include:
- Specialized expertise in utility and telecom expense management-an often overlooked but high-impact vendor category.
- Automated governance workflows that streamline invoice validation, contract compliance, and vendor performance tracking.
- Proactive cost recovery that directly improves profitability and cash flow management.
- Reduced operational workload for procurement, AP, and finance teams through automation and data integration.
- Enhanced compliance assurance, ensuring every transaction meets corporate, legal, and regulatory standards.
- Strategic reporting that provides leadership visibility into spend performance and governance health.
It combination of domain expertise and technology-driven transparency helps enterprises achieve governance maturity without overcomplicating operations. It delivers the visibility, accountability, and cost efficiency that traditional vendor management systems struggle to provide.
Building a Resilient and Value-Driven Vendor Ecosystem
This governance is no longer a back-office process-it is a core component of business resilience and value creation. A well-governed vendor ecosystem reduces risk exposure, strengthens compliance, and delivers measurable financial returns.
RadiusPoint embodies these principles through its focused approach to utility expense management. By automating processes, enforcing compliance, and recovering lost value, it helps enterprises transform fragmented vendor relationships into a cohesive, performance-driven network.
Organizations seeking to build a resilient governance framework benefit most when they combine internal policy discipline with specialized partners who bring operational precision and technology depth.
Explore how RadiusPoint’s utility expense management solutions can help your enterprise strengthen vendor governance, recover lost value, and build a smarter, more transparent vendor ecosystem.
What is Invoice Processing? A detailed guide for businesses
Invoice processing (or accounts-payable workflow) involves receiving supplier invoices, capturing their data, matching them to purchase orders, routing for approval, and completing payment. Manual handling of this process can be slow and error-prone.
For example, processing 1,000–2,000 invoices per month can consume hundreds of staff hours. Automated invoice processing uses software (OCR and AI) to streamline and digitize the receipt, verification, and approval of supplier invoices. By replacing paper workflows with digital capture and rules-based routing, companies can pay suppliers faster and improve accuracy.
Manual Invoice Workflow (Challenges)
Traditional (manual) invoice processing typically follows these steps:
- Invoice Receipt: Invoices arrive by mail, fax, or email.
- Data Entry: AP staff manually key in invoice details (vendor, date, amount, GL coding).
- Verification: Manual 2-way/3-way matching to purchase orders and receipts; exceptions are flagged.
- Approval: Paper or email routing to managers for sign-off.
- Payment: Checks or electronic payments are prepared and sent.
- Filing: Invoices and approvals are filed (paper or scanned) for record-keeping.
Common issues include:
- Inefficiency: Manual entry is time-consuming and ties up staff.
- Payment Delays: Missed deadlines result in lost discounts or late fees.
- Human Errors & Fraud: Typing mistakes, skipped approvals, and duplicate payments increase risk.
- Compliance Burdens: Difficulties in tracking vendor tax forms or applying tax rates accurately.
- Visibility Gaps: Lack of real-time insight into payables and spending.
Automated Invoice Processing (Benefits)
Key advantages of automation include:
- Faster Processing: Reduces invoice-to-payment time dramatically.
- Lower Error Rates: Automated matching and validations minimize mistakes.
- Cost Savings: Processing costs drop significantly due to reduced manual labor.
- Labor Productivity: Staff can shift focus from data entry to higher-value tasks.
- Improved Cash Management: Captures early-payment discounts and avoids late fees.
- Auditability & Spend Visibility: Automated systems provide audit trails and real-time dashboards.
- Security and Controls: Built-in checks and role-based access help enforce compliance.
Challenges and Drawbacks of Automation
Automation is powerful but not without challenges:
- Upfront Costs & Integration: Significant investment and IT setup may be required.
- Reduced Human Oversight: Some exceptions still need manual review.
- Vendor Variability: Diverse invoice formats can challenge automated systems.
- Change Management: Staff training and buy-in are critical for success.
- Complex Setup and Maintenance: Business rules must be configured and maintained accurately.
Compliance and Regulatory Considerations in Invoice Processing (U.S.)
Invoice processing must align with U.S. legal and regulatory frameworks:
- Record Retention: Invoices should be stored for 3–7 years, depending on the requirement.
- Digital Records Legality: E-invoices are valid if securely stored with audit trails.
- HIPAA (Healthcare): Invoices containing patient data must comply with HIPAA privacy and security rules.
- Tax Reporting (1099s): Vendor tax form collection and correct coding are essential for IRS compliance.
- Industry-specific Rules: Additional standards may apply in retail, healthcare, education, and manufacturing.
Industry-Specific Considerations
Each industry has unique invoice processing needs:
Healthcare
HIPAA compliance, insurance claims, and remittance advice management.
Retail & Hospitality
High invoice volume, tax rules, and credit card compliance.
Manufacturing
Global suppliers, freight invoices, and three-way matching.
Education (Non-profit)
Grant tracking and compliance with audit standards.
General Business
Adherence to accounting standards and audit readiness.
Best Practices for Invoice Processing
To ensure success, organizations should:
- Standardize and digitize invoices: Promote e-invoicing and scan paper invoices promptly.
- Leverage AI-based capture: Use adaptive systems that learn from invoice variability.
- Implement robust matching rules: Automate validation and flag exceptions.
- Maintain audit trails: Track all actions to support compliance and internal control.
- Train and document policies: Ensure clear procedures and consistent handling.
- Monitor performance: Use KPIs to measure processing time, errors, and cost savings.
- Stay updated on regulations: Adjust systems as tax laws and industry rules evolve.
Key Takeaways
Efficient invoice processing improves financial control, reduces costs, and strengthens compliance. Automation transforms AP from a manual bottleneck into a strategic function by streamlining data capture, accelerating approvals, and enhancing visibility. Organizations should balance automation with human oversight and adapt workflows to industry-specific requirements. With a well-structured system and an informed team, invoice processing becomes a driver of accuracy, accountability, and operational efficiency.
In summary, a thorough invoice processing strategy blends industry-tailored compliance with smart automation: standardize and digitize invoices, use AI/ML capture to handle variability, and maintain controls and records. This approach keeps processes lean and compliant, turning AP from a bottleneck into a strategic asset.
15 Effective Ways to Reduce IT Costs for Businesses
IT leaders and CIOs are under constant pressure to control expenses without stalling innovation. According to Gartner, global IT spending is projected to reach $5 trillion in 2024, driven by cloud adoption, AI integration, and security requirements. These rising costs necessitate that businesses consider long-term solutions beyond short-term cost reductions and implement sustainable cost-reduction strategies.
“Reducing IT costs and accelerating innovation are not mutually exclusive. When done right, cost discipline should enable innovation.” — Arvind Joshi, COO & CFO, Global Technology, JPMorgan Chase. This perspective highlights the dividends of smarter IT management—businesses save capital while positioning themselves for long-term scalability.
The following strategies offer actionable steps for reducing IT costs while maintaining performance and driving innovation.
Reassess Cloud Costs
Cloud services are often over-provisioned. Many businesses purchase more storage, computing power, or licenses than they use. According to Flexera’s 2024 State of the Cloud Report, 32% of cloud spending is wasted on underutilized resources.
A cost-reduction approach starts with monitoring workloads and rightsizing resources. Businesses should also implement spending thresholds, schedule automated shutdowns for idle services, and consolidate workloads across fewer providers.
Optimizing cloud contracts ensures IT budgets reflect actual consumption rather than inflated projections.
Revisit the Hardware Stack
Legacy infrastructure creates hidden costs through higher maintenance fees, frequent downtime, and energy inefficiencies. Older servers require more power and cooling, driving operational expenses.
By upgrading to energy-efficient servers, adopting virtualization, or migrating workloads to the cloud, businesses cut capital expenditure and reduce total cost of ownership.
Evaluating the hardware stack annually helps avoid paying for systems that no longer align with operational needs.
Recheck Project Portfolio
IT teams often juggle multiple projects, but not all deliver measurable returns. Projects with low adoption, unclear objectives, or outdated outcomes drain budgets and staff hours.
Portfolio rationalization means pausing, combining, or retiring projects that no longer align with business objectives.
CIOs should prioritize high-value initiatives that contribute directly to growth, security, or customer experience. This reduces cost leakage while ensuring resources are directed toward innovation.
Move Toward Consumption-Based Contracts
Paying for fixed resources leads to inefficiencies. A consumption-based model, often called pay-as-you-go, allows businesses to pay only for the services they actively use. This approach applies to cloud storage, networking, and even software licensing.
Consumption-based contracts reduce the risk of over-committing and allow IT budgets to flex with real demand. Businesses that shift to this model improve cost predictability and align IT spend with revenue cycles.
Realign IT Support Models
Traditional support agreements charge a flat fee for comprehensive services, but many organizations only need partial coverage. A tiered or remote-first support model helps businesses match costs with actual needs.
Shared-service arrangements or managed service providers also reduce internal labor costs while ensuring expert coverage. Realigning support saves money without compromising uptime or reliability.
Optimize Sourcing Strategies
Vendor sourcing directly impacts IT budgets. Relying on a single vendor may limit negotiation power, while managing too many suppliers creates administrative overhead.
A balanced approach, through competitive bidding or hybrid sourcing, drives cost savings while maintaining service quality. Regular sourcing reviews ensure that vendor relationships remain aligned with pricing trends and technology requirements.
Align Sourcing With Business Objectives
Sourcing decisions should extend beyond price comparisons. Vendors tied to strategic outcomes deliver more value than those based on transactional contracts. Value-based sourcing includes service-level agreements tied to performance, efficiency, or customer satisfaction metrics.
This alignment eliminates unnecessary spending on misaligned services and promotes stronger accountability across vendor partnerships.
Audit All Existing Contracts
Many businesses continue paying for outdated or overlapping contracts because renewals are automated or unnoticed. Quarterly or biannual audits uncover these inefficiencies.
Auditing ensures that subscription software, cloud services, and telecom contracts reflect current business requirements. Terminating redundant agreements or consolidating providers often leads to substantial savings.
Conduct Application Rationalization
Maintaining redundant applications is one of the most common sources of IT waste. Licensing fees, integration costs, and staff training expenses multiply when multiple tools serve the same function.
Rationalizing applications, by consolidating into a single enterprise suite or reducing overlapping platforms, lowers costs and simplifies management. For example, replacing multiple collaboration tools with a single enterprise system reduces both licensing and support expenditures.
Embrace IT Automation
Automation removes repetitive tasks such as system patching, user provisioning, monitoring, and incident response. Beyond cost savings, automation improves accuracy and reduces downtime.
Automated IT processes allow staff to focus on higher-value initiatives like digital transformation or customer service enhancements. Over time, automation produces measurable reductions in labor and operational overhead.
Adopt Expense Management Software
Expense management software provides visibility into IT, telecom, and utility costs. Platforms like RadiusPoint’s expense management solution centralize expense tracking, generate detailed reports, and identify inefficiencies.
By implementing such solutions, businesses prevent billing errors, optimize vendor contracts, and streamline payment processes. Data-driven insights transform expense management into a proactive cost-control function.
Reduce, Don’t Freeze IT Spending
Freezing IT budgets is a short-term reaction that stifles innovation. Instead, businesses should reduce expenses strategically by cutting non-essential services while continuing to fund critical areas such as cybersecurity, cloud modernization, and automation.
This approach safeguards innovation pipelines while still achieving meaningful cost reductions.
Improve IT Cash Flow Strategies
Cash flow management improves financial flexibility. Options include leasing hardware instead of purchasing outright, adopting subscription-based models, or extending payment schedules.
Shifting from large capital expenses (CAPEX) to predictable operating expenses (OPEX) ensures budgets remain balanced while meeting technology requirements.
Renegotiate Vendor Contracts
Vendors are often open to renegotiation when presented with alternatives. Businesses reduce costs by consolidating purchases, extending contract terms, or negotiating discounts.
Regular renegotiations not only cut immediate expenses but also establish stronger vendor accountability. Preparing benchmarks before discussions helps CIOs secure more favorable terms.
Implement IT Asset Lifecycle Management
Unmanaged IT assets lead to unnecessary purchases and lost efficiency. Lifecycle management ensures assets are monitored from procurement to retirement.
Strategies include redeploying underutilized devices internally, extending device lifespans with proper maintenance, and scheduling structured decommissioning. This approach maximizes asset value while avoiding redundant expenditures.
Strengthen Governance and Cost Transparency
Governance frameworks help create accountability for IT spending. Regular reporting at the department or project level builds transparency and ensures that budgets align with corporate strategy.
Cost transparency fosters informed decision-making, enabling CIOs to make adjustments before costs spiral out of control.
Final Thoughts
Reducing IT costs is not about cutting corners—it is about creating efficiency, accountability, and resilience. CIOs and business leaders who reassess contracts, rationalize applications, adopt automation, and leverage expense management software position their organizations for both savings and scalability.
As Arvind Joshi of JPMorgan Chase noted, cost discipline and innovation go hand in hand. By treating cost optimization as a continuous process rather than a one-time initiative, businesses strengthen their financial health while keeping technology aligned with long-term growth.
10 Best Vendor Management Practices for SMBs & Enterprises
Vendor management is the structured process of selecting, onboarding, monitoring, and optimizing relationships with external suppliers. In 2025, it will no longer be limited to negotiating prices or securing contracts. It now involves risk mitigation, data security, sustainability compliance, and the use of digital tools to ensure operational resilience.
The stakes are higher than ever. According to Gartner, 83% of legal and compliance leaders detect vendor risks only after due diligence is complete, which often proves too late to prevent disruption.
The global economy adds further complexity, with nearly 80% of organizations experiencing at least one supply chain disruption in the past year (Supply Chain Dive).
For procurement leaders and business owners, strong vendor management practices are not optional—they are a strategic imperative.
What Are the Key Phases of the Vendor Management Lifecycle?
The vendor lifecycle stretches from initial sourcing through to offboarding. Each phase requires structured actions to prevent inefficiencies and risks.
In the selection phase, organizations evaluate vendors against cost, compliance, and performance criteria. Yet 43% of organizations still lack visibility into tier 1 supplier performance, which results in poor decision-making.
During contract negotiation and onboarding, alignment on service levels and compliance clauses helps avoid disputes. AI-driven tools now accelerate contract analysis and highlight risk terms that would otherwise be overlooked.
The performance monitoring phase focuses on real-time KPI tracking, regular feedback, and collaborative sessions. Without this, budgets suffer—only 34% of projects are delivered on budget, often due to weak vendor tracking.
Finally, the renewal or offboarding phase ensures that long-term value is reviewed, and vendors who underperform are replaced. A structured evaluation process prevents vendor lock-in and reduces risk exposure.
How Do Clear Policies and Criteria Improve Vendor Selection?
Clear policies define the foundation for consistent vendor decisions. A structured policy sets measurable criteria for cost, service quality, compliance, and alignment with business goals. By using scorecards during RFPs, procurement leaders reduce bias and drive objective evaluations.
Companies that lack these policies face higher project overruns and hidden costs. With only 34% of projects meeting budget expectations, structured vendor policies are essential for cost control and risk reduction.
Why Should Vendor Data Be Centralized for Better Monitoring?
Vendor information is often fragmented across departments, leading to duplication, compliance gaps, and blind spots. Centralizing this data creates a single source of truth where contracts, performance metrics, and compliance records are monitored.
According to Deloitte, 48% of organizations find tracking third-party partners a considerable challenge. Centralized monitoring addresses this issue and enables proactive management.
Platforms such as RadiusPoint integrate contract details, invoices, and risk indicators into one dashboard, providing procurement and IT leaders with real-time visibility.
How Can Collaborative Relationships Strengthen Vendor Performance?
Vendors deliver better results when treated as strategic partners rather than transactional suppliers. Collaboration involves scheduling reviews, exchanging performance feedback, and aligning on shared goals.
This trust-driven approach fosters innovation and strengthens continuity in service delivery. Involving vendors in long-term strategy discussions creates stronger bonds and motivates them to deliver beyond the basic contract terms.
Why Are Risk Assessments and Compliance Checks Essential?
Vendor partnerships introduce hidden risks that extend beyond pricing. Financial stability, cybersecurity defenses, and ESG commitments must be assessed regularly. Without proper checks, organizations expose themselves to compliance failures and reputational damage.
The risks are measurable. 61.7% of organizations experienced a cyber incident tied to third-party vendors. Meanwhile, 49% of companies reported that vendors misused confidential data.
Annual audits, ongoing monitoring, and contractual contingency planning reduce these vulnerabilities and ensure regulatory compliance.
How Does Leveraging Technology and Automation Streamline Vendor Management?
Manual processes create delays and errors in vendor oversight. Automation eliminates redundancies by accelerating onboarding, analyzing spend patterns, and flagging risks before they escalate. AI-driven tools score vendor performance against predefined KPIs and reduce the effort required to manage large vendor bases.
Digital transformation is driving adoption. According to MarketsandMarkets, spending on e-sourcing platforms is projected to grow at a 14% CAGR through 2025, reflecting widespread adoption of automation in vendor oversight.
RadiusPoint leverages automation to handle invoice matching, real-time performance dashboards, and predictive monitoring that improve accuracy and save costs.
How Should Organizations Measure and Optimize Vendor Performance?
Performance evaluation ensures vendors remain accountable. Establishing KPIs such as on-time delivery, compliance rate, and cost savings provides a factual basis for renewals and terminations.
Regular reviews are critical. A recent study by ISACA found that 90.9% of organizations now conduct regular assessments of third-party vendors. Quarterly scorecards supported by centralized dashboards drive continuous improvements, allowing procurement leaders to renegotiate contracts with evidence in hand.
Why Segment Vendors Strategically?
Not all vendors deserve equal investment of time and resources. Segmenting suppliers by criticality, financial impact, and strategic value ensures that attention is directed toward those who affect core business outcomes.
The Kraljic Matrix provides a structured method, classifying vendors as strategic, leverage, bottleneck, or transactional. Businesses that segment effectively improve efficiency by building deep partnerships with core vendors while streamlining oversight of low-risk suppliers.
How Does Continuous Training Improve Vendor Management Outcomes?
Even with strong processes in place, employees must stay aligned with best practices. Regular training on negotiation tactics, compliance standards, and technology platforms ensures that procurement teams adapt to evolving risks.
A workforce educated on data privacy laws, ESG frameworks, and automation tools avoids costly errors. Training also improves cross-departmental communication, which remains a common pitfall in vendor oversight.
Why Should Organizations Align Vendor Management with ESG and Sustainability Goals?
Sustainability is now a business requirement rather than a reputation booster. Procurement leaders are expected to evaluate vendors on environmental, social, and governance (ESG) factors alongside pricing and quality.
The shift is evident: 64% of business leaders view third-party risk management as a strategic ESG imperative. By prioritizing ESG-focused vendors, organizations strengthen compliance, attract investors, and appeal to socially conscious customers.
How Do Benchmarking and Analytics Drive Vendor Optimization?
Benchmarking allows businesses to compare vendor performance against industry standards. Analytics go deeper by forecasting vendor-related risks and uncovering cost inefficiencies.
Advanced platforms aggregate supplier data across industries, giving procurement leaders insights into delivery timelines, quality standards, and pricing benchmarks. This data-backed approach identifies gaps that traditional reviews fail to capture.
What Common Pitfalls Should Organizations Avoid in Vendor Management?
Many organizations fall into predictable traps when managing vendors. Over-reliance on low-cost suppliers often leads to hidden risks. Poor communication between internal teams and vendors erodes accountability. Others fail to account for AI biases in vendor scoring models, which introduce unfair or inaccurate assessments.
The consequences are severe. IBM reports that data breaches, many linked to vendor vulnerabilities, cost businesses an average of $4.88 million in 2024, a 10% increase from the prior year. Avoiding these pitfalls requires a balance of strategy, oversight, and technology.
What Benefits Do Organizations Gain from Following Best Practices?
Adopting best practices transforms vendor management from a cost center into a growth driver. Structured negotiations yield 20–30% cost reductions, while centralized monitoring accelerates onboarding and prevents compliance failures.
Evidence supports these outcomes. A PwC survey found that 72% of companies using structured due diligence reduced their financial, legal, and reputational risks significantly. Meanwhile, the vendor risk management market, valued at $13.47 billion in 2025, is projected to grow at 12.12% CAGR, highlighting the critical role of vendor oversight in modern business.
How Does RadiusPoint Simplify Vendor Management for Organizations?
RadiusPoint delivers vendor management solutions designed to reduce costs, strengthen compliance, and improve visibility. By centralizing data, automating performance tracking, and providing detailed spend analysis, RadiusPoint ensures procurement leaders make evidence-driven decisions.
Whether addressing rising inflation, cybersecurity exposure, or sustainability compliance, RadiusPoint’s software and services align with the most pressing challenges of 2025. Businesses that adopt these solutions streamline vendor relationships, cut costs, and safeguard operations against disruptions.
What is Document Management in Healthcare?
Document management in healthcare refers to the structured process of storing, organizing, and securing patient-related information, administrative records, and billing documents in a centralized system.
It eliminates dependence on paper records and fragmented storage practices, allowing healthcare organizations to manage sensitive data efficiently while maintaining compliance with regulatory standards.
Unlike Electronic Health Records (EHR), which focus primarily on patient clinical data, a document management system (DMS) supports a wider range of records, contracts, billing forms, medical images, insurance documentation, and compliance reports.
When integrated with an EHR, a DMS strengthens a hospital or clinic’s ability to unify operations and maintain a single source of truth across departments.
Why is Document Management Important in Healthcare?
Healthcare providers deal with thousands of documents daily, from patient intake forms to regulatory submissions.
Without a structured document management system, staff spend excessive time on administrative tasks, leaving less time for patient interaction.
According to the Annals of Internal Medicine study cited by AMA (American Medical Association), physicians spend 49% of their office hours on EHR and desk work compared to just 27% on direct patient interaction.
In addition, physicians dedicate an average of 1.77 hours outside office hours to documentation, and clinical staff spend nearly 13.5 hours weekly on paperwork—a 25% increase over the past seven years.
Patient safety also suffers when documentation lacks accuracy. Research published by BMJ Quality & Safety found that 25% of patients who reviewed their medical records identified errors, with 10% classified as very serious.
Other industry reports reveal that up to 70% of medical records contain missing or incorrect information. Inaccuracies not only erode patient trust but also increase liability risks for providers.
What Are the Benefits of a Healthcare Document Management System?
A healthcare-focused DMS addresses operational inefficiencies while improving accuracy and compliance. It shortens retrieval times for patient records, reduces duplication, and enables secure sharing across authorized teams.
Financial benefits are also significant. According to Becker’s Hospital Review, medical billing errors cost U.S. providers approximately $125 billion annually. Automating documentation helps reduce this burden by eliminating redundant manual work.
Additionally, IDC research shows that inefficient document management costs organizations $19,732 per information worker per year, making it one of the highest productivity drains in healthcare.
By digitizing processes, organizations also reduce administrative overhead. Data from Health Affairs indicates that administrative tasks account for 25–30% of total healthcare spending in developed countries.
For hospitals and large clinics, even small efficiency gains translate into millions in annual savings.
What Challenges Do Healthcare Providers Face in Document Management?
While the advantages are clear, healthcare providers encounter barriers when transitioning to structured document management. Manual processes remain deeply embedded in many organizations, making the shift toward digitization a cultural and financial challenge.
Paper-based workflows are expensive and time-consuming. Reports from McKinsey & Company estimate that paperwork processing costs the healthcare sector up to $210 billion annually. Beyond costs, human error introduces further risk.
Studies have shown that data inaccuracies in hospitals occur at rates of 26.9%, costing providers up to $20 million annually in billing issues, compliance penalties, and patient mismanagement.
Integration is another challenge. Not all systems communicate seamlessly with existing EHR platforms, leading to fragmented workflows.
Training staff to adopt new tools and enforcing compliance protocols further complicate implementation.
What Are the Different Types of Document Management in Healthcare?
Healthcare organizations adopt different models depending on budget, size, and IT infrastructure. Traditional manual systems rely on physical storage, filing cabinets, and in-person retrieval, which limit scalability.
Hybrid approaches combine paper with digital archives, offering partial flexibility but still requiring significant manual input.
A fully digital-first DMS centralizes records, provides instant access, and enforces data security policies. When integrated with an EHR, the system extends its functionality to include medical imaging, compliance reporting, and billing, giving providers an end-to-end solution for information management.
How Does Digitization Transform Healthcare Document Management?
Digitization is more than scanning and storing records, it creates structured workflows that improve speed, accuracy, and compliance. AI-driven tagging and indexing reduce the time spent searching for files, while cloud-based systems ensure access across multiple facilities without compromising security.
The growth trajectory reflects this shift. According to Future Market Insights, the global medical document management systems market is projected to reach $2.1 billion by 2034, growing at a CAGR of 11.8% from $0.7 billion in 2024.
This trend underscores the urgency for healthcare providers to invest in scalable solutions that align with digital-first strategies.
Why Should Healthcare Providers Use Software Instead of Manual Work?
Relying on manual document handling creates inefficiencies and exposes healthcare providers to compliance risks. Files may be misplaced, data entry errors accumulate, and audits become resource-heavy.
A dedicated document management system reduces these risks through automation, audit trails, and secure storage.
Software also supports organizational growth. As patient volumes rise, manual processes collapse under pressure, while a scalable DMS maintains speed and accuracy without requiring proportional staffing increases.
In an industry where precision and compliance define outcomes, software-driven systems are no longer optional, they are essential.
How Do You Choose the Right Healthcare Document Management Software?
Selecting a document management solution requires careful evaluation of compliance, security, and integration features. At a minimum, the software must meet HIPAA standards, provide encryption, and allow for role-based access control.
Integration with EHR and billing systems is critical for workflow efficiency. Vendor support, customization options, and scalability should also influence the decision.
Compliance risks add further urgency: the U.S. Department of Health & Human Services (OCR) has imposed penalties in 152 HIPAA cases, totaling $144.8 million to date.
In 2024 alone, OCR reported $9.16 million in HIPAA violation settlements. Choosing a vendor with proven compliance expertise protects healthcare organizations from costly exposure.
What Are the Compliance Considerations for Document Management in Healthcare?
Compliance represents one of the most important drivers for implementing a DMS. Patient privacy and data protection requirements under HIPAA and other regional laws demand strict safeguards.
The risks of neglecting compliance are significant.
In 2023, HIPAA Journal reported 725 large healthcare data breaches exposing more than 133 million records. The number surged further in 2024, with 170 million patient records affected, compared to just 6 million in 2010.
The average cost of a healthcare data breach reached $10.22 million in 2025, according to IBM Security’s Cost of a Data Breach Report. These figures highlight why healthcare executives treat compliance as both a financial and reputational priority.
What is the ROI of a Healthcare Document Management System?
A well-implemented DMS delivers measurable ROI by reducing costs, preventing compliance penalties, and increasing staff productivity. Time saved on record retrieval translates directly into more patient-facing hours. Error reduction minimizes financial losses linked to billing disputes.
Market projections further support adoption. Research from Grand View Research shows the medical document management market is expected to grow from $610 million in 2023 to $1.33 billion by 2030. This growth signals that healthcare organizations adopting digital solutions now position themselves ahead of future operational and compliance demands.
What Are the Best Practices for Healthcare Document Management?
Healthcare providers seeking to maximize the benefits of document management should adopt structured best practices. First, prioritize digitization across all departments rather than isolated areas.
Second, ensure seamless integration with EHR systems to unify patient and operational data. Third, enforce strict compliance protocols with regular audits, user training, and access monitoring.
Finally, foster a culture of accountability and continuous improvement. Staff should be trained not only on software use but also on the importance of secure handling, accuracy, and efficiency.
This human element, combined with advanced technology, ensures long-term sustainability.
How Does RadiusPoint Help Healthcare Organizations Improve Document Management?
RadiusPoint delivers healthcare document management solutions designed to reduce inefficiencies, ensure compliance, and enhance scalability.
By integrating with existing EHR systems, RadiusPoint enables hospitals and clinics to automate records handling, billing workflows, and compliance checks in a HIPAA-secure environment.
With over three decades of experience in telecom and IT expense management, RadiusPoint applies proven methodologies to healthcare document management, helping organizations cut costs, reduce errors, and eliminate manual paperwork.
For healthcare executives seeking a compliant, cost-effective, and future-ready document management system, RadiusPoint provides the strategic partner they need.
What CFOs Are Focused on in 2025
 What CFOs Are Focused on in 2025 — And How to Take Strategic Action
What CFOs Are Focused on in 2025 — And How to Take Strategic Action
In today’s unpredictable business landscape, CFOs are under immense pressure to achieve more with fewer resources. Rising operational costs, rapid digital transformation, and increased board scrutiny are forcing finance leaders to rethink how they manage spend, data, and risk. Below are the top priorities for CFOs in 2025—and how RadiusPoint is helping them respond with confidence.
1. Cash Flow and Liquidity Take Center Stage
With capital harder to access and interest rates still elevated, protecting cash flow is a top concern. CFOs are optimizing working capital and eliminating inefficiencies to preserve margins.
RadiusPoint Supports Liquidity:
• Uncovers waste in telecom, utility, and IT spend
• Automates allocations and reporting for improved cash visibility
RadiusPoint’s 30+ years of experience in cost recovery and process automation has helped clients reduce manual processing costs and increase financial control. Traditional invoice processing can cost more than $13 per invoice—and that doesn’t include auditing. RadiusPoint automates the entire process, auditing by line item and flagging discrepancies. Clients have seen returns exceeding 400% annually, with some reaching over 1,000% including a nationwide vision provider saving over $500,000 annually in deregulated energy markets alone.
2. AI & Automation: Progress with Precision
CFOs are modernizing finance operations with automation, but not at the expense of compliance or visibility. The goal: to increase efficiency while maintaining control.
RadiusPoint Delivers:
• Full automation of invoice processing and validation
• Trackable exception handling for audit-readiness
• Improved insights without increasing headcount
For a Fortune 100 company, RadiusPoint automated the allocation of a $1M wireless invoice affecting over 10,000 users—work that previously required six full-time employees. An additional telecom invoice that used to take a month to validate now runs through an automated monthly audit, which uncovered $600K in overcharges. Another client, a national homebuilder, cut utility waste by $25K per month after RadiusPoint streamlined their utility setup and shutdown process.
3. Real-Time Spend Visibility Is a Must
Long reporting cycles don’t cut it in today’s volatile environment. CFOs need immediate access to actionable insights.
RadiusPoint Delivers Real-Time Intelligence:
• Dynamic dashboards and automated reporting tools
• Department, vendor, and location-based spend tracking
• Predictive insights based on historical trends
With ExpenseLogic, RadiusPoint provides one of the industry’s most robust monthly audits. More than just identifying overcharges, RadiusPoint works directly with vendors to recover funds—whether it’s $1.4M in misbilled wireless services or $16K in electricity overcharges due to meter errors. Automation uncovers issues; RadiusPoint’s team ensures recovery.
4. Control Costs Without Cutting Corners
Budget cuts can’t come at the expense of performance. CFOs are looking for savings that don’t hinder innovation or growth.
RadiusPoint Finds Strategic Savings:
• Identifies billing errors and unused services
• Renegotiate contracts and right size services
• Delivers 15–25% average client savings
Clients often lack the staff or expertise to handle detailed vendor disputes. RadiusPoint’s team does this every day—identifying contract lapses, managing expirations, and negotiating based on real utilization data. For example, a global elevator company saw 28% savings (or $180K annually) on waste management across 40 locations after RadiusPoint optimized contracts and removed unnecessary services.
Read more ➝ Waste Services Case Study
5. Support Growth Without Growing Overhead
Finance leaders need systems that scale with the business. Growth should not require proportional increases in back-office headcount.
RadiusPoint Enables Scalable Growth:
• Centralizes procurement and reporting across locations
• Supports expansion without increasing staff
• Provides tailored acquisition and transition services
During one client acquisition, RadiusPoint identified over $2M in unclaimed VAT and recovered it by tracing the invoice chain. This type of integration and support helps clients grow confidently without operational drag.
Read more ➝ Acquisition Support Case Study
6. Compliance, Risk, and ESG Reporting Are Rising in Importance
Whether it’s ESG metrics, fraud prevention, or audit readiness, CFOs must ensure transparency and regulatory compliance across all operations.
RadiusPoint Strengthens Governance:
• Maintains audit trails for every invoice and vendor interaction
• Tracks energy usage for ESG and sustainability reporting
• Mitigates fraud risk through automated controls and alerts
RadiusPoint’s ESG services extract energy data from invoices to produce monthly reports using the correct units (kWh, therms, CCF, etc.), eliminating hundreds of hours of manual effort. One client avoided over 800 man-hours annually using these tools. RadiusPoint also helped uncover $350K in fraudulent wireless purchases at a healthcare company by identifying audit gaps and implementing stricter controls.
Read more ➝ ESG & Fraud Case Studies
Read more ➝ IT Department Fraud Case Study
The Bottom Line
CFOs in 2025 aren’t just financial stewards, they’re strategic decision-makers navigating uncertainty, driving automation, and championing ESG. With RadiusPoint as your partner, you gain clarity, control, and confidence to lead your organization forward. Let RadiusPoint help you drive cost-efficiency and strategic growth in 2025 and beyond.
Contact us today! www.radiuspoint.com or sales@radiuspoint.com
Why is Mobile Device Management Important?
MDM bolsters security by implementing layered defenses, including data encryption to protect information at rest and in transit, remote wipe functionalities to erase compromised devices, and multi-factor authentication to verify user identities.
It addresses compliance by generating audit trails for regulatory audits, restricting data flows to approved regions, and enforcing policies aligned with standards like GDPR or CCPA.
For example, in regulated industries, MDM logs access attempts and flags non-compliant behaviors, helping prevent fines averaging millions per violation.
As data breaches cost an average of $4.4 million globally, with a 10% year-over-year increase, MDM’s role in credential management and vulnerability patching remains critical.
How Does MDM Support Remote Work and BYOD Policies?
By providing location-agnostic tools for device monitoring, software distribution, and troubleshooting, ensuring employees remain productive without on-site IT intervention.
In BYOD scenarios, it creates virtual containers to segregate corporate data from personal files, applying selective policies like mandatory VPN usage for work apps while preserving user privacy.
This separation mitigates risks from unmanaged devices, where 80% of BYOD instances expose organizations to hackers through vulnerabilities like outdated OS or rogue applications.
Post-pandemic, MDM has adapted to hybrid models, with features like geofencing to enforce location-based restrictions, fostering secure flexibility for global teams.
What Business Value Does MDM Provide?
MDM generates business value through operational efficiencies, such as automating onboarding to save up to 6 hours per new employee via pre-configured profiles and app deployments.
It drives cost savings by optimizing resource allocation, reducing hardware replacement needs through predictive maintenance, and minimizing shipping expenses by $80 per hire in remote setups.
Productivity benefits arise from uninterrupted access to enterprise tools, with 90% of organizations noting smoother BYOD integration, leading to fewer disruptions.
Overall, MDM contributes to ROI by lowering breach-related losses and scaling with business growth, particularly in cloud-deployed models that adapt to fluctuating device counts.
What is the Difference Between MDM and Enterprise Mobility Management (EMM)?
MDM concentrates on device-centric operations, such as hardware configuration, location tracking, and basic security enforcement across mobile devices.
EMM extends beyond devices to encompass application lifecycle management, secure content distribution, and identity-based access controls, creating a holistic mobility ecosystem.
For instance, while MDM might enforce password policies on a smartphone, EMM would additionally manage app stores, blacklist unauthorized software, and integrate with single sign-on systems for seamless user experiences.
How Does MDM Compare to Unified Endpoint Management (UEM)?
MDM is specialized for mobile platforms, handling OS-specific features like Android Enterprise or Apple DEP for enrollment and policy application.
UEM consolidates management across all endpoints: mobiles, desktops, servers, and IoT, via a unified console, incorporating advanced analytics for cross-device insights and threat correlation.
UEM evolves MDM by addressing silos, where multiple tools previously led to overhead, now offering integrated dashboards for 90% of IT teams seeking help desk improvements.
When Should Businesses Choose MDM Over EMM or UEM?
Select MDM for organizations with predominantly mobile fleets requiring cost-effective, focused security without broader infrastructure needs, suitable for startups or small teams.
Opt for EMM when mobility strategies involve intricate app ecosystems and content security, ideal for enterprises with heavy reliance on custom mobile applications.
Choose UEM for diverse environments mixing mobiles with traditional endpoints, where unified visibility prevents management fragmentation and supports scalability in large-scale deployments.
Use the following table for a quick comparison:
| Aspect | MDM | EMM | UEM |
| Scope | Mobile devices only | Mobility, including devices, apps, and content | All endpoints (mobile, desktop, IoT, servers) |
| Key Features | Policy enforcement, tracking, and remote actions | App management, identity verification, and content security | Cross-platform analytics, unified policies, and threat correlation |
| Ideal Use Case | Mobile-focused security for SMEs | Comprehensive mobility in app-heavy enterprises | Integrated management in mixed-endpoint setups |
| Complexity | Low to medium | Medium to high | High |
What architecture an MDM System?
MDM architecture comprises a central management console, often cloud-hosted, that interfaces with device agents or built-in OS APIs for command execution.
It includes backend databases for storing device inventories, compliance logs, and user profiles, connected via secure protocols like HTTPS.
Integration layers link to directory services (e.g., Active Directory) for authentication and to cloud providers for OTA pushes, ensuring resilient communication even in low-bandwidth scenarios.
As of 2025, architectures incorporate edge nodes for localized processing, reducing dependency on central servers for faster responses.
How Does MDM Handle Monitoring and Tracking?
MDM conducts monitoring by collecting telemetry data on device status, including CPU usage, storage levels, and connectivity health, visualized in dashboards for IT oversight.
Tracking involves GPS or Wi-Fi-based location services to pinpoint devices, with alerts for geofence breaches or unusual patterns indicating theft.
It maintains historical logs for forensic analysis, ensuring non-intrusive observation that complies with privacy laws, while integrating AI to predict failures based on usage trends.
What Policies Can Be Enforced Through MDM?
MDM enforces policies ranging from authentication requirements, like biometric locks or complex passwords, to network controls such as automatic VPN activation on public Wi-Fi.
It manages content filters to block malicious sites, app allowlists to permit only vetted software, and data usage caps to prevent overages.
Policies can be role-based, applying stricter rules to sensitive positions, and dynamically updated via push notifications for immediate effect.
What Remote Actions Are Possible with MDM?
Remote actions encompass locking screens to prevent access, selective or full data wipes to protect information on lost devices, and software installations for urgent patches.
Admins can execute password resets, factory resets, or app uninstalls over-the-air, with auditing to track action histories.
In advanced setups, actions include quarantining devices during threats or forcing reboots for maintenance, all executed securely to minimize user disruption.
How Does MDM Enhance Security and Protect Data?
MDM enhances security through proactive measures like real-time threat scanning, encryption of stored data, and automatic updates to patch vulnerabilities.
It protects data with containerization in BYOD, isolating breaches, and features like remote attestation to verify device integrity.
With 74% of IT leaders reporting mobile-related breaches, MDM reduces exposure by enforcing zero-trust principles, where access is continually validated.
What Efficiency and Productivity Gains Come from MDM?
Efficiency gains stem from automation of routine tasks, such as bulk provisioning for new hires or scheduled backups, freeing IT for strategic roles.
Productivity increases as users experience minimal interruptions, with quick app access and reduced downtime from enforced optimizations like battery management policies.
In practice, this translates to faster workflows, especially in field operations where devices stay operational longer.
How Can MDM Lead to Cost Reductions?
MDM achieves cost reductions by tracking assets to recover lost devices, extending lifespans through usage monitoring, and consolidating tools to avoid redundant licensing.
Cloud models, with 56.5% adoption, eliminate on-premise hardware expenses, while predictive analytics prevent costly failures.
For SMEs, this means lower IT staffing needs and breach mitigation, potentially saving thousands annually.
In What Ways Does MDM Ensure Compliance and Scalability?
MDM ensures compliance via automated reporting on policy adherence, geo-restrictions for data sovereignty, and integration with compliance frameworks for audits.
Scalability is achieved through elastic cloud resources that handle device surges without infrastructure upgrades, supporting growth from hundreds to thousands of endpoints.
This adaptability is key in dynamic industries, where regulatory changes demand swift policy adjustments.
How Does MDM Improve Remote Management and Application Control?
Remote management improves with OTA capabilities for updates and diagnostics, enabling global oversight without travel.
Application control involves curating repositories, blocking shadow IT, and pushing updates to ensure version consistency, reducing compatibility issues.
This control extends to monitoring app performance, optimizing for enterprise needs like secure collaboration tools.
What Privacy Concerns Arise in BYOD Setups?
Privacy concerns in BYOD include potential overreach into personal data during monitoring, such as accessing non-work apps or location history outside business hours.
Employees may fear surveillance eroding trust, necessitating transparent consent mechanisms and data segmentation to limit corporate visibility.
Balancing enforcement with privacy requires policies that delete personal logs upon separation, addressing 67% of executives’ challenges in usability-compliance trade-offs.
Why Do Implementation Costs Limit Adoption for SMEs?
Implementation costs encompass software licensing, integration consulting, ongoing maintenance, and training, often exceeding SME budgets and delaying ROI.
Fortune Business Insights highlights how these expenses—installation and updates—hinder adoption, especially with cloud migrations requiring upfront investments.
SMEs face compounded issues from scalability fees as device counts grow, restricting access to advanced features.
What Security Risks Persist Despite MDM?
Persistent risks include sophisticated attacks exploiting zero-day vulnerabilities or social engineering bypassing policies, like phishing on managed apps.
BYOD amplifies threats from mixed personal-corporate usage, with corrupt passwords or illegal apps creating entry points.
Even with MDM, 74% of breaches stem from mobile issues, underscoring the need for continuous updates and user education.
How Do Limited IT Resources Affect MDM in SMEs?
Limited IT resources in SMEs result in inadequate policy customization, leading to misconfigurations and exposure.
Grand View Research notes challenges in protection due to budget constraints, causing silos and overhead from multiple systems.
This resource scarcity delays threat responses, with 90% of teams requiring help desk upgrades to manage complexities.
What Common Issues Do IT Leaders Face with MDM Providers?
IT leaders encounter rollout delays for new services (42%), escalating remote work costs (41%), and general management hurdles (39%), per dissatisfaction rates of 72%.
Providers often lack seamless integrations, leading to compatibility issues with legacy systems.
Additional pain points include vendor lock-in and insufficient customization, amplifying operational friction in fast-evolving environments.
What Do IT Administrators and Managers Prioritize in MDM?
IT administrators prioritize intuitive interfaces for policy deployment, robust integrations with existing tools, and scalability to handle device diversity.
Representing 70.8% of adoption, they emphasize support for OS like Android (58% share), focusing on features for enrollment efficiency and real-time alerts to streamline daily operations.
How Do CIOs and C-Suite Executives View MDM?
CIOs assess MDM on metrics like ROI from reduced breaches, compliance assurance, and risk reduction, with 64% emphasizing data privacy in hybrid setups.
They navigate provider shortcomings reported by 72%, viewing MDM as a strategic investment for long-term agility and cost control in executive decision-making.
What Focus Areas Do Security Officers and Compliance Teams Have?
Security officers target threat mitigation through AI-enhanced detection and regulatory tools for sectors like healthcare, which holds the largest market share.
Compliance teams focus on audit-ready logs and policy automation to balance controls with usability, addressing challenges in high-stakes environments where breaches carry severe repercussions.
How Do Industry-Specific Personas Benefit from MDM?
Industry personas, such as finance managers handling sensitive transactions, benefit from encrypted communications and audit trails.
Government officials gain from secure data handling in regulated operations, while retail supervisors use tracking for inventory devices.
SMEs, with 39% noting management issues, leverage cloud MDM for affordable, scalable security without large IT teams.
What Geographic and Demographic Nuances Influence MDM Adoption?
North America leads with a 38.6% share in 2024, driven by infrastructure upgrades and compliance demands among US IT professionals and business owners.
Asia-Pacific exhibits the fastest growth via urbanization and BYOD in emerging markets like India.
Demographic factors include targeting tech-savvy managers in urban areas, with nuances like language support and regional regulations shaping adoption patterns.
How Does MDM Address High Implementation Costs?
MDM counters high costs with tiered pricing models and cloud options that shift from capex to opex, reducing initial outlays.
It streamlines integration via pre-built APIs, minimizing consulting needs, and offers free trials for proof-of-concept to justify expenses.
What Solutions Does MDM Offer for BYOD Security Risks?
MDM provides containerization to isolate risks, enforces authentication to combat poor passwords, and app scanning to block illicit software.
By managing 80% unmanaged devices, it prevents breaches through remote controls and compliance checks.
How Can MDM Help SMEs with Limited Resources?
MDM assists SMEs by automating security tasks, requiring minimal staff oversight, and offering affordable SaaS models.
It delivers turnkey solutions for protection, enabling resource-strapped teams to focus on core business without extensive expertise.
What Improvements Does MDM Bring to Mobile Help Desks?
MDM unifies platforms to eliminate silos from 2-3 UEM systems, providing centralized ticketing and remote diagnostics for quicker resolutions.
This addresses 90% of IT teams’ needs for enhanced support, reducing overhead through self-service portals.
How Does MDM Mitigate Data Breaches and Unmanaged Devices?
MDM mitigates breaches costing $4.4 million on average by strengthening credentials, deploying wipes, and monitoring for anomalies.
It enrolls unmanaged devices systematically, applying policies to close exposure gaps.
What are the Current Projections for the Global MDM Market?
As of 2025, the global MDM market stands at approximately USD 9.49 billion to USD 15.75 billion, based on varying reports from key analysts.
This reflects growth from USD 7.67 billion to USD 12.15 billion in 2024, driven by increased enterprise investments.
How is the MDM Market Expected to Grow Through 2030 and Beyond?
Projections indicate growth to USD 28.37 billion by 2030 at a CAGR of 24.5%, extending to USD 81.72 billion by 2032 with a 26.5% CAGR.
Earlier estimates like USD 22.0 billion by 2027 align with this upward trajectory, updated for 2025 realities.
What Factors are Driving MDM Market Expansion?
Driving factors include remote work proliferation, BYOD policies enhancing productivity, and security demands amid rising breaches.
Cloud adoption at over 58% facilitates scalability, while regional growth in Asia-Pacific via urbanization and North America’s dominance propel the market.
What Steps are Involved in Choosing an MDM Provider?
Begin by assessing business needs, including device types, user count, and security priorities.
Research providers for features like ease of use and pricing, reviewing case studies, and demos.
Conduct trials to test compatibility, then negotiate contracts focusing on support SLAs and scalability options.
How to Enroll Devices and Configure Policies?
Enroll devices using methods like QR scanning, email invitations, or zero-touch for bulk setups, linking to the MDM server.
Configure policies in the admin console by defining rules for passwords, apps, and networks, then deploy profiles and verify through device testing for compliance.
What Best Practices Ensure Successful MDM Implementation?
Adopt phased rollouts starting with pilot groups, provide user training on policies, and establish feedback loops for adjustments.
Regularly audit configurations, integrate with backups, and update software to maintain security, ensuring alignment with business goals.
How to Balance Usability and Security in Setup?
Balance by implementing flexible policies, such as conditional access based on context, and soliciting user input to avoid overly restrictive rules.
Use analytics to monitor impacts on productivity, refining settings to enforce essentials like encryption without hindering daily tasks.
What Cloud Platforms Support MDM Integration?
AWS supports MDM with services like Amazon WorkSpaces for secure access, Google Cloud via Endpoint Manager for Android focus, and Azure through Microsoft Intune for hybrid integrations.
These platforms enable OTA management, API-driven customizations, and scalable storage for logs.
Which MDM Tools are Best for Different Operating Systems?
For Android, Google Endpoint Management offers native integration with enterprise features; iOS benefits from Jamf or Apple Business Manager for DEP enrollment.
Cross-OS tools like Microsoft Intune or VMware Workspace ONE provide unified support, handling Windows and macOS alongside mobiles.
How to Evaluate MDM Solutions Based on Features and Scalability?
Evaluate by scoring features like AI analytics, integration depth, and mobile threat defense.
Assess scalability through trial expansions, checking performance under load, and cost per device.
Prioritize vendors with strong SLAs, user reviews, and future-proofing like IoT compatibility.
What Role Do Open-Source or Free MDM Options Play?
Open-source tools like Flyve MDM deliver basic enrollment and policy enforcement at no cost, ideal for SMEs testing the waters.
Free tiers from commercial providers, such as Intune’s entry level, offer limited devices with upgrades for advanced needs, serving as gateways to full solutions.
How Will AI Transform MDM for Threat Detection and Automation?
AI will revolutionize MDM by enabling predictive threat detection through behavioral analysis, automating responses like quarantines, and customizing policies via machine learning.
Self-healing mechanisms will repair configurations in real-time, reducing manual interventions and enhancing efficiency in dynamic environments.
What Impact Will IoT Integration Have on MDM?
IoT integration will broaden MDM to manage sensors, wearables, and smart devices alongside mobiles, unifying security protocols for interconnected ecosystems.
This enables centralized oversight of endpoint diversity, with 75 billion IoT devices projected by 2025, improving data flows and resilience.
How is Zero Trust Architecture Shaping MDM?
Zero Trust shapes MDM by mandating continuous authentication and micro-segmentation, verifying every access request regardless of location.
It incorporates device attestation and AI-driven defenses, fortifying against insider threats in IoT-heavy environments.
What Role Will Blockchain and Predictive Analytics Play?
Blockchain will secure identity management with decentralized ledgers for tamper-proof authentication, while predictive analytics forecasts vulnerabilities using historical data.
Together, they enable proactive policy adjustments, minimizing risks in distributed systems.
How Will Edge Computing and 6G Influence MDM?
Edge computing will decentralize processing for low-latency decisions, like on-device threat scans, while 6G will support ultra-fast connectivity for seamless OTA updates.
This duo facilitates hyper-automation and real-time maintenance in mobile-heavy environments.
What Emerging Trends in Endpoint Diversity and User-Centric Management to Expect?
Expect trends in managing AR/VR headsets and wearables (55.8% smartphone dominance persisting), with user-centric designs prioritizing intuitive interfaces and privacy controls.
This shift balances security with experience, incorporating feedback-driven approaches.
How Might Quantum Computing Redefine MDM Encryption?
Quantum computing threatens current encryption, prompting MDM to adopt post-quantum algorithms for resilient data protection.
It will redefine standards with quantum-resistant keys, ensuring long-term security against advanced decryption.
What Collaborative Governance Models are Forecasted for MDM Policies?
Collaborative models will involve multidisciplinary teams—IT, security, legal—for policy development, ensuring holistic alignment.
Cross-functional input will foster adaptive frameworks, integrating stakeholder views for equitable, effective governance in evolving landscapes.
Detailed Guide on IT Asset Management for Enterprises & SMBs
IT asset management (ITAM) is the practice of systematically tracking, maintaining, and optimizing an organization’s IT assets, including hardware like servers and laptops, software licenses, cloud services, and related resources, from acquisition through disposal.
This involves documenting asset details, monitoring usage to ensure efficiency, controlling costs by preventing redundancies, and aligning resources with business needs to support operations while minimizing risks such as compliance violations or security gaps.
Purpose of IT Asset Management
ITAM serves to catalog every IT asset within a company, including details on their current location, operational status, and how they contribute to daily workflows.
By managing the full lifecycle, from initial purchase or lease to ongoing updates and eventual retirement, this approach aligns technology investments with broader business objectives.
It also mitigates potential issues like software license violations or hardware obsolescence, while fostering better resource allocation to support growth and efficiency.
Core Objectives
- Maintain accurate inventory records for all IT items.
- Optimize asset performance to meet business needs.
- Minimize financial waste through efficient procurement.
- Ensure regulatory adherence during asset handling.
- Facilitate smooth transitions in asset ownership or retirement.
Why IT Asset Management is Essential
Without proper tracking, assets can become lost, underutilized, or vulnerable, leading to unnecessary financial drains and operational disruptions.
ITAM delivers clear visibility that aids in budgeting, prevents compliance failures during regulatory audits, and strengthens overall security by identifying unmanaged devices that could serve as breach points.
For IT managers and executives in mid-sized firms, it becomes a critical tool for maintaining service reliability and adapting to events like mergers or cloud shifts.
Common Challenges Without ITAM
- Hidden costs from duplicate purchases or idle resources.
- Increased vulnerability to cyber threats due to unknown assets.
- Difficulty in scaling IT infrastructure during growth phases.
- Potential fines for non-compliance with licensing rules.
- Inefficient resource allocation is affecting team productivity.
The market is projected to reach USD 13968.6 million by 2032, with a compound annual growth rate (CAGR) of 8.22% from 2024 to 2032 (Source). Increasing focus on cost optimization and compliance with IT standards like ITIL and ISO 55001 drives adoption.
Key Benefits of IT Asset Management
Effective ITAM will reduce overall IT spending by 20-30% through improved asset utilization and elimination of redundant purchases.
It enhances operational efficiency by enabling precise allocation of resources based on real-time data, which in turn supports proactive decision-making via analytics on usage patterns.
Financial Advantages
- Identifies underutilized assets for reallocation or decommissioning.
- Optimizes software licensing to prevent over-purchasing.
- Provides data for accurate budgeting and forecasting.
Operational Improvements
- Centralizes asset information for quick access by teams.
- Reduces manual tracking errors with automated tools.
- Enhances collaboration between IT and finance departments.
Risk Mitigation
- Tracks vulnerabilities to prioritize security patches.
- Ensures all assets meet compliance standards.
- Supports faster recovery during incidents or outages.
According to a survey, half of respondents (46%) say that their ITAM teams now report directly to the CIO or CTO, up from 40% last year and 22% the year prior.
Types of IT Asset Management
ITAM encompasses several specialized categories, each tailored to different aspects of an organization’s technology ecosystem.
Hardware asset management deals with tangible items such as servers, desktops, and peripherals, focusing on their physical condition and deployment.
Software asset management involves overseeing licenses, installations, and usage rights to ensure legal compliance and avoid overpayments.
Here are the four types of this management:
Hardware
- Manages physical items such as desktops, printers, and networking equipment.
- Tracks depreciation, warranties, and physical locations.
- Ensures proper maintenance to extend device usability.
Software
- Monitors installations, versions, and license compliance.
- Prevents unauthorized software usage.
- Handles updates and renewals for optimal performance.
Cloud
- Oversees virtual machines, storage, and SaaS subscriptions.
- Tracks usage in multi-cloud setups.
- Optimizes costs by scaling resources based on demand.
Other Specialized Types
- Mobile management for devices like smartphones and tablets.
- Fixed management for long-term infrastructure like data centers.
- Data management for protecting sensitive information assets.
Processes and Steps in IT Asset Management
ITAM process begins with asset discovery, where automated tools scan networks and systems to compile an initial inventory of all hardware and software present.
Following this, acquisition involves evaluating needs, selecting vendors, and procuring items while documenting costs and terms.
Step 1: Asset Discovery and Inventory
- Use scanning tools to detect all connected devices and software.
- Categorize assets by type, location, and ownership.
- Create a baseline inventory for ongoing reference.
Step 2: Acquisition and Procurement
- Assess needs based on business requirements.
- Evaluate vendors for cost, quality, and support.
- Document purchases with contracts and warranties.
Step 3: Deployment and Configuration
- Assign assets to users or departments.
- Set up configurations and access controls.
- Train users on proper handling.
Step 4: Maintenance and Monitoring
- Schedule regular updates and repairs.
- Track performance metrics like uptime.
- Monitor for compliance and security issues.
Step 5: Retirement and Disposal
- Identify end-of-life assets.
- Secure data wiping and environmentally safe recycling.
- Update records to remove retired items.
Regular audits interspersed throughout ensure data accuracy, and integration with other systems like procurement keeps everything synchronized.
Basic IT Asset Management Framework
A foundational ITAM framework starts with establishing clear policies that outline responsibilities, such as designating asset custodians and defining usage guidelines.
It incorporates inventory tools to centralize data collection and employs standardized processes for handling requests, approvals, and changes.
Reporting features generate insights on asset performance, while alignment with broader IT service management ensures consistency across operations.
Annual reviews allow for refinements based on evolving needs, providing a scalable base for organizations just starting.
Key Components of the Framework
- Policies outlining asset handling rules.
- Roles assign responsibility to specific teams.
- Tools for automation and real-time updates.
- Processes for lifecycle stages.
- Metrics to measure effectiveness.
Building a Successful IT Asset Management Framework (With Examples)
To construct a robust ITAM framework, begin by conducting a thorough assessment of existing assets to pinpoint inaccuracies or gaps in current tracking methods. Select automation tools that facilitate real-time discovery and integrate seamlessly with other enterprise systems for streamlined data flow.
- Train employees on adherence to processes, emphasizing the importance of accurate reporting to build a culture of accountability.
- For instance, a mid-sized manufacturing company adopted barcode scanning for hardware tracking, which decreased asset losses by 15% within the first year by enabling quick location checks.
- Set measurable key performance indicators, such as asset utilization rates above 80%, to gauge effectiveness and guide improvements.
- Another example involves a financial services firm that performed regular software audits, reclaiming unused licenses and achieving annual savings of $50,000 through renegotiated contracts.
- Implement dashboards for visual monitoring, allowing stakeholders to spot trends and make data-driven adjustments promptly.
Continuous feedback loops refine the framework, ensuring it adapts to organizational changes like remote work expansions.
IT Asset Management’s Role in Cybersecurity
ITAM plays a pivotal role in cybersecurity by maintaining an up-to-date inventory of all network-connected devices, which helps identify and isolate potential weak points before threats exploit them.
It ensures that security patches are applied across assets promptly, reducing exposure to known vulnerabilities.
Enhances Security
- Provides complete visibility of all assets, including shadow IT.
- Prioritizes patching based on asset criticality.
- Integrates with vulnerability scanners for proactive alerts.
Addressing Common Risks
- Reduces exposure from unknown devices connecting to networks.
- Ensures compliance with security standards like NIST.
- Supports forensic analysis during breaches.
Cybersecurity asset management continuously discovers, inventories, and monitors assets to protect against threats.
IT Asset Management in Managing Cloud Resources
In cloud environments, it extends to overseeing dynamic resources such as virtual machines, containers, and storage instances, providing visibility into usage patterns that fluctuate with demand.
It curbs unauthorized “shadow IT” deployments by enforcing approval workflows and monitors subscription costs to avoid bill surprises.
- Tools integrated with cloud APIs enable real-time tracking, optimizing allocations through features like auto-scaling that adjust resources automatically.
- For multi-cloud setups, ITAM consolidates data from various providers, ensuring consistent governance across platforms.
- Compliance is maintained by logging configurations and access, which is crucial for audits in regulated industries.
- An example is a tech startup using ITAM to detect idle cloud instances, reallocating them to save on monthly expenses.
This approach ensures cloud investments remain efficient and secure amid rapid scalability.
Best Practices for IT Asset Management
To maximize ITAM effectiveness, centralize all asset information in a single, accessible repository that updates automatically to reflect changes.
Automate discovery processes to minimize manual errors and conduct audits at regular intervals, such as quarterly, to validate data integrity.
Implementation Tips
- Start with a clear strategy defining assets and goals.
- Use automation to eliminate manual errors.
- Prioritize high-value assets for monitoring.
- Foster cross-department collaboration.
- Review and update practices annually.
Advanced Practices
- Leverage AI for predictive maintenance.
- Integrate with ITSM for seamless operations.
- Focus on sustainability in disposal processes.
ITAM vs. CMDB: Key Differences
While ITAM concentrates on the financial and lifecycle management of assets, including ownership and cost optimization, a Configuration Management Database (CMDB) prioritizes mapping out configurations and interdependencies among IT components.
ITAM ensures compliance and tracks expenditures, whereas CMDB facilitates faster incident resolution by highlighting how changes in one area affect others.
Both tools complement each other, with ITAM often feeding essential data into the CMDB for a holistic view of the IT landscape.
Comparison Table
|
Aspect |
ITAM | CMDB |
| Focus | Lifecycle, costs, ownership | Configurations, relationships |
| Primary Use | Cost optimization, compliance | Incident management, changes |
| Data Scope | All assets |
Configuration items only |
ITAD vs. ITAM vs. ITSM: Understanding the Distinctions
IT Asset Disposal (ITAD) specializes in the end-of-life phase, focusing on environmentally responsible recycling, data sanitization, and resale of obsolete equipment.
In contrast, ITAM encompasses the entire asset journey from start to finish, incorporating ITAD as one of its processes.
IT Service Management (ITSM) centers on delivering and supporting IT services to users, relying on ITAM data for resource planning and issue resolution.
Together, they form an interconnected ecosystem where ITAM optimizes assets to fuel ITSM’s service goals, and ITAD ensures safe closures.
Key Distinctions
- ITAD: End-of-life handling, secure erasure, environmental compliance.
- ITAM: Full cycle from acquisition to retirement.
- ITSM: Service-oriented, using assets to deliver IT services.
ITAM provides foundational data for ITSM, while ITAD handles the final stage.
ISO Standards Related to IT Asset Management
ISO 19770 applies to software asset management as it outlines processes for licensing. ISO 55001 covers general asset management and emphasizes risk and value.
Achieving certification to these standards demonstrates a commitment to best practices, leading to improved processes and stakeholder confidence.
Lastly, ISO 19770-1 defines management systems, and its compliance improves efficiency.
Relevant Standards
- ISO/IEC 19770-1: Requirements for ITAM systems.
- ISO 55000: Vocabulary and overview for asset management.
- ISO 55002: Guidelines for applying ISO 55001.
These standards promote structured approaches to maximize asset value.
How to Choose the Right ITAM Software
When selecting ITAM software, first evaluate your organization’s scale and specific requirements, such as handling hybrid environments or high-volume transactions.
Prioritize solutions with strong automation capabilities for asset discovery and lifecycle tracking to save time on manual tasks.
- Ensure compatibility with existing tools like ERP or helpdesk systems for smooth data exchange.
- Opt for intuitive user interfaces that require minimal training, enhancing adoption rates.
- Verify robust security features, including encryption and role-based access, to safeguard sensitive information.
- Compare costs against projected benefits, factoring in implementation and ongoing support fees.
- Review case studies or user feedback from peers in similar industries to gauge reliability.
- Request trial periods or demos to test functionality in your real-world scenarios.
This methodical selection process leads to a tool that truly fits your needs.
Courses and Resources to Learn or Improve IT Asset Management Skills
Several structured programs exist to build expertise in ITAM. IAITAM’s Certified Asset Management Professional (CAMP) covers foundational concepts, processes, and practical applications for managing hardware and software.
Udemy offers a dedicated Hardware IT Asset Management course that dives into tracking physical devices and inventory techniques.
- ITIL 4 Practitioner: IT Asset Management from Learning Tree emphasizes lifecycle management within service frameworks.
- APMG International provides IAITAM certifications that incorporate emerging elements like AI in asset optimization.
- Online resources, such as blogs from InvGate or Virima, compile lists of top certifications and free guides for self-paced learning.
These options cater to both beginners and professionals seeking advanced skills.
Online Resources
- Blogs from InvGate and Virima for guides.
- Udemy and Learning Tree for self-paced learning.
- APMG and Axelos for exam preparation.
Upcoming Trends in IT Asset Management
AI-driven automation is streamlining asset tracking and predictive maintenance, allowing systems to anticipate failures before they occur. Sustainability initiatives are emphasizing reverse logistics, where disposed assets are refurbished or recycled to minimize environmental impact.
- Hybrid IT setups demand advanced analytics for managing on-premises and cloud resources cohesively.
- Tighter cybersecurity integration is becoming standard, with ITAM tools embedding threat detection features.
- Market growth projections indicate the sector reaching USD 2.09 billion by 2025, driven by a CAGR of 6.32% through 2030.
- Collaborations between ITAM and FinOps are rising to optimize cloud spending amid economic pressures.
- Reports highlight challenges like maintaining visibility in complex environments and pushing for more intuitive dashboards.
Emerging Technologies
- AI for predictive analytics and anomaly detection.
- Blockchain for secure asset records.
- IoT sensors for real-time location tracking.
Industry Shifts
- Greater focus on sustainable disposal and recycling.
- Integration with FinOps for cost management.
- Adoption of zero-trust in asset security.
These trends signal a shift toward more intelligent, integrated ITAM strategies.
How RadiusPoint Solves ITAM Challenges as the Best Software Solution
RadiusPoint delivers a comprehensive expense management solution through its software, ExpenseLogic. It excels in addressing IT asset management needs by providing robust tools for tracking, optimizing, and securing assets across telecom, mobility, and utility domains.
This web-based platform stands out for maintaining detailed asset inventories, enabling organizations to gain full visibility into hardware, software, and related resources while automating processes that traditionally lead to inefficiencies and oversights.
With features tailored for mid-sized to enterprise-level companies, it integrates seamlessly with cloud environments, supporting SaaS in fintech and cloud spend management to prevent shadow IT and ensure scalable resource allocation.
By tackling spiraling IT costs through proactive audits and analytics, RadiusPoint empowers IT managers to reclaim control over assets and foster better decision-making.
It allows for adaptation to dynamic business environments, making it a top choice for resolving common ITAM pain points in industries like healthcare, manufacturing, and education.
Request a demo to see how RadiusPoint works.
A Detailed Guide on Invoice Auditing for SMBs & Enterprises
In business operations, especially in accounts payable (AP) and procurement departments, invoice audits are not just a financial safeguard—they directly impact cost recovery, fraud prevention, and operational efficiency.
The process typically examines pricing, quantities, tax, delivery terms, and matching with purchase orders or service contracts.
While often confused with invoice reconciliation, which matches invoices against POs and receipts for processing, invoice auditing is broader.
It focuses on identifying systemic billing issues, pricing discrepancies, overcharges, and potential fraud.
Invoice audits play a vital role in Telecom Expense Management (TEM) programs, where recurring billing errors across vendors are common.
Manual audits rely heavily on spreadsheets and manual review, which increases the risk of errors. Automated systems, by contrast, streamline validation against historical benchmarks and contract terms, reducing inaccuracies and uncovering hidden cost leakages.
Why is invoice auditing critical for finance and procurement teams?
Invoice audits have become indispensable due to the rise in invoice volumes, complex supplier relationships, and heightened fraud risk.
According to a report by Basware, businesses lose an average of 5% of revenue to fraud annually, with billing fraud being the most common. Finance teams need preventive controls to avoid such losses.
Compliance requirements, especially in industries with regulatory oversight, have made audit trails mandatory. When internal controls are weak or manual processes dominate, errors go unchecked, increasing exposure to penalties and financial discrepancies.
The complexity grows with volume. Month-over-month invoice volume spikes of 300% or more are often a red flag for error or fraud.
With expanding supplier networks and multi-vendor relationships, continuous auditing helps businesses maintain oversight without overwhelming staff.
What are the most common issues identified during an invoice audit?
Invoice audits frequently uncover overpayments, duplicate payments, pricing errors, and quantity mismatches. Approximately 5–10% of company profits are lost to payment errors like overcharges. These losses accumulate silently unless actively identified and recovered.
One of the most persistent issues is invoice duplication. A study reported that 2% of AP invoices are paid more than once, costing millions in unnecessary outflows for mid-sized and large organizations.
Quantity discrepancies make up about 12% of all invoice errors, often caused by misalignment between delivery documentation and the invoiced amounts. Errors like these lead to inflated payables and distorted inventory or cost reports.
Data entry mistakes also contribute significantly. Around 73% of invoices contain at least one pricing or calculation error, according to Resolve Pay.
Manual data entry remains a weak link, creating exceptions and increasing downstream reconciliation time.
How do invoice audits help with cost recovery and fraud detection?
A well-executed audit supports both cost recovery and internal fraud monitoring. By identifying billing anomalies, companies recover capital that would have otherwise remained unreclaimed. Research shows that audits recover roughly $1 million for every $1 billion in supplier spend.
Fraud detection is another strategic benefit. ResearchGate highlights that internal audits are the second most effective method to uncover fraud, behind only whistleblower reports. These audits, especially when supported by automation, surface inconsistencies in vendor behavior, irregular charges, and suspicious activity.
Continuous auditing models, adopted by large enterprises, ensure ongoing visibility and eliminate the need for retrospective correction. Real-time alerts for anomalies empower AP managers to take immediate action, protecting liquidity and trust in supplier relationships.
What is the checklist for conducting an effective invoice audit?
Before beginning the audit process, organizations must ensure access to clean, centralized invoice data. Cross-referencing invoice line items against purchase orders, vendor contracts, and receiving reports is the foundation of an accurate audit.
Reviewing invoices for pricing accuracy, appropriate taxation, freight charges, and line-item discrepancies is essential. Flagging unusual payment terms or surcharges also improves the thoroughness of the audit.
Teams should also validate if any line items were previously paid or fall outside the contract scope. A comprehensive audit includes validating quantities delivered, verifying account coding, and tracing invoice trails within the ERP or cloud finance system.
Documentation is critical. All findings should be recorded with contextual notes, flagged for vendor dispute or correction, and structured for compliance review. This level of diligence forms the basis of a defensible audit trail.
What’s the best way to report and document invoice audit findings?
Audit findings should be compiled into a structured report that communicates the scope, issues uncovered, and financial impact. Reports should outline both recoverable amounts and process issues.
Automated platforms help generate audit logs, highlight repeat offenders, and benchmark vendor performance. Dashboards assist in visualizing trends, like high exception rates or recurring late fees, that may not be evident in static data sets.
Reports should also provide remediation recommendations, including adjustments to procurement processes, tighter vendor controls, and automation enhancements. These insights guide CFOs and controllers in adjusting internal financial controls and workflows.
What are the pitfalls to avoid in invoice audits?
One of the biggest pitfalls is relying too heavily on manual reviews. According to a newly published study, manual invoice processing can take over 10 days per invoice and cost nearly $10 per document. This slows audits and makes the detection of inconsistencies harder.
Another common mistake is treating minor errors as negligible. Even small overcharges across hundreds of vendors can result in significant annual leakage. Without a defined audit schedule, errors go unnoticed until year-end or beyond.
Failure to integrate the audit process with ERP or spend management platforms also weakens control. It restricts audit trail accuracy, increases duplication, and reduces the ability to generate meaningful insights.
How does manual invoice auditing compare to automated methods?
Automated audits outperform manual efforts in scale, speed, and accuracy. With manual processes, AP professionals process around 6,082 invoices annually. Automated workflows raise this capacity to 23,333 invoices per staff member.
Machine learning algorithms also enable pattern detection across millions of transactions, which is impractical for human reviewers. Automation improves visibility into anomalies and supports real-time flagging of duplicate or suspicious invoices.
Accuracy rates also improve significantly. The average invoice accuracy rate in traditional AP departments hovers around 91.7%. With automated validation and exception management, companies boost that rate and reduce downstream financial rework.
What regulatory and technological shifts are shaping invoice audits?
Mandatory e-invoicing is accelerating, especially across Europe and Latin America. As noted by Procys, digital invoice formats enhance auditability and simplify compliance.
Organizations also face pressure to comply with tax and data retention regulations. Automated audit trails, according to DigitalDefynd, cut audit response times by ensuring quick retrieval of supporting documentation.
Cloud-based ERP integrations are becoming standard, enabling seamless access to financial data across departments. As more finance platforms adopt API-first approaches, audit automation is now easier to deploy across multiple business units and vendors.
What makes invoice auditing more sustainable and scalable today?
Paper-based audits are being phased out. Sustainability goals, paired with regulatory pressure, are driving digital adoption in finance departments. Automation not only eliminates physical document storage but also supports remote audits and global vendor oversight.
With scalable audit engines, businesses adjust audit frequency based on risk tiers or spend volume. Instead of annual audits, high-spend vendors are monitored monthly, providing earlier detection and faster resolution of billing errors.
Systems such as RadiusPoint’s ExpressLogic™ are built to scale, supporting clients with dynamic supplier bases while maintaining high audit accuracy.
How does RadiusPoint’s auditing solution deliver measurable results?
RadiusPoint has been delivering invoice auditing solutions for over 20 years, with a proven track record of recovering costs, reducing billing discrepancies, and preventing fraud across telecom and utility expense solutions.
Through its proprietary ExpressLogic™ platform, RadiusPoint automates the audit process from ingestion to resolution. The system integrates with client ERP and billing platforms, validates line items against contract terms, and flags outliers in real-time.
Clients benefit from detailed reporting dashboards, task automation, and proactive vendor dispute handling. It has saved clients millions through precise invoice validation and cost recovery, positioning RadiusPoint as a leader in TEM and invoice audit services.
To explore more, contact our sales team.
How should organizations evolve their invoice audit strategy moving forward?
To future-proof their AP functions, organizations must combine automation, analytics, and skilled oversight. Auditing should shift from a reactive, year-end activity to a continuous process embedded in procurement and payment workflows.
Audit metrics should be benchmarked quarterly to monitor progress and surface systemic issues. High-risk vendors should be subject to a stricter audit cadence, while all suppliers should be monitored for compliance deviations.
As fraud techniques evolve and invoice volumes grow, businesses must ensure executive-level visibility into audit outcomes and maintain robust documentation. Investing in scalable, automated invoice auditing is no longer optional—it’s a core part of financial governance and risk management.
What does Telecom Lifecycle Management mean in today’s enterprise landscape?
Telecom Lifecycle Management (TLM) is a structured, end-to-end process designed to manage telecom assets, services, vendors, contracts, and expenses throughout their operational life.
In multi-vendor environments, this lifecycle becomes more intricate due to overlapping contracts, asset duplication, fragmented support tickets, and disjointed SLAs.
TLM provides a centralized framework to govern every telecom activity, from provisioning and usage to deactivation and asset recovery.
A key differentiator between TLM and basic telecom support lies in its proactive, cross-departmental structure.
While traditional support reacts to issues, TLM governs operational workflows per procurement, finance, and IT policies.
This allows enterprise teams to audit, validate, monitor, and optimize performance relative to business objectives.
As mid-to-large enterprises adopt hybrid network models and expand distributed teams, managing telecom costs without a formal lifecycle strategy leads to waste, overbilling, compliance violations, and infrastructure sprawl.
What stages make up the telecom lifecycle in a multi-vendor setup?
Telecom lifecycle management encompasses multiple operational and financial checkpoints. Each stage interacts with vendors, internal departments, and existing IT systems.
Inventory acquisition starts with sourcing vendor-managed or in-house telecom assets. This includes ordering mobile lines, internet circuits, VoIP, 5G routers, or unified communications hardware.
These assets are tagged, cataloged, and assigned based on departmental use.
Service activation follows provisioning. It involves assigning SLAs, configuring carrier services, and ensuring billing aligns with negotiated terms.
Failure to enforce SLAs from day one leads to poor service quality and budget overruns.
Next is usage tracking and SLA compliance. Enterprises must reconcile actual usage against vendor limits, monitor outage frequencies, and ensure services meet defined KPIs.
Without accurate metrics, support issues often escalate or go unnoticed.
Invoice validation and expense management represent the most error-prone lifecycle phase. According to Gartner via GDS, up to 14% of telecom bills contain errors, mostly favoring carriers.
These discrepancies result in overcharges and budget gaps.
Change management and upgrades ensure systems remain aligned with evolving needs. Departments must reassign, scale, or consolidate services as team structures or operational demands shift.
Finally, renewal and deactivation handle contract expirations and asset retirement. Without proper documentation, devices go unused while still incurring monthly charges.
Refurbished equipment, when used effectively, saves around 60% in upfront costs.
What are the biggest challenges organizations face in managing TLM?
As enterprises grow, vendor sprawl becomes inevitable. Managing dozens of telecom providers increases the risk of duplication, lack of transparency, and service overlap.
When vendor onboarding is manual, delays in provisioning reduce productivity and raise project costs.
Billing inaccuracies persist as a top concern. As reported research, between 12-20% of invoices contain errors. Without audit-ready platforms, finance departments miss out on refunds and spend unnecessary hours validating line items.
Disjointed inventory is another common bottleneck. Many IT teams operate without a centralized asset repository, making it difficult to track usage-based charges or confirm contract-bound assets. During mergers or remote expansions, these issues multiply.
Regulatory and compliance risks also increase. With nearly 98% of organizations linked to a third-party breach (SecurityScorecard), tracking lifecycle ownership is critical to avoiding liability.
Distributed teams add operational pressure. When employees work across different states or countries, inactive services often remain unnoticed.
Without lifecycle visibility, these silent costs accumulate into significant overhead.
How do modern software platforms support telecom lifecycle management?
TLM software solutions streamline asset provisioning, automate invoice reconciliation, and offer visibility across the vendor spectrum.
These platforms provide usage-based analytics tied to vendor SLAs and mapped to finance systems.
Cloud-based portals reduce email dependency by enabling real-time escalation, order tracking, and asset transfers.
Platforms like RadiusPoint’s embed governance into workflows so that every change request or provisioning task aligns with approval policies.
Automation plays a major role in reducing human error. From auditing invoices to deactivating dormant lines, software enables telecom managers to optimize lifecycle events without manually checking multiple spreadsheets.
API integrations are vital. Effective TLM tools connect with ERP, HR, and ITSM systems to synchronize personnel changes, reallocate costs, and manage inventory in accordance with operational shifts.
Analytics dashboards provide visibility across lifecycle stages. From onboarding a new device to tracking usage anomalies, dashboards allow teams to compare service levels with historical performance and adjust strategies before costs spike.
Which technologies are transforming TLM going forward?
Emerging technologies are enhancing lifecycle precision. AI-driven platforms identify anomalies in billing or usage patterns by learning historical behaviors. This enables pre-emptive ticketing or renegotiation opportunities.
With 5G expansion, bandwidth allocation and asset deployment become more complex. xRAN frameworks offer more flexible provisioning, but also require updated lifecycle protocols.
TLM platforms need to track edge nodes, microcells, and virtual assets in near real-time.
IoT is another disruptor. As sensor-based devices connect to corporate networks, their lifecycle must be governed to avoid security lapses and operational blind spots.
Each IoT node has unique provisioning, security, and billing characteristics.
Sustainability has emerged as a strategic goal. Organizations now require eco-friendly decommissioning of outdated equipment.
By including recycling metrics and carbon offset benchmarks, TLM contributes to ESG reporting.
Blockchain-based lifecycle tracking is also gaining ground. When embedded in TLM platforms, blockchain enhances contract transparency, automates SLA verification, and prevents disputes over service delivery timelines.
What should enterprises look for in a TLM solution?
A robust TLM solution must deliver more than visibility. It must automate lifecycle governance from acquisition to retirement, enforce policy compliance, and provide SLA-focused insights.
Enterprises should look for centralized asset repositories that show the real-time status of telecom lines, hardware, and licenses. These inventories should be contract-bound, aligned with provisioning dates, and mapped to renewal timelines.
Reporting capabilities should offer SLA-based alerting, downtime tracking, and comparative vendor benchmarks. Such metrics help managers understand performance bottlenecks or support deficiencies.
Invoice validation workflows should allow audit trails and approval escalations. This reduces finance friction and enables monthly accuracy without delay.
Lastly, the architecture must be scalable. Whether a business adds new vendors through M&A or expands to remote teams, the platform must grow without bottlenecks or data integrity loss.
How does RadiusPoint’s TEM platform solve telecom lifecycle challenges?
RadiusPoint integrates every telecom lifecycle function into a single cloud-based interface. From contract uploads to invoice audits and real-time asset reconciliation, it provides structured workflows that replace spreadsheets and manual tracking.
Its audit-ready framework captures overbilling, flags unused services, and allows direct dispute management with vendors. Based on analysis, organizations save between 10-30% annually by implementing a structured TEM solution.
The platform also enforces policy-compliant provisioning and deactivation. Lifecycle tasks are triggered based on contract renewals, organizational changes, or budget thresholds, ensuring no unused assets remain active.
ExpenseLogic supports vendor onboarding, contract governance, and SLA-based reporting in one place. Its integration with finance and procurement systems ensures that every invoice is tracked relative to assets, services, and agreements.
Client case studies have shown reductions in telecom spend, increased compliance readiness, and measurable productivity gains. For distributed and complex networks, RadiusPoint offers a proven TLM engine to regain cost control.
Why is future-ready TLM critical for 2025–2027 enterprise goals?
As enterprises move toward AI-led operations, distributed teams, and regulatory scrutiny, managing telecom as a lifecycle—not a cost center—becomes a strategic necessity.
A future-ready TLM approach supports edge deployments with real-time visibility, enforces compliance by managing lifecycle ownership, and reduces unnecessary spending through proactive governance.
Organizations aligning TLM with sustainability goals reduce e-waste, optimize energy usage, and support green IT initiatives. In tandem, SLA-focused platforms enable service consistency without overspending.
By investing in structured, tech-enabled TLM today, enterprises ensure operational resilience, strategic cost savings, and lifecycle control across their telecom environments for years to come.
The Ultimate Guide on Multi Vendor Support
Multi vendor support is a unified IT service model that provides a centralized, SLA-driven framework for managing, troubleshooting, and maintaining technology infrastructure sourced from multiple original equipment manufacturers (OEMs). Instead of working separately with individual vendors for servers, storage, networking gear, or software, businesses consolidate support into one cohesive, interoperable platform. The approach is vendor-agnostic, modular, and engineered to reduce downtime, streamline coordination, and cut total cost of ownership across fragmented systems.
In a modern enterprise, this strategy is especially valuable where hardware diversity and hybrid environments dominate. Whether it’s a Lenovo server, NetApp storage, Cisco firewalls, or VMware cloud services, all require synchronized support to avoid operational silos and escalations. It helps organizations scale their infrastructure, simplify contract management, and align support protocols relative to service tiers and compliance obligations. It acts as a centralized layer across vendors, improving issue resolution and reducing the average time-to-repair in environments where complexity is the norm.
Why do businesses need multi vendor support in today’s IT environments?
The shift toward cloud-native applications, SaaS stacks, and globally distributed systems has made IT infrastructures more heterogeneous than ever. Businesses are no longer sourcing everything from a single vendor. Instead, operations rely on integrated platforms, hybrid cloud deployments, and software ecosystems involving five to ten distinct vendors, each with their maintenance policies, escalation procedures, and service-level agreements.
This diversity creates friction. Finger-pointing during outages, delayed diagnostics due to vendor incompatibility, and repetitive onboarding for multiple support contacts all increase operational risk. In data centers or retail environments where uptime is critical, delays in issue resolution translate directly into revenue loss. According to EasyVista, the average cost of IT downtime is around $9,000 per minute for large enterprises. Even mid-sized businesses feel the sting, with The 20 reporting that 81% of respondents suffer losses exceeding $300,000 for just 60 minutes of unplanned downtime.
it resolves this complexity by acting as a centralized command center, ensuring seamless coordination across hardware, software, and cloud providers. It gives IT leaders more control over contract renewals, avoids redundant support contracts, and creates visibility into every vendor’s compliance with SLAs.
What are the core benefits of using multi vendor support?
It isn’t just a convenience—it’s an operational strategy for reducing risk, increasing efficiency, and improving cost predictability. By consolidating vendor interactions through a unified platform, businesses eliminate the administrative overhead of tracking multiple renewal dates, support portals, and escalation paths.
One of the standout benefits is accelerated resolution. Instead of initiating parallel tickets with different vendors and waiting for blame to be shifted, businesses gain a single point of contact that owns the incident from start to finish. This significantly reduces mean time to repair (MTTR) and ensures service alignment across systems.
There’s also a financial upside. The Fortune Business Insights report projects that the multi vendor support services market will reach over USD 69.87 billion by 2032, highlighting growing enterprise investment. Organizations pursuing this model often achieve 10–20% savings on total support costs. This happens not only through bulk support agreements but also via reduced downtime, optimized contract lifecycle management, and fewer resource overlaps.
Furthermore, scalability becomes much easier. As businesses adopt new technologies—whether edge computing nodes or multi-cloud orchestrators—support can be extended through the same integrated framework rather than creating new silos. Support becomes a predictable, governable layer that evolves with infrastructure.
How does multi vendor support differ from traditional IT support or third-party maintenance (TPM)?
While traditional IT support and third-party maintenance are often reactive or piecemeal in nature, it is proactive, SLA-driven, and engineered for consistency across ecosystems. TPM typically steps in when OEM warranties expire or when cost-cutting is prioritized over service breadth. Although TPM offers extended hardware coverage, it lacks the orchestration and contract unification that multi vendor support provides.
Unlike fragmented maintenance agreements, it focuses on interoperability. It’s designed to align with enterprise service levels, escalate issues across systems, and consolidate ticketing processes. The goal isn’t just to fix hardware—it’s to ensure coordinated performance across server clusters, storage environments, networks, and cloud workloads.
Additionally, this support enables real-time diagnostics and resolution tracking across platforms. For example, an incident involving NetApp storage impacting a VMware ESXi cluster can be resolved without bouncing between two OEMs. Support is mapped to service tiers, linked with compliance policies, and often integrated with monitoring dashboards to detect failure points early, minimizing escalations and resolution delays.
What types of organizations benefit most from multi vendor support?
Organizations of all sizes benefit from this, but it offers the highest ROI in environments managing diverse and distributed technology. SMBs that lack internal IT resources can offload operational complexity, while large enterprises gain centralized control over sprawling support contracts and compliance frameworks.
Industries such as retail, healthcare, finance, aviation, and education are especially reliant on multi-vendor ecosystems. For instance, a retail chain may have POS systems from Oracle, payment hardware from Ingenico, and networking gear from Aruba—all operating under different OEMs. In a healthcare setting, a hospital’s server infrastructure may involve Dell, backup appliances from Veritas, and imaging systems from GE, requiring synchronized support.
In these contexts, this support improves operational agility. It reduces the burden on internal IT admins and ensures compliance is upheld across vendor protocols. For fast-scaling environments, it also helps avoid infrastructure fragmentation, giving decision-makers a unified view of system health, costs, and contract obligations.
Which platforms and environments require multi vendor support?
Modern IT infrastructure is no longer confined to a single rack or vendor ecosystem. It becomes essential in complex environments where disparate technologies coexist across hybrid clouds, on-premises data centers, and global SaaS deployments. The goal is to provide consistent, centralized support across this diversity without sacrificing performance or compliance.
Hybrid cloud setups, in particular, benefit significantly. Businesses often run critical workloads on platforms like AWS or Azure while retaining sensitive data on local servers from Dell or Lenovo. Without a multi vendor strategy, support becomes fractured, requiring separate engagements, incompatible SLAs, and uneven incident response. Unified support, monitoring, and troubleshooting are orchestrated across cloud and on-prem systems through a single framework.
E-commerce platforms and digital marketplaces also depend on robust multi vendor support. These businesses rely on APIs, payment gateways, warehouse automation tools, and third-party plugins from various providers. According to Raconteur, third-party sellers will account for 59% of global e-commerce sales by 2027. This creates an urgent need for centralized support that aligns across integrated services and ensures an uninterrupted customer experience.
Data centers, too, often run multi-vendor equipment—switches from Juniper, servers from HPE, and storage from Pure—where coordinated incident resolution is critical to uptime. Similarly, telecom and 5G rollouts involve numerous vendors across the network core, edge, and radio layers. In these environments, the ability to align service tiers, escalation paths, and real-time monitoring across vendors is not just helpful—it’s mission-critical.
What tools and features enhance multi vendor support effectiveness?
Effective support relies on tools that integrate across vendors and environments. Centralized dashboards provide visibility into support status, asset health, and service ticket progression—all aligned with SLA metrics. These platforms unify alerting and escalation, allowing IT teams to act swiftly when incidents span multiple technologies.
Monitoring tools play a central role. They track system uptime, detect anomalies, and correlate issues across devices and services. For example, a performance degradation in a virtualized storage cluster may stem from upstream network congestion. Instead of opening cases with individual vendors, support teams use integrated tools to pinpoint the source, trigger the correct resolution path, and document the outcome within one interface.
Automation adds another layer of efficiency. From provisioning new devices to logging support calls based on monitored alerts, automation reduces manual errors and accelerates service. AI-enhanced diagnostics assist in identifying recurring issues, matching patterns to known resolutions across vendor databases.
Most importantly, these tools must remain SLA-driven and compliant. Features like escalation timers, contract linkage, and performance scorecards help ensure vendors are accountable. Support delivery remains consistent and measurable, regardless of how many OEMs are in the ecosystem.
What challenges does multi vendor support help solve?
At its core, it addresses inefficiencies that stem from system fragmentation. When hardware, software, and cloud platforms operate under different support umbrellas, teams waste hours navigating disconnected ticketing systems, incompatible diagnostic tools, and inconsistent response times. This increases the mean time to resolution and opens the door to regulatory exposure.
Downtime is perhaps the most immediate threat. The CIO Dive report notes that the median annual downtime from high-impact IT outages is 77 hours, with hourly costs reaching up to $1.9 million. These disruptions often happen when a vendor delay triggers a chain reaction across interlinked systems. This support reduces this risk by ensuring incidents are escalated and resolved holistically.
Security is another critical challenge. In fragmented support models, patch cycles and firmware updates may vary between vendors. This misalignment creates vulnerabilities, especially in regulated industries like healthcare and finance. It creates a standardized process for updates, aligned with risk management policies and compliance timelines.
Finally, contract sprawl can lead to cost waste and missed renewals. Studies from Procurement Tactics indicate that 2% to 11% of total contract value is often lost to mismanagement. It consolidates these contracts, making renewals simpler, pricing more transparent, and budgeting more accurate.
How does multi vendor support impact contract consolidation and cost control?
Managing multiple vendors without a centralized strategy results in overlapping support contracts, mismatched service levels, and unnecessary administrative burdens. Each contract brings its own terms, renewal timelines, and pricing models—creating inefficiencies that often go unnoticed until a failure or audit forces attention. It addresses this by standardizing and consolidating contracts into a unified framework aligned with business objectives and SLA requirements.
When vendor management is fragmented, the cumulative cost of oversight increases. Research from Moldstud shows that organizations allocate approximately 20–30% of their entire budget to vendor management. That figure often includes contract negotiation, compliance tracking, and time lost managing disconnected systems. A multi vendor model helps reduce this burden by eliminating duplicate contracts and offering enterprise-wide service bundles.
Cost predictability improves as well. With centralized billing and reporting, businesses gain real-time visibility into support spend across departments, projects, or geographies. This transparency makes it easier to detect overages, optimize renewals, and benchmark performance. Instead of engaging in repetitive vendor renegotiations, procurement teams operate from a single pane of control, reducing cycle times and freeing up resources for more strategic initiatives.
Multi vendor support also reduces the “soft costs” of support, such as time wasted on escalation, delayed resolution from multi-party involvement, or missed SLAs. These operational inefficiencies often add up, even if they aren’t captured on a balance sheet. By unifying service delivery, organizations ensure that cost control extends beyond procurement and into actual performance delivery.
What are future trends in multi vendor support from 2026 and beyond?
As businesses modernize IT operations, multi vendor support must evolve to support more dynamic, scalable, and intelligent environments. AI-driven diagnostics, real-time analytics, and predictive maintenance are becoming integral components of next-generation support strategies. Instead of waiting for issues to arise, AI models will proactively flag vulnerabilities, track performance degradation, and initiate automated remediation, enabling support that’s preventive, not reactive.
Sustainability is another emerging factor. Regulatory mandates and ESG goals are prompting organizations to rethink the infrastructure lifecycle and power consumption. Multi vendor support providers are adapting by offering services that extend asset lifespans, optimize utilization, and reduce e-waste, turning hardware maintenance into a sustainability opportunity. This aligns especially well with the growing focus on green data centers and energy-efficient hardware sourcing.
Edge and 5G deployments are also shaping the future. In the telecom and industrial sectors, distributed computing architectures are replacing centralized models. These setups involve hardware and software from numerous vendors, often deployed in remote or hard-to-access areas. Multi vendor support ensures these edge components receive the same tiered, SLA-aligned service as core infrastructure, avoiding performance gaps in mission-critical operations.
Cloud lock-in concerns are rising, too. Cloud Computing News reported that 80% of enterprises have moderate to high levels of concern about being locked into a single cloud vendor. Multi vendor support is an effective counter-strategy—it enables portability, encourages platform-neutral architecture, and keeps organizations agile in the face of cloud service shifts or cost spikes.
What should businesses consider when selecting a multi vendor support provider?
Selecting a multi vendor support partner isn’t just about coverage—it’s about alignment with long-term operational goals, risk tolerance, and technology strategy. Businesses must assess how well the provider integrates with their existing infrastructure, how it governs service levels across systems, and how proactively it manages incidents that span multiple technologies.
One of the first considerations is service-level alignment. A competent provider will offer SLA structures that mirror internal uptime expectations and compliance needs. It’s not enough to promise 24/7 support; response times, escalation paths, and resolution guarantees must be clearly documented and consistently tracked. In environments with strict audit requirements, SLA transparency is non-negotiable.
Global reach and OEM diversity are also critical. A support partner must be capable of managing hardware and software from a broad range of vendors, across geographic regions, and in both on-prem and cloud-native configurations. Businesses with distributed teams or remote assets—such as retail stores, warehouses, or branch offices—require a provider with field coverage and remote diagnostics capability.
Another key factor is integration. This support must seamlessly align with the company’s existing ticketing, monitoring, and asset management platforms. Support should not exist in isolation—it should be embedded into daily IT workflows, with consolidated dashboards, automated alerts, and unified reporting systems that track performance across all touchpoints.
Support providers that offer embedded automation, predictive analytics, and AI-powered recommendations stand out. These capabilities allow businesses to shift from reactive incident management to proactive optimization. Over time, this improves not just technical performance, but also financial planning and vendor governance.
Lastly, contract flexibility matters. As businesses scale or shift technologies, the support structure should evolve with them. This includes modular service plans, scalable SLAs, and transparent billing models that support growth without introducing lock-in.
What are the key metrics to track multi vendor support ROI?
The value of this support is best measured through performance metrics that align with both operational outcomes and financial impact. Uptime, resolution speed, and cost avoidance are core pillars that demonstrate return on investment across the service lifecycle.
One of the most direct indicators is a reduction in downtime. When incidents are resolved faster due to centralized coordination, businesses reduce revenue loss, avoid SLA penalties, and maintain higher service quality. As noted by The 20, even 60 minutes of downtime can cost over $300,000 for the majority of businesses. It helps mitigate this risk by ensuring all vendors are held accountable to unified response protocols.
Support ticket velocity and first-time resolution rate are also important. Fewer escalations, fewer repeated issues, and faster average resolution time point to stronger coordination and more effective service design. These metrics directly affect IT productivity and the internal cost of troubleshooting.
From a financial perspective, contract consolidation lowers administrative overhead and improves spend visibility. Businesses can track support cost per asset, SLA compliance rate per vendor, and total contract reduction over time. These indicators help benchmark cost performance against the IT budget and provide data to guide renewal and renegotiation decisions.
Moreover, qualitative ROI matters too. Businesses should assess whether support improves decision-making, reduces IT fatigue, and enhances service consistency across departments. When service is aligned with business continuity goals, ROI extends beyond spreadsheets into long-term competitive advantage.
How does RadiusPoint deliver integrated multi vendor support with TEM?
RadiusPoint’s approach to multi-vendor support is embedded within its Telecom Expense Management (TEM) solution, ExpenseLogic, designed to centralize support, streamline expense visibility, and standardize service delivery across complex technology ecosystems. By combining vendor coordination with telecom and IT cost management, RadiusPoint addresses the operational and financial pain points businesses face in multi-vendor environments.
One of the key advantages RadiusPoint offers is a single point of accountability. Whether clients are managing mobile endpoints, unified communications platforms, or data center assets, RadiusPoint coordinates across OEMs to deliver SLA-aligned, contract-aware support. This eliminates vendor conflicts and ensures that each incident is managed with the full context of the environment.
The platform tracks support costs, ticket activity, asset inventory, and contract terms in one place, enabling real-time decision-making and performance benchmarking. It also integrates with AP systems for invoice reconciliation, allowing IT and finance teams to align procurement with support delivery.
In sectors where compliance, scalability, and speed are critical, such as healthcare, finance, retail, manufacturing, logistics, education, and energy, RadiusPoint helps reduce downtime, improve support reliability, and optimize total vendor spend.
With the global multi vendor support services market projected to exceed $69.87 billion by 2032, organizations investing in unified, SLA-driven models stand to gain a measurable competitive edge. RadiusPoint empowers this shift by offering a consolidated service layer that supports infrastructure resilience, financial transparency, and operational control.
Request a demo and talk with our team to discuss your needs.
Complete Guide on Utilization Management in Healthcare
Utilization management (UM) in healthcare is a structured, data-driven process used by health plans, hospitals, and insurers to evaluate the necessity, appropriateness, and efficiency of medical services, procedures, and hospital stays.
It serves as a regulatory checkpoint that determines whether a healthcare service is medically necessary, cost-effective, and consistent with evidence-based care standards before it is delivered, during treatment, or after it has occurred.
It is not just a compliance obligation; it is a core component of managed care, value-based delivery, and population health strategies.
The goal is to align medical decisions with clinical guidelines while preventing unnecessary tests, treatments, or prolonged hospitalizations.
This process supports both fiscal responsibility and patient-centered care by ensuring services are justified and outcomes-based rather than volume-driven.
It’s program rely on real-time reviews, clinical documentation, and decision support tools to assess each case.
They operate across three primary phases: prospective review (prior authorization), concurrent review (during care), and retrospective review (post-treatment).
These processes are usually executed by a combination of nurses, physicians, data analysts, and increasingly, intelligent software platforms.
Why Is Utilization Management Important in Modern Healthcare Systems?
Utilization management is essential for maintaining equilibrium between healthcare quality and cost control.
As U.S. healthcare spending reached $4.87 trillion in 2023, growing faster than GDP for the first time since the pandemic (AMA), much of that growth was attributed to increased utilization.
Without structured review systems, this surge often results in unnecessary interventions, fragmented care, and avoidable financial strain on both patients and payers.
Effective management ensures services are aligned with standardized clinical pathways, reducing the risk of overuse and inappropriate care.
For instance, research published by Nature Digital Medicine highlights that a significant number of coronary angiographies and bypass surgeries may be inappropriate, inflating costs and exposing patients to unnecessary risks.
It also has regulatory significance. Institutions must comply with CMS requirements, NCQA standards, and HIPAA regulations that directly intersect with utilization review protocols.
These frameworks enforce timeliness, documentation accuracy, and patient privacy throughout it’s lifecycle.
How Does the Utilization Management Process Work?
The utilization management process functions as a tiered system of medical review, structured to assess whether services meet clinical, financial, and administrative benchmarks at key points of patient care.
Each stage involves distinct actions, staff roles, and approval criteria, and it’s designed to be both preventive and corrective.
It’s decision influences whether services are authorized, delayed, denied, or modified, all based on current care guidelines and policy frameworks.
Step 1: Initial Case Identification or Notification
This phase involves flagging cases that require review based on treatment codes, high-cost thresholds, or payer triggers. Notifications often occur through automated intake tools or EHR-based alerts.
Step 2: Clinical Review (Prior Authorization)
Prior authorization is the most recognized form of UM and often the most controversial. It requires healthcare providers to justify procedures or medications before they’re approved.
According to the AMA, 88% of physicians describe prior auth burdens as high, and 80% of patients have abandoned treatment due to delays.
Step 3: Concurrent Review During Care
While a patient is hospitalized or undergoing treatment, concurrent reviews monitor clinical progression and discharge readiness.
Reviews occur in real-time and are coordinated between hospital staff and insurance case managers to ensure the continued appropriateness of care.
Step 4: Retrospective Review After Care
Post-treatment analysis verifies whether services already rendered were medically necessary. Though less preventive, this stage helps recover payments, flag errors, and inform coverage adjustments.
Step 5: Appeals and Reconsideration
If a service is denied, providers or patients may initiate an appeal. Reviews involve both clinical and contractual reassessments.
Efficient systems aim to minimize appeal rates by ensuring consistent application of medical necessity criteria.
What Are the Different Types of Utilization Management?
It is categorized based on the timing of review relative to patient care. Understanding each type clarifies how decisions are coordinated, who makes them, and when they impact the patient journey.
The most common form is prospective review, also known as prior authorization. Here, the treatment is evaluated before it’s delivered. This method aims to prevent unnecessary costs and service delays but has drawn criticism for causing treatment bottlenecks.
In contrast, concurrent review takes place while care is ongoing. This model is proactive and time-sensitive, helping to manage length of stay and resource utilization in hospital settings.
Retrospective reviews occur after services have been delivered. Though less favorable from a patient-experience standpoint, they help identify patterns of overuse or abuse and inform payer policy updates.
These types must not be confused with case management, which focuses on coordinating services for complex patient populations rather than controlling service approval.
What Tools and Technologies Support Utilization Management?
Digital transformation has reshaped how this is executed. Platforms equipped with artificial intelligence, predictive analytics, and clinical decision support systems (CDSS) allow payers and providers to make faster, more accurate determinations.
In addition, AI-driven models assess vast volumes of patient data to predict high-risk cases needing intervention. Automation also plays a vital role in reducing physician burden.
A NIH-backed study shows that 62% of physician burnout stems from administrative EHR tasks, prompting 38% of large hospital systems to implement UM automation.
These technologies not only streamline decisions but ensure consistency, transparency, and scalability, critical for regulatory compliance and operational excellence.
How Is Utilization Management Implemented in Hospitals and Health Plans?
Implementation varies between payer models and care settings but generally requires a coordinated framework combining people, processes, and platforms.
Hospitals integrate it into their billing, discharge planning, and care coordination functions.
Dedicated utilization nurses or clinical reviewers evaluate real-time patient data to ensure medical necessity standards are met.
Health plans deploy it through structured policy documents, integrated claims systems, and AI-powered review engines.
Often, third-party utilization management companies manage this function to improve objectivity and efficiency.
One common barrier is fragmented communication between providers and payers, which leads to delays or denials.
Hospitals now emphasize automation, transparency, and documentation compliance to overcome these friction points.
How Does Utilization Management Affect Patients and Providers?
UM decisions have a direct, measurable impact on healthcare access, delivery, and patient satisfaction.
For patients, delays in authorization often result in deferred care, financial stress, or clinical deterioration.
The AMA notes that 94% of patients have experienced care delays due to prior auth, and 33% of physicians have observed serious adverse events as a result.
Physicians and administrators face mounting administrative complexity. Time-consuming tasks, unclear payer requirements, and inconsistent criteria result in reduced job satisfaction, documentation overload, and poor morale.
A NIH article found transportation barriers impact access to care for 3–67% of Americans, depending on geography. When combined with restrictive management policies, these barriers disproportionately affect marginalized populations.
What Guidelines Govern Utilization Management?
It is not arbitrary; it is anchored in national and state-level regulations. CMS sets forth rules on what constitutes medically necessary services under Medicare and Medicaid programs. Payers must align with these definitions during reviews.
Organizations such as NCQA enforce accreditation standards that require timely authorizations, physician involvement, and appeal protocols.
Failing to meet these standards affects an institution’s credibility and reimbursement eligibility.
HIPAA adds another layer of governance by mandating secure handling of protected health information (PHI) during UM processing, especially in AI-enabled platforms.
Additionally, frameworks like the BURDEN score assess payer UM policies for transparency and fairness, particularly in how coverage decisions affect patient outcomes.
What Are the Pros and Cons of Utilization Management?
It offers measurable advantages when properly implemented. It reduces unnecessary expenditures, ensures treatment relevance, and enhances compliance with care protocols.
These benefits support institutional accountability and value-based reimbursements.
However, the process has downsides. Poorly managed utilities cause service delays, administrative overload, and patient dissatisfaction.
It also creates friction between providers and payers, especially when decisions are made without clear medical rationales.
Balancing efficiency with compassion remains the central challenge. The solution lies in transparent criteria, automation, and data-informed decision-making.
What Is the Future of Utilization Management Post-2025?
As healthcare delivery continues evolving, it is expected to expand into areas like behavioral health, telemedicine, and virtual care models.
According to Vizient, behavioral health utility management will grow by 8% for inpatient and 26% for outpatient services by 2034.
It workflows will increasingly occur virtually. The American Hospital Association projects that 23% of UM-related visits will be virtual by 2034, along with 50% of psychotherapy visits, pushing hospitals to rethink review logistics.
Data integration, real-time approval, and advanced analytics will further refine utilization decisions, prioritizing patient outcomes while controlling costs.
How Can Automation Improve Utilization Management?
Automation plays a vital role in reducing decision-making friction. By streamlining data validation, criteria matching, and real-time alerts, automated management eliminates redundant approvals and accelerates patient access.
It reduces the burden on clinical staff, ensures faster turnaround for prior authorizations, and lowers appeal rates. Predictive models flag cases for early intervention, reducing inpatient stays and procedural duplication.
Yet, automation must remain compliant. HIPAA regulations and NCQA guidelines require encrypted handling of medical data and human oversight for AI-driven decisions.
Ethical use of automation demands accuracy, fairness, and explainability.
How Can RadiusPoint Help with Utilization and Expense Management?
At RadiusPoint, we deliver a unified solution that merges utilization management automation with cost and resource tracking across healthcare enterprises.
Our platform integrates seamlessly with your existing systems, automating clinical documentation reviews, monitoring policy compliance, and generating actionable reporting.
Whether you’re a hospital administrator, insurance CIO, or compliance officer, RadiusPoint empowers your organization with the insights and tools needed to minimize delays, reduce costs, and improve care quality.
Request a demo to see how our solutions bring clarity and control to your management processes.
What is Usage Management? Detailed and updated Guide
Usage management is the structured process of collecting, monitoring, analyzing, and controlling how resources, such as data, software, network bandwidth, or infrastructure, are consumed within an organization.
It helps businesses gain visibility into actual usage patterns, enforce policies, and optimize allocation of assets and services. This process plays a pivotal role in enabling usage-based pricing models, quota management, and compliance enforcement.
It also underpins cost-effective service delivery in telecom, SaaS, and cloud environments. Key elements include data collection through user activity and system logs, real-time usage monitoring, quota enforcement based on defined thresholds, policy automation to govern usage behavior, and structured reporting through dashboards or usage APIs.
How does usage management work across systems and platforms?
The usage lifecycle typically includes capture, storage, analysis, and action. Systems first capture data by logging user interactions, consumption events, or device activity.
This data is securely stored in structured databases or cloud storage.
Analytical tools then evaluate patterns, detect anomalies, and flag overages or inefficiencies. Based on these insights, automated systems trigger actions such as restricting access, provisioning additional resources, or sending notifications.
In cloud services, management ensures resource efficiency and cost control.
According to OpenMetal, 28% of public cloud spend is wasted, highlighting the necessity of real-time controls and proactive policy enforcement in cloud environments.
Why is usage management important for organizations today?
It provides a foundational layer of operational control and financial discipline. It supports resource optimization, eliminates untracked consumption, and drives billing transparency in usage-based service models.
It is especially critical for organizations operating at scale, where decentralized systems and fragmented data can quickly lead to overspending or compliance failures.
According to Flexera, 84% of organizations struggle to manage cloud spend, reinforcing the need for granular usage visibility, real-time monitoring, and cross-functional alignment across IT, finance, and operations.
What are the benefits of implementing usage management?
Implementing management leads to measurable gains in cost-efficiency by identifying underutilized or redundant assets.
It enhances operational transparency, allowing stakeholders to understand usage behavior and make informed decisions.
Accurate metering and consumption logs support predictable billing and enable companies to adopt usage-based pricing without revenue leakage. It also simplifies compliance by maintaining audit-ready records.
StormForge reported that over $17 billion is spent annually on idle cloud resources, a figure that highlights the urgency of deploying management strategies that align resource allocation with actual demand.
What statistics highlight the need for effective usage management?
According to Statista, 30% of cloud spend is wasted, while Flexera notes that 84% of organizations struggle to control cloud costs.
PR Newswire projects $44.5 billion in cloud waste in 2025 due to disconnects between FinOps and developer teams.
G2 Track also found that 85% of organizations fail to comply fully with software license terms.
These figures underscore the importance of usage management as a foundational discipline for cost control, policy enforcement, and operational agility.
Which industries rely heavily on usage management?
Industries such as telecom and utilities use it for service metering, quota enforcement, and billing accuracy.
SaaS providers and software vendors rely on it to support consumption-based pricing models. In cloud infrastructure, it facilitates real-time usage tracking and cost control.
Manufacturing and energy sectors use it to monitor machine usage and energy flow, while healthcare and IoT ecosystems depend on it for device-level usage visibility.
According to Chargebee, 46% of SaaS companies now offer usage-based pricing, and as Metronome reports, 78% of them adopted it in the last five years, signaling a shift toward transparent, consumption-linked billing.
What are the common types or models of this management?
This management model varies based on how resources are consumed.
Quota-based systems allocate fixed limits to users or devices, while time-based models track usage over defined periods such as CPU hours or connection time.
Event-based tracking monitors discrete actions like API calls or login sessions.
Resource-based usage logs quantify consumed units such as storage space, bandwidth, or energy. Pay-as-you-go models link service costs directly to usage without long-term commitments.
These models are often supported by embedded APIs and real-time dashboards that provide administrators with ongoing insights.
How is usage management different from utilization management?
While it focuses on tracking, billing, and policy enforcement based on actual consumption, utilization management is more about ensuring optimal use of available resources or services.
In industries like healthcare or insurance, utilization management ensures services are necessary and cost-effective, often linked to patient outcomes or resource eligibility.
Usage management, on the other hand, measures quantity consumed and enforces predefined policies. Though both intersect in data and analysis, their objectives and contexts differ significantly.
What are the challenges businesses face in managing usage?
Businesses often face challenges in integrating usage data from multiple, disconnected systems.
Many organizations lack consistent usage logs, making it hard to apply quota limits or detect anomalies in real-time. User behavior can fall outside predefined policies, especially in large or decentralized teams.
Software license non-compliance remains a costly concern. According to OpenIT, over half of organizations have incurred millions in costs from software audit failures.
Usage tracking plays a critical role in preventing such penalties and ensuring alignment with vendor agreements.
What tools and platforms support usage management?
It is supported by various tools, including real-time dashboards, metering engines, and integration APIs.
Dashboards allow teams to view historical and real-time consumption trends, while APIs enable automated data sharing across billing systems, CRM platforms, or financial systems.
Cloud FinOps platforms help control infrastructure costs, and Telecom Expense Management tools offer deep usage tracking across telecom assets. Platforms like RadiusPoint’s ExpenseLogic provide full lifecycle visibility by linking usage data with billing records, contracts, and inventory, making them ideal for organizations operating in complex environments.
How does it connect with Telecom Expense Management (TEM)?
Usage management supports TEM by enabling data usage monitoring, carrier billing validation, and device-level visibility across mobile and fixed telecom assets. It automates alerts for threshold breaches and integrates consumption patterns with billing details to ensure accountability.
RadiusPoint’s telecom expense management solution brings these capabilities together, combining real-time usage tracking with contract-level oversight. This ensures telecom services are used efficiently, billed correctly, and aligned with policy.
What are the best practices for implementing usage management?
To implement management effectively, organizations should centralize usage data across departments and platforms.
Defining clear and enforceable policies is essential, supported by real-time alerts to flag overages or anomalies.
Integration with billing, CRM, and contract management systems creates a seamless flow of data. Regular audits and benchmarking help identify trends and optimization opportunities.
An effective governance framework supports consistent, scalable practices and reinforces accountability across teams.
How can small and mid-size businesses (SMBs) benefit from it?
SMBs benefit from it by avoiding over-provisioning, ensuring cost predictability, and enhancing service transparency.
Modern SaaS-based tools offer scalable solutions without requiring significant IT overhead. Historical usage trends help with budget forecasting and vendor negotiations.
Usage alerts prevent unnecessary consumption, while usage logs support client billing or internal reporting.
CIOL reported that 27% of enterprises spend $500K+ annually due to license non-compliance, evidence that effective management is just as crucial for SMBs as it is for large enterprises.
What metrics or KPIs are critical in tracking usage data?
Key metrics include volume of resource consumption, cost-to-usage ratio, license quota utilization, overage percentage, and user-level activity distribution.
These indicators help organizations understand usage patterns, manage risk, and ensure alignment with operational and financial goals.
Regular review of these KPIs supports continuous improvement and operational efficiency.
What role do APIs play in management implementations?
APIs play a central role by enabling automated capture, retrieval, and integration of usage data. They allow systems to exchange real-time information with billing platforms, CRMs, and reporting tools.
APIs also support extensibility, allowing developers to build custom dashboards, enforce policies dynamically, and trigger workflows based on usage thresholds.
Their flexibility makes them foundational for modern, scalable usage management systems.
What does a successful usage management setup look like?
A successful setup features a centralized data warehouse for usage logs, role-based dashboards for various departments, and pre-configured alert thresholds.
Policy automation tools enforce usage rules, while integrated billing systems ensure accurate invoicing. Teams should have access to actionable insights for decision-making.
Proper documentation and change management practices support long-term success, allowing organizations to scale their usage strategies across new services or geographies.
How is usage management evolving with AI and predictive analytics?
AI and predictive analytics are transforming it by enabling systems to forecast consumption, detect irregular patterns, and optimize resource allocation.
Machine learning models analyze historical data to predict peak periods or detect misuse. These capabilities reduce operational waste, minimize risk, and support continuous improvement.
They are particularly valuable in fast-moving environments like cloud services, where manual oversight is insufficient to manage dynamic demand.
How does RadiusPoint help businesses with usage management?
RadiusPoint helps organizations gain control over consumption data and optimize expense accountability through its telecom expense management. It provides full-spectrum usage management capabilities that include real-time tracking, policy automation, and analytics integration.
RadiusPoint serves eight core sectors: telecom, utilities, manufacturing, logistics, SaaS, healthcare, retail, and education, delivering tailored insights and reporting for unique needs.
Its platform links usage records with billing, contracts, and service inventories, creating an intelligent feedback loop that reduces waste and improves operational transparency.
Finance, IT, procurement, and operations teams benefit from a centralized dashboard that supports proactive decisions and compliance enforcement.
Whether it’s mitigating cloud waste, monitoring telecom thresholds, or managing IoT resource utilization, RadiusPoint ensures consistent visibility across services.
For companies facing rising infrastructure and software costs, RadiusPoint’s solution offers a unified approach to manage usage from a single pane of glass. To learn how ExpenseLogic fits your organization’s needs, request a demo today and discover how to unlock real-time cost control and operational efficiency.
What is a vendor scorecard?
A vendor scorecard is a performance-based evaluation tool that allows businesses to measure and manage their suppliers using consistent, criteria-based metrics. It serves as a structured framework to assess vendor reliability, service delivery, cost efficiency, quality standards, and compliance obligations across procurement and supply chain operations.
The primary objective is to align supplier performance with organizational goals by establishing transparent, quantifiable benchmarks. Vendor scorecards are scalable across various industries, from healthcare and manufacturing to retail and telecom, because they translate subjective vendor feedback into objective, data-driven insights.
These scorecards standardize performance measurement, allowing procurement professionals and supply chain managers to compare vendors consistently, track improvement over time, and enforce accountability.
In high-risk categories such as telecom, logistics, or regulated sectors, scorecards support compliance mandates and reduce exposure to third-party risks.
When integrated with automated systems or vendor management platforms, they streamline the tracking of contract obligations, service-level agreements (SLAs), and delivery milestones.
How does a vendor scorecard work?
A scorecard operates through a structured set of components that form the backbone of an objective evaluation system.
These components typically include defined performance metrics, weightage assignments, a scoring framework, consistent data input methods, and a review cycle.
Metrics are chosen based on the strategic priorities of the business, such as on-time delivery, invoice accuracy, issue resolution efficiency, compliance adherence, and product or service quality.
Each metric is assigned a weight to reflect its relative importance to the business’s objectives, ensuring that scoring reflects true performance impact.
Scoring usually follows a standardized format such as a percentage scale or a rating system from one to five.
Data input for each metric is gathered from enterprise systems, procurement records, support logs, or invoice databases.
The scorecard is reviewed periodically, with monthly or quarterly reviews being common for critical vendors, and semi-annual or annual reviews for less strategic ones.
This continuous loop allows for performance tracking over time, helping businesses identify patterns, gaps, and areas for corrective action.
They may be structured differently depending on organizational needs. A balanced scorecard integrates financial, operational, and compliance indicators into one model.
Risk-focused scorecards evaluate vendors based on exposure to cybersecurity threats, regulatory breaches, or ESG violations.
Other scorecards are built specifically for contract renewals, focusing on service consistency, financial value, and adherence to previous commitments.
Customized models are also developed for different procurement categories, such as logistics, IT, or raw material sourcing.
Why do businesses use vendor scorecards?
Businesses adopt vendor scorecards to bring measurable control and clarity to supplier relationships. Many procurement functions struggle with fragmented data, inconsistent evaluations, and manual tracking that often result in overlooked inefficiencies.
These scorecards resolve these issues by establishing a uniform and transparent framework for ongoing evaluation.
Without such a system, performance issues often remain undocumented, resulting in reactive rather than proactive supplier management.
The strategic advantage of using scorecards lies in their ability to provide actionable insights.
By aligning performance metrics with organizational priorities, businesses can evaluate suppliers not just on cost, but on service quality, delivery consistency, and compliance adherence.
This becomes especially important in industries like telecom, healthcare, and logistics, where vendor reliability directly impacts operational success.
Statistics from Deloitte show that 43% of organizations have limited or no visibility into Tier 1 supplier performance, while Dun & Bradstreet notes that 61.7% of firms have experienced cyber incidents linked to third-party vendors.
These figures highlight the critical need for structured monitoring tools.
McKinsey reports that supply chain disruptions lasting longer than one month occur every 3.7 years and often increase operating costs by 3 to 5 percent while reducing revenue by up to 7 percent.
Incorporating them also enables smarter contract negotiations.
Companies with structured supplier management initiatives typically achieve average cost savings of around 12%, as cited by Procurement Leaders.
The practice improves audit readiness, strengthens compliance, and facilitates vendor consolidation.
When should you implement a vendor scorecard?
The implementation of these scorecards is often triggered by specific operational or strategic needs.
Businesses facing recurring delivery delays, incorrect billing, or quality lapses begin to realize the importance of formal vendor tracking.
These issues not only incur direct costs but also damage customer satisfaction and compliance standings. When such challenges persist, a scorecard becomes a necessary corrective mechanism.
In regulated industries, vendor scorecards are frequently introduced as part of due diligence or compliance protocols. For example, a healthcare organization might deploy a scorecard to ensure vendors meet HIPAA or FDA requirements.
Similarly, finance or telecom firms may use them to document SLA compliance and mitigate exposure during audits.
These scorecards also support internal procurement transformations, where companies are aiming to streamline supplier management processes and integrate data-driven decision-making across teams.
Scorecards are particularly effective during contract renewal periods. They offer a structured evaluation of a vendor’s past performance, making it easier for procurement teams to decide whether to continue, renegotiate, or terminate agreements.
Multi-vendor comparisons, onboarding processes, and expansion into new regions also benefit from the clarity vendor scorecards provide.
How do you create a vendor scorecard?
The creation of a scorecard starts by defining clear, strategic objectives. Businesses must determine what outcomes they expect from their supplier relationships, whether it’s cost control, quality assurance, timely delivery, or regulatory compliance.
Once goals are established, the next step is to select key performance indicators that align with these priorities. Each KPI should be quantifiable, directly tied to vendor actions, and measurable over a given period.
Weightage is then assigned to each metric to reflect its importance. For example, a company may assign 30% weight to on-time delivery, 25% to product quality, 20% to invoice accuracy, 15% to customer support, and 10% to compliance.
A standardized scoring scale is chosen, typically a 1 to 5 rating or a percentage-based system, to ensure consistency. Data inputs are mapped out based on available systems, such as ERP platforms, ticketing systems, or invoice databases.
The review process must also be defined in this stage. Most organizations conduct quarterly evaluations, but for high-value or critical vendors, monthly reviews might be more appropriate.
A pilot phase with one or two suppliers is useful to validate the scoring model before full-scale implementation.
Collaboration between procurement managers, compliance officers, finance teams, and internal stakeholders who interact with the vendor ensures that the scorecard reflects organizational needs comprehensively.
What key metrics and KPIs should you include?
Vendor scorecards are only as effective as the metrics they measure. Businesses must choose KPIs that are consistent, measurable, and directly indicative of vendor performance.
Common metrics include on-time delivery rates, product or service defect rates, invoice accuracy, issue resolution times, compliance scores from audits, and cost variance over time.
These indicators help businesses assess how well a supplier meets expectations and obligations.
Each industry has its critical metrics.
In healthcare, compliance with data protection regulations and patient safety protocols is paramount. In manufacturing, product quality and delivery timelines determine production schedules.
Retailers focus on stock availability, shrinkage rates, and seasonality. Telecom providers prioritize billing accuracy, SLA adherence, and dispute resolution times.
By tailoring metrics to industry requirements, businesses ensure the scorecard remains relevant and actionable.
How do vendor scorecards support risk and compliance management?
Scorecards are essential tools for identifying and managing risks associated with third-party relationships. In today’s increasingly regulated business environment, companies are held accountable not only for their practices but also for those of their vendors.
Risk-focused scorecards emphasize factors like cybersecurity, ESG alignment, financial stability, and legal compliance.
A security-focused scorecard may include metrics related to data breach history, certification status, regulatory violations, and incident response times.
These evaluations are especially relevant as 59% of organizational leaders now consider third-party vendors their most significant corruption risk, according to KPMG. Risk scorecards allow businesses to document due diligence efforts and provide auditable proof of oversight.
During external or internal audits, they simplify reporting by providing a centralized view of vendor performance over time.
The structured nature of a scorecard ensures that no key area is overlooked. Instead of reacting to issues after they occur, businesses are empowered to proactively monitor performance and escalate concerns.
This continuous monitoring helps identify early signs of non-compliance, enabling timely intervention and safeguarding operational integrity.
How do you score and rate vendors objectively?
Objectivity is crucial when evaluating vendors. Using a weighted scoring model ensures that each performance area contributes proportionately to the overall score.
For instance, a vendor that performs exceptionally in cost but poorly in quality will reflect a lower overall score if quality is given a higher weight.
Scoring consistency is achieved through the use of defined rating scales and rubrics.
To avoid subjectivity, organizations often use rank-based comparisons, threshold-based evaluations, or historical benchmarking. In rank-based models, vendors are compared against each other across the same set of KPIs.
Threshold models set a minimum acceptable score for each metric, ensuring only vendors who meet the criteria are approved for continued partnership.
Cross-validation by different departments, data input from verified systems, and regular calibration meetings help maintain scoring integrity across evaluators.
What tools or templates can help in building scorecards?
Scorecards can be built using basic tools like spreadsheets or more advanced platforms like vendor management systems.
Businesses looking to start quickly often use free templates available from sources like Smartsheet, HubSpot, or Score.org.
These templates include editable fields for vendor names, performance metrics, weights, and scoring formulas, making them easy to customize.
What are the real-world benefits of using scorecards?
The impact of scorecards is well-documented across sectors. Businesses using scorecards report better vendor performance, higher cost-efficiency, and lower operational risk.
A study by ISM found that 77% of suppliers believe scorecard-based compliance programs improve their internal operations.
Additionally, businesses that adopt structured vendor evaluation systems see average cost savings of 12%.
Disruption-related statistics also make the case for scorecards. Over 84.6% of businesses report increased costs due to supply chain breakdowns.
The average cost of a disruption is $1.5 million per day. By continuously monitoring vendor performance, companies are better positioned to anticipate and mitigate these disruptions before they escalate.
For small and mid-sized businesses, vendor scorecards offer a pathway to professionalize procurement without massive software investments.
These organizations benefit from enhanced vendor accountability, improved service consistency, and stronger contract negotiation leverage.
What are the best practices for ongoing scorecard success?
Ongoing success with vendor scorecards depends on regular updates, stakeholder alignment, and clear communication with suppliers.
Reviews should be conducted frequently enough to reflect meaningful performance changes. Monthly reviews are best for high-risk vendors, while quarterly or semi-annual reviews may suffice for others.
To align scorecards with procurement strategy, businesses must ensure that KPIs are linked to overarching goals and department-level OKRs.
Sharing scorecard results with vendors fosters transparency and encourages improvement. Scorecards should not be static; they must evolve based on market conditions, regulatory changes, and internal priorities.
Adding a feedback loop that includes both internal stakeholders and vendor representatives helps refine the evaluation framework over time.
What sectors benefit the most from scorecards?
Vendor scorecards deliver value across multiple sectors. In healthcare, they ensure regulatory compliance and patient safety by monitoring vendor practices around data security and medical supply quality.
In telecom, scorecards help manage multi-carrier networks by tracking uptime, billing accuracy, and service responsiveness.
Retailers use them to maintain consistent inventory levels and performance during high-demand seasons.
Logistics firms evaluate real-time performance and delivery accuracy. Energy companies monitor equipment reliability and sustainability compliance.
Even educational institutions rely on scorecards for IT infrastructure, digital platforms, and cybersecurity.
How are scorecards used in telecom expense management (TEM)?
Telecom Expense Management is a specialized field where scorecards play a vital role in optimizing cost, usage, and vendor performance.
In this context, scorecards are used to monitor telecom carriers for SLA compliance, dispute resolution timelines, data overages, and invoicing accuracy.
These evaluations ensure telecom services align with business needs and cost expectations.
In TEM, poor vendor performance often leads to service disruptions, billing errors, and unnecessary expenses.
Scorecards provide the structure to identify and resolve these issues promptly. They offer visibility into each carrier’s track record, making it easier to justify transitions, renegotiations, or escalations.
Businesses that integrate vendor scorecards into their TEM process gain better control over usage, achieve higher ROI, and reduce telecom-related risks.
How does RadiusPoint support vendor scorecard implementation?
RadiusPoint offers vendor scorecard functionality through its ExpenseLogic platform, which is purpose-built for telecom and utility expense management.
The platform automates data collection from invoices, usage logs, and service tickets to generate dynamic vendor performance reports.
These reports reflect SLA adherence, billing accuracy, and responsiveness.
RadiusPoint vendor evaluation empowers procurement and finance teams to enforce accountability.
Users can define metrics, set weights, and automate scorecard reviews based on real-time data. This reduces reliance on spreadsheets and manual audits, offering a scalable solution for organizations managing multiple telecom providers.
For organizations seeking a robust vendor evaluation process that integrates directly into their expense lifecycle, RadiusPoint provides a proven, intelligent platform.
To explore its features and see how it supports data-driven vendor management, request a demo here.
Financial Technology
Imagine a future where you’re in full control of your telecom and utility expenses. RadiusPoint is dedicated to providing insights and resources that empower you and your team for the full lifecycle of your telecom and utility invoices,.Read More
Customer Service at its Best
Over 33 years of experience allow us to identify and resolve client issues.Read More
Expense Management Services
Tailored Solutions That Maximize Value and Meet Your Budget
We understand that finding the right service provider means balancing your goals with your budget. That’s why we specialize in creating fully customized solutions designed to deliver maximum value for every dollar spent. Our pricing reflects the care and expertise we put into every project—no cookie-cutter services here.
Your needs and custom solution drive the pricing model with the monthly cost aligning with the annual expense. Costs can be applied per invoice processed monthly, an hourly fee for project-based tasks, or help desk tasks.
What Can You Expect to Invest?
Our services are as unique as your needs, and pricing varies based on factors like the number of locations and invoices to be managed, the annual dollar volume, and the level of services required. We provide services at three different levels but can tailor a service to meet your specific needs:
- Host & Load
- Receiving and loading invoices monthly
- Missing bill retrieval
- Basic
- All Host & Load services
- Invoice payment
- GL Interface file
- Accrual file
- Enhanced
- All Host & Load and Basic services
- Invoice audit and reconciliation
- Contract management
- Access to our Help Desk ticketing module
- Asset Management module
Clients provide their invoice information and desired services, and we create a tailored solution and pricing. We’re here to help you explore the right options for your goals and budget requirements.
A Few of the Driving Factors:
- Type of services: Telecom, IT, Wireless, or Utilities
- Number of locations: How many locations will we be managing?
- Annual dollar volume: The monthly fee is based on a percentage of your telecom and IT spend.
- Number of utility invoices: How many invoices will we receive and process?
- Wireless devices: How many devices will be under management?
Lastly, think about what services you want to take off your plate. Many clients need us to simply load the invoices and manage daily tasks like auditing, reconciling, and paying invoices. Enhanced Services allow you and your team to focus on core business tasks while we ensure all invoices are paid on time.
Why Choose Us?
Bringing unique value to the partnership is our key focus, and we differentiate our services, software, and problem-solving team in several ways:
- ExpenseLogic Software: Our in-house developed and maintained software can be tailored to any Business Intelligence needs.
- Combines eight software packages into one: accounting, expense audit, help desk, asset management, contract management, document management, wireless management, and reporting analytics.
- Enables seamless collaboration across finance, operations, facilities, and real estate departments.
- Invoice Reconciliation: We handle incorrect billing by disputing errors and recovering overcharges, shouldering the burden for you.
- High ROI: Our clients achieve an average ROI of over 400%.
- Effortless Onboarding: Our team manages vendor transitions and invoice setup seamlessly. Clients frequently commend our efficiency during this phase.
- Proven Experience: Over 33 years of expertise with continuous innovation. Our software is now in its 10th release.
- Exceptional Retention: Client retention exceeds 98% over the past six years, with many clients partnering with us for nearly two decades.
What’s Included in Your Investment?
- Custom-Tailored Solutions: We develop solutions specifically aligned with your goals and operational needs.
- Dedicated Problem-Solving Staff: Our team collaborates closely with your organization to address challenges and implement effective strategies.
- Seamless Collaboration: You’ll work directly with an experienced Account Team committed to understanding your business.
- Exceptional Post-Project Support: We remain available to answer questions, provide guidance, and ensure sustained success after implementation.
- Transparent Processes: We keep you informed every step of the way, ensuring clarity and confidence in the services provided.
- Focus on Your Business Needs: Our staff takes pride in proactively solving problems, offering innovative solutions, and adapting to the unique demands of your business environment.
Provide us with the services that are needed, and we will tailor a solution and pricing to meet those needs.
Client Testimonials
Our clients consistently praise our expertise, efficiency, and ability to deliver meaningful results. Here are just a few success stories:
Efficient Setup in 4 Weeks
“I cannot speak highly enough about your team. The RP team supported our team through managing the challenging vendor base, providing great guidance and all the necessary tools required for success. The implementation was FAST but also successful. Most implementations that go as fast as this have hiccups, and we had very few items to clean up after go live.”
Ease of Use
“The features provided are very helpful and the system is very user-friendly.”
Time-Saving
“I have been more organized than ever. My time is precious, and countless hours have been saved.”
Improved Vendor Management
“RadiusPoint has helped us streamline our vendor relationships and keep our expenses in check. Their team’s dedication to resolving disputes and ensuring accurate billing has saved us both time and money.”
Scalable Solutions
“As we expanded, RadiusPoint adapted seamlessly to our growing needs. Their tailored approach and comprehensive software have been invaluable.”
These testimonials demonstrate the trust our clients place in us and the results we deliver. Whether you need help managing a few locations or scaling solutions across a nationwide network, we’re here to help.
Ready to Learn More? Let’s Talk!
Contact us today for a no-pressure consultation. We’ll explore your needs and provide a customized plan that works for you. Visit us at Contact Us or Schedule a Discovery Call
2024 Gartner press release
For immediate release:
Orlando, FL November 27, 2024 – The 2024 Gartner Market Guide for Telecom Expense Management Services recognizes RadiusPoint as a Representative Vendor, affirming its position as a premier single-source SaaS platform and BPO service provider in the TEM services sector, a testament to its over three decades of market presence.
Gartner states, “To be commercially and operationally efficient, enterprises must eliminate service redundancy and ensure that all services add value to the business. TEM providers are offering program management capabilities to oversee fragmented estates spanning multiple carriers, lines of business, contracts and internal organizational units.”
When sourcing a TEM vendor, Gartner recommends best practices, “To increase the chances of a successful engagement, it is critical to conduct due diligence regarding what the provider will deliver and how that will be achieved.”
As a result of the ongoing advancements in the IT market, RadiusPoint is consistently enhancing the features and functionalities of its proprietary software, ExpenseLogic. RadiusPoint is committed to providing business intelligence, and ExpenseLogic empowers businesses to attain a favorable return on investment. Moreover, it helps transform the complexity of telecom management into streamlined efficiency while optimizing and reducing communication expenses, including IoT, mobile, fixed line, and cloud devices, as well as utility costs.
The success of businesses hinges on the precision and meticulous attention to detail required for technology and utility invoices and inventory every month. All financial transactions must be meticulously documented and systematically monitored, providing easy access for auditing and reporting through a unified platform. Alongside pinpointing costly billing errors, RadiusPoint’s exclusive software, ExpenseLogic, grants clients access to a range of Internet billing options that can be efficiently processed and managed within its IoT section. The flexibility of their service delivery enables RadiusPoint to adapt and scale as required.
“We are thankful to be included in Gartner’s Market Guide as a Representative Vendor, as we believe their key findings and recommendations are highly valued for enterprises of all sizes. Our flexibility and automation allow us to move faster and hold hands easier, said Sharon Watkins, CEO of RadiusPoint. “We believe Gartner provides clear evidence for those in the IT arena to make informed business decisions so you can focus on your core business strategy.”
Earning a place in the Gartner 2024 Market Guide for Telecom Expense Management Services represents a significant milestone for RadiusPoint and marks the sixth year of inclusion in this guide.
Subscribers to Gartner can find the 2024 Market Guide for Telecom Expense Management Services here.
Disclaimer: Gartner does not endorse any vendor, product, or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
About RadiusPoint
Established in 1992, RadiusPoint is a prominent provider of services encompassing Telecom Expense Management (TEM), Utility Expense Management (UEM), Wireless Expense Management (WEM), and Mobile Device Management (MDM). Located at its corporate headquarters in Orlando, Florida, RadiusPoint offers a comprehensive range of business and technology solutions, all aimed at enhancing the global business performance of its clients.
RadiusPoint is proud to be a 2025 SSON Sponsor
March 2025 –
We are thrilled to announce that RadiusPoint is a proud sponsor of the Shared Services Outsourcing Network (SSON) Orlando Conference taking place from March 24 – 27, 2025!
This premier event brings together the brightest minds in shared services and global business. It’s your chance to connect with industry leaders, gain insights from top experts, and network with peers who are shaping the future of our field.
Mark your calendars and make plans to join us in sunny Orlando for an unforgettable experience of learning, collaboration, and innovation. We look forward to seeing you there and sharing in the excitement of this incredible gathering!
Stay tuned for more updates and information as the event approaches. Let’s make SSON Orlando 2025 a standout occasion together!
Role of Utility Expense Management in Enhancing Sustainability
The Crucial Role of Utility Expense Management (UEM) in Enhancing Sustainability
In the pursuit of a more sustainable future, businesses and organizations are increasingly turning their attention to the management of utility expenses. Energy, water, and other utility costs not only impact the bottom line but also have significant environmental implications. By implementing effective utility expense management (UEM) strategies, businesses can reduce resource consumption, lower costs, and contribute to a more sustainable planet.
Understanding Utility Expense Management
Utility expense management involves the monitoring, analysis, and optimization of energy, water, and other utility costs within an organization. It encompasses various practices, including tracking usage patterns, identifying inefficiencies, implementing conservation measures, and leveraging technology to optimize resource consumption.
Benefits of UEM for Sustainability
- Reduced Environmental Impact: By actively managing utility expenses, organizations can identify areas of excessive resource consumption and implement measures to reduce waste. For example, businesses can significantly decrease their carbon footprint and conserve valuable natural resources by investing in energy-efficient appliances, optimizing heating and cooling systems, and minimizing water usage.
- Cost Savings: Effective utility expense management not only benefits the environment but also yields significant cost savings for businesses. By reducing energy and water consumption, organizations can lower their utility bills and allocate resources to other areas of operation. Additionally, many sustainability initiatives, such as installing solar panels or upgrading to energy-efficient lighting, may qualify for financial incentives and rebates, further enhancing cost savings.
- Enhanced Corporate Social Responsibility (CSR): Demonstrating a commitment to sustainability through responsible resource management can enhance an organization’s reputation and brand image. Consumers and stakeholders increasingly expect businesses to operate in an environmentally responsible manner. By actively managing utility expenses and reducing environmental impact, companies can strengthen their CSR initiatives and attract environmentally-conscious customers and investors.
- Regulatory Compliance: As governments worldwide enact stricter environmental regulations, businesses face increasing pressure to comply with sustainability standards. Effective utility expense management can help organizations meet regulatory requirements by reducing emissions, conserving resources, and adopting eco-friendly practices. By staying ahead of regulatory changes, businesses can avoid fines and penalties while positioning themselves as leaders in sustainability.
- Long-Term Resilience: Investing in sustainability through utility expense management fosters long-term resilience for businesses. By reducing reliance on finite resources and minimizing exposure to volatile energy markets, organizations can mitigate risks associated with resource scarcity and price fluctuations. Embracing sustainability also future-proofs businesses against evolving consumer preferences and regulatory trends, ensuring continued relevance and competitiveness in a rapidly changing world.
Best Practices for Utility Expense Management
- Conducting Regular Audits: Regularly assess utility bills, meter readings, and consumption patterns to identify areas of inefficiency and opportunities for improvement.
- Implementing Energy-saving Technologies: Invest in energy-efficient appliances, lighting systems, and HVAC equipment to reduce energy consumption and lower utility costs.
- Employee Engagement: Educate employees about the importance of resource conservation and encourage participation in sustainability initiatives through training programs and incentive schemes.
- Leveraging Technology: Utilize energy management software, smart meters, and IoT devices to monitor and control utility usage in real time, enabling proactive decision-making and optimization.
- Setting Targets and KPIs: Establish clear sustainability goals, such as reducing energy consumption by a certain percentage or achieving specific emissions targets, and track progress using key performance indicators (KPIs).
Conclusion
Effective UEMt is a cornerstone of sustainable business practices, offering environmental, economic, and social benefits. By optimizing resource consumption, reducing costs, and demonstrating a commitment to environmental stewardship, organizations can enhance their competitiveness, strengthen their brand reputation, and contribute to a more sustainable future for generations to come. Embracing sustainability through utility expense management is not only a strategic imperative but also a moral obligation in the face of global environmental challenges.
Factors That Impede Your Inventory Efforts
Factors That Impede Your Inventory Efforts
Creating and maintaining an inventory of your telecommunications services, invoices, and vendors is a substantial undertaking that demands consistent attention to detail. Ensuring the cleanliness and accuracy of this inventory is a challenging task, often requiring dedicated daily efforts. Engaging the services of a Telecom Expense Management (TEM) company is essential in effectively managing these tasks.
Many organizations opt to outsource the periodic inventory assessment of their telecom services and invoices. While some may view this as a sporadic necessity, often with a minimal financial benefit, a more strategic approach suggests otherwise. Rather than periodic assessments, an audit encompassing a comprehensive inventory conducted once, followed by regular maintenance, offers a more pragmatic solution.
The practicality of maintaining a clean inventory on an ongoing basis is often hindered by time constraints within most companies. However, partnering with a reputable TEM provider enables the execution of this task every month. This proactive approach not only mitigates the risks of overbilling but also streamlines the recovery process for any erroneous charges. Additionally, any recovered funds resulting from the initial audit can be efficiently managed and shared, maximizing overall savings and efficiency.
Challenges in Maintaining an Accurate Inventory of Telecom Services
Many factors contribute to an organization needing help maintaining an accurate inventory.
- Absence of Corporate Contracts: When corporate contracts are lacking, employees may independently enter into agreements, resulting in higher service costs.
- Decentralized Spending: This occurs when employees make equipment purchases without organizational oversight, leading to inefficiencies.
- Inaccurate Inventory: Without proper tracking of telecom and IT services at each location and for each employee, overspending is likely due to duplicate or unnecessary services.
Addressing these factors is crucial for effective inventory management of telecom services. Implementing corporate policies and contracts can help control spending. Engaging a reputable Telecom Expense Management (TEM) company is the initial step in assessing service distribution through a comprehensive Inventory and Audit. This process necessitates a thorough examination of services beyond superficial refunds, providing detailed descriptions of phone or circuit numbers, monthly charges, service types, and features.
Enhancing Cost Reduction Strategies with Comprehensive TEM Solutions
Upon establishing an accurate inventory, a Telecom Expense Management (TEM) system empowers organizations to consistently drive cost reductions by offering comprehensive visibility into their communication ecosystem and invoice lifecycles. Centralizing all telecom-related data in a unified repository, accompanied by robust reporting tools, facilitates precise cost assessments, aids in identifying and disputing billing discrepancies, streamlines contract management including contract imaging and auditing, and uncovers optimization opportunities. Additionally, capacity planning and call accounting functionalities mitigate resource wastage within the network.
This goes beyond just telecom. A good TEM vendor will provide a comprehensive cost reduction management strategy that includes both telecom and IT, managing the complete communications lifecycle. The accuracy behind these transactions is vital to the overall efficacy of the organization.
Steps to Maintain a Clean Inventory
Keeping the inventory clean will be affected by the following:
- Monthly services being added.
- Monthly services being disconnected.
- Employees moving to different departments, being hired or terminated.
- Vendor’s changes in monthly fees.
To maintain a clean inventory every month, it is imperative to establish an order process that fosters transparency throughout the organization. Integration of a Help Desk module within the TEM provider’s software is instrumental in capturing all moves, additions, changes, or disconnects effectively. This ensures a seamless transition of new invoices to accounting without delay for coding, thereby preventing overpayment for previously disconnected services.
The next critical step in maintaining inventory accuracy is invoice and service validation. Conducting a monthly audit of each invoice and charge is essential for any TEM company. This line-item audit enables prompt identification of overcharges and provides an efficient mechanism to notify vendors for dispute and recovery. Rigorous tracking of disputes to ensure proper crediting on invoices is paramount in the recovery process facilitated by TEM services.
Optimizing Inventory Accuracy
Maintaining the accuracy of your monthly inventory relies heavily on verifying it against the established baseline inventory. A reputable TEM provider should offer validation services with select telecom vendors, enabling swift identification and rectification of discrepancies to prevent recurring overcharges on subsequent invoices.
Leveraging its proprietary SAAS platform, ExpenseLogic, RadiusPoint facilitates the creation of a concise list of invoices and services for monthly validation against the baseline inventory. This validation process provides organizations with a clear overview of services at each location, streamlining interactions with telecom vendors and pinpointing opportunities for cost reduction by identifying unnecessary services. Partnering with the right TEM provider can significantly save time, money, and resources while empowering internal teams to take control of expenses.
Diving Into Your Trash
Waste management stands as a sizable industry that is essential for every company. In the United States alone, a staggering 624,700 metric tons of trash get discarded daily, incurring an annual expense of approximately $11 billion. Businesses shoulder a substantial 80% of these expenses. Across the board, companies are actively seeking strategies to curtail costs while simultaneously minimizing waste generation and maximizing recycling opportunities wherever feasible.
Invoices and Fees
The initial phase of cost reduction in waste management involves scrutinizing usage patterns and existing services. Numerous companies grapple with expensive monthly waste services, often burdened by additional charges appended to their regular service bills. These fees often include:
- Management fees
- Environmental fees
- Gas surcharge fees
- Lock fees
- Extra Pick-up fees
- Contamination fees
- Overage fees
- Locked gate fees
By comprehending the invoice details and extra fees, you can effectively optimize your cost savings.
Questions to Ask
Some of the above fees can be eliminated or negotiated just by asking the right questions including:
- Do we need a separate bin for environmental waste? This could involve quick-service restaurants discarding spoiled food or spent grease.
- Can we recycle cardboard, plastic, and metal? Breaking down boxes for recycling might save both money and the environment.
- Is there a vendor we can use to collect scrap metal? This move could cut costs for larger roll-off bins and potentially lead to rebates.
- Are any bins situated behind locked gates? If trash collection is hindered due to inaccessibility, expect additional fees. To avoid this, place bins outside locked areas or coordinate gate access on pickup days.
- Are extra pickup fees a routine on your invoices? A quick review of the invoice can help resolve this by adjusting bin size or pickup frequency.
- Is there a corporate contract governing waste services? Ensure your team is aware of this contract to benefit from agreed-upon rates when ordering services.
Given the array of questions, it’s evident that most companies will require support in overseeing trash invoices and managing multiple service providers. Generating detailed, precise information crucial for optimal business decisions demands dedicated time and meticulous attention to detail from a skilled team.
Problems with Billing Complexity
The billing intricacies present a convoluted mix of charges that necessitate monthly and long-term analysis to pinpoint the most optimal services at the most favorable prices. Monthly invoices might vary, with additional charges appearing one month and none the next, leading to potential confusion. It’s crucial to meticulously identify each charge on the invoice every month to ensure informed business decisions for each location.
Vendors contribute to this complexity by offering multiple trash haulers within a single area. This approach proves more advantageous than having only one hauler since multiple options enable bidding and price competition. However, managing these multiple vendors requires a dedicated effort and a specific finesse to navigate pricing and negotiate contract terms effectively.
Optimization Solutions with RadiusPoint
Having a partner who can break down the invoice monthly is critical to effectively managing your trash or waste services and meeting your sustainability goals. RadiusPoint’s Waste Optimization process involves a deep dive into the waste invoices and current business programs and policies to provide a multi-point approach to managing waste services. This inventory and audit process delivers an environmentally responsible waste management program that assists in reaching waste initiatives and provides unmatched value.
RadiusPoint’s optimization involves investigating services with the current vendor and determining best practices to provide a cost-saving program to our clients. Many multi-location organizations have ordered services as needed with no thought given to contract terms, bin size, or the frequency of pick-up. All of these factors determine the monthly cost and could result in huge savings if managed with cost savings, efficiency, and program goals in mind.
During our inventory and audit of the waste services, RadiusPoint would:
- Obtain a copy of the vendor’s current contract.
- Validate the contract rates against the current invoice.
- Comparison of services across all sites for any anomalies.
- Identifying any overage charges or other charges beyond the normal pick-up charges.
- Identifying better rates for those locations not under contract.
- Identifying better rates and possible early termination penalties, if applicable, for those locations under contract.
- Identify and recommend service changes to eliminate overage charges.
- Provided consolidated report for Request for Proposal (RFP).
- Provide analysis once the RFP is returned to show savings.
- Assist with contract negotiations for each contract or global contract.
- Assist with issues that arise at the location during the term of the agreement.
Once the inventory and audit is complete, RadiusPoint employs our exclusive software, ExpenseLogic, to handle and settle the monthly invoice. Simultaneously, continued auditing is conducted to guarantee precise billing according to contracted rates.
Connect with us to learn how RadiusPoint will support you in achieving your business’s waste service savings goals.
Why Your Company Needs a Managed Mobility Service Provider
The Strategic Imperative: Why Your Company Needs a Managed Mobility Service Provider
Is your company struggling to keep up with the rapidly evolving mobile landscape?
Are you overwhelmed by the complexities of managing a growing number of mobile devices and applications?
If so, it’s time to consider partnering with a managed mobility service provider. In this article, we will explore why your company needs the expertise of a managed mobility service provider to stay ahead of the game.
With the proliferation of smartphones, tablets, and other mobile devices, organizations are facing a multitude of challenges when it comes to managing their mobile ecosystem.
From device procurement and provisioning to security and support, there are numerous tasks that need to be handled efficiently and effectively. A managed mobility service provider can help streamline these processes, allowing your company to focus on its core competencies.
By leveraging the expertise of a managed mobility service provider, you can ensure that your company’s mobile infrastructure is optimized for productivity and cost-effectiveness.
These providers have the knowledge and experience to implement best practices, ensuring that your mobile devices and applications are secure, up-to-date, and fully utilized.
Don’t let your company fall behind in the mobile revolution. Partner with a managed mobility service provider and stay ahead of the game.
Benefits of partnering with a managed mobility service provider
Managing a growing number of mobile devices and applications can be a daunting task for companies of all sizes. The complexities involved in device procurement, provisioning, security, and support can quickly become overwhelming.
Without the right expertise and resources, companies may struggle to effectively manage their mobile ecosystem. This is where a managed mobility service provider can make a significant difference.
How a managed mobility service provider can help optimize your company’s mobility strategy?
1. Expertise and Knowledge
Managed mobility service providers specialize in the management of mobile devices and applications. They have the expertise and knowledge to navigate the complexities of the mobile landscape, ensuring that your company’s mobile infrastructure is optimized for success.
2. Cost Savings
By partnering with a managed mobility service provider, you can reduce the total cost of ownership of your mobile devices. These providers have the resources and relationships to negotiate favorable pricing for device procurement and support services.
Additionally, they can help you identify and eliminate unnecessary expenses, saving your company money in the long run.
3. Enhanced Security
Mobile devices are vulnerable to security threats, making it essential to have robust security measures in place.
Managed mobility service providers have the expertise to implement comprehensive security solutions, protecting your company’s sensitive data and mitigating the risk of cyberattacks.
4. Streamlined Processes
Managing a large number of mobile devices and applications can be time-consuming and resource-intensive. A managed mobility service provider can streamline these processes, automating tasks such as device provisioning, software updates, and application deployment.
This allows your IT team to focus on more strategic initiatives, improving overall efficiency and productivity.
Key features to look for in a managed mobility service provider
When choosing a managed mobility service provider, it’s essential to consider the following key features:
5. Expertise and Experience
Look for a provider with extensive experience in managing mobile devices and applications. They should have a proven track record of success and a deep understanding of industry best practices.
6. Comprehensive Service Offering
Ensure that the provider offers a comprehensive range of services, including device management, application management, security, and expense management. This will ensure that all aspects of your company’s mobile ecosystem are covered.
7. Scalability
Consider the scalability of the provider’s services. Your company’s mobile needs may grow and evolve, so it’s important to choose a provider that can scale its services to accommodate future requirements.
8. Robust Security Measures
Mobile security is of paramount importance. Choose a provider that has robust security measures in place, including encryption, two-factor authentication, and mobile threat defense.
9. Flexibility and Customization
Every company has unique mobility requirements. Look for a provider that offers flexible and customizable solutions to meet your specific needs. They should be willing to work closely with you to understand your business objectives and tailor their services accordingly.
The value of investing in a managed mobility service provider for your company’s success
Managed mobility services will continue to play a vital role in helping companies navigate the ever-changing mobile landscape. As technology advances and new challenges emerge, the expertise of managed mobility service providers will become even more valuable.
With the increasing adoption of IoT devices, the rise of 5G networks, and the growing need for enhanced security, companies will rely on these providers to optimize their mobility strategies and ensure their competitive edge.
RadiusPoint Recognized as a Distinguished Vendor in the 2024 Amalgam Insights Vendor SmartList
For immediate release:
Orlando, FL January 23rd, 2024 – RadiusPoint, a renowned name in the Technology Expense Management (TEM) services sector, proudly announces its recognition as a Distinguished Vendor in the 2024 Amalgam Insights Vendor SmartList. The SmartList, themed “Why TEM Matters More Than Ever in a Cloud, SaaS, and AI World,” serves as a testament to RadiusPoint’s exceptional contributions and expertise in the industry.
Amalgam Insights, a trusted source for technology insights, has distinguished RadiusPoint as a standout performer in the TEM landscape. This recognition reflects RadiusPoint’s position as a premier single-source SaaS platform and Business Process Outsourcing (BPO) service provider. With over three decades of unwavering commitment to excellence, RadiusPoint continues to lead the way in delivering innovative solutions that align with the evolving needs of a Cloud, SaaS, and AI-driven world.
Amalgam Insights states; “Organizations seeking to contextualize telecom, mobility, and IT spend with broader accounting activity, including facilities visibility and ESG reporting, are best positioned to get the most value from RadiusPoint. As companies worldwide emphasize spending accountability within all divisions and, at the same time, require metrics for their social responsibility efforts, they must think beyond managing disciplines in a siloed fashion. Combining telecom, mobility, IT, and facilities administration into a single practice delivers holistic insight while improving productivity, efficiency, and costs,”
“We are honored to be recognized by Amalgam Insights as a Distinguished Vendor in their prestigious Vendor SmartList,” said Sharon Watkins, CEO at RadiusPoint. “This acknowledgment underscores our dedication to providing cutting-edge TEM services and reinforces our commitment to delivering value to our clients in an ever-changing technological landscape.”
RadiusPoint expresses gratitude to Amalgam Insights for this distinguished recognition and looks forward to continuing its mission of excellence in the TEM services sector.
To learn more about Amalgam Insights, please visit their website here.
The full Amalgam Insights Vendor SmartList is available to download here.
About RadiusPoint
RadiusPoint is a leading provider of Technology Expense Management (TEM) services, offering a comprehensive suite of solutions to manage, optimize, and control technology expenses. With over 30 years of industry experience, RadiusPoint is committed to delivering innovative and cost-effective TEM services in a rapidly evolving technology landscape.
Waste Services Case Study: 28% Reduction in Trash Spend
28% Reduction in Trash Spend
Trimming expenses on waste management serves as the initial step in an organization’s sustainability journey. A prominent elevator company operating worldwide successfully slashed its monthly waste expenditure by 28%. Additionally, by securing a corporate contract, they paved the way for greater savings across their new locations, fortifying their commitment to sustainability.
Issues
Our client grappled with numerous challenges in its billing and services. Upon conducting an initial review, it became evident that over 40 locations had individually inked contracts with local waste haulers. Consequently, these contracts staggered in expiration, often incurring hefty early termination fees. This complexity rendered negotiating a unified corporate contract unfeasible within the initial twelve months of gaining contract and service visibility.
Solution
To tackle these issues, the organization teamed up with RadiusPoint. Collaborating on bill processing and payment services for their monthly waste invoices, RadiusPoint unearthed a route toward cost reduction during the standard optimization process.
RadiusPoint’s optimization process delved into scrutinizing services provided by the existing vendor, aiming to uncover contractual obligations and service specifics. Numerous locations had ordered services sporadically without considering contract terms, bin sizes, or pickup frequency. RadiusPoint conducted a comprehensive analysis across the organization, tailoring services to match the office types and specific service requirements to ensure an appropriate fit.
During our inventory and audit of the waste services, RadiusPoint:
- Obtained a copy of the vendor’s current contract.
- Validated the contract rates against the current invoice.
- Compared services across all sites for any anomalies.
- Identified overage charges or other charges beyond the normal pick-up charges.
- Identified better rates for those locations not under contract.
- Identified better rates and possible early termination penalties, if applicable, for those locations under contract
- Recommend service changes to eliminate overage charges.
- Provided consolidated report for Request for Proposal (RFP).
- Provided analysis once RFP is returned to show savings.
- Assisted with contract negotiations for each contract or global contract.
- Managed the transition project.
- Assisted with issues that arose at the location during the term of the agreement.
Results
Partnering with RadiusPoint empowered the client to leverage our exclusive software, ExpenseLogic. This tool facilitated the seamless processing and payment of monthly invoices while concurrently conducting an audit to guarantee precise billing per contracted rates. This meticulous approach culminated in an impressive 28% decrease in monthly waste expenses. Embracing transparency in management paves the way for astute business choices, fostering cost-effectiveness, operational efficiency, and the achievement of sustainability objectives. Entrust RadiusPoint to guide you toward attaining your business savings targets, specifically with your waste services.
The Future of Cost Optimization: TEM Services are Leading the Way
How RadiusPoint Telecom Expense Management Services are Leading the Way
As RadiusPoint Telecom Expense Management (TEM) services continue to revolutionize cost optimization in the telecom industry, businesses are now equipped with the tools they need to stay ahead of the game. With its cutting-edge technology and innovative solutions, RadiusPoint has positioned itself as a leader in helping companies streamline their telecom expenses while achieving significant cost savings.
In this article, we will delve into the future of cost optimization and how RadiusPoint TEM services are paving the way for businesses to optimize their telecom expenses like never before. By leveraging their extensive experience and industry knowledge, RadiusPoint provides customized solutions tailored to each client’s unique needs.
With cost optimization becoming increasingly crucial in today’s competitive landscape, businesses need a reliable partner like RadiusPoint to navigate the complexities of managing telecom expenses. Their proactive approach, coupled with their innovative software, helps businesses identify potential areas of cost savings and implement effective strategies to optimize their telecom spend.
Stay tuned as we explore how RadiusPoint TEM services are leading the way in cost optimization and discover how your business can benefit from their expertise.
The challenges of cost optimization in telecom expenses
Cost optimization plays a vital role in the success of any business. In today’s highly competitive market, where every penny counts, companies are constantly seeking ways to reduce expenses and increase profitability. Telecom expenses, in particular, can be a significant drain on a company’s resources. With the increasing reliance on telecommunications for business operations, companies must optimize telecom spend to remain competitive.
Effective cost optimization allows businesses to allocate their resources efficiently, ensuring that every dollar spent delivers maximum value. By identifying and eliminating unnecessary expenses, businesses can free up capital for investments in growth opportunities, product development, and innovation. Cost optimization also helps businesses improve their bottom line, increase profitability, and enhance their overall financial health.
How RadiusPoint’s TEM services work
Cost optimization in telecom expenses presents unique challenges for businesses. The telecom industry is complex, with multiple service providers, various billing structures, and a wide range of services and technologies. Managing and controlling telecom expenses can be a daunting task, especially for businesses with multiple locations or a large number of employees.
One of the main challenges in TEM is the lack of visibility into telecom spend. Without a centralized system to track and monitor expenses, businesses may struggle to identify inefficiencies and cost-saving opportunities. Additionally, the ever-evolving nature of the telecom industry means that businesses need to stay up-to-date with the latest technologies, services, and pricing plans to ensure they are getting the best value for their money.
Another challenge is the complexity of telecom invoices. Telecom bills can be confusing, with multiple line items, different rates, and various fees and surcharges. Without a thorough understanding of telecom billing, businesses may miss out on potential cost-saving opportunities or fall victim to billing errors and overcharges.
Key features of RadiusPoint’s TEM services
RadiusPoint’s TEM services offer a range of key features that set them apart from other TEM providers. These features include:
- Invoice Processing and Auditing: RadiusPoint’s proprietary software, ExpenseLogic, automates the invoice processing and auditing process, ensuring accurate and timely payment of telecom bills. This eliminates the need for manual invoice processing, reduces the risk of errors, and improves overall efficiency.
- Expense Tracking and Reporting: ExpenseLogic provides real-time visibility into telecom expenses, allowing businesses to track costs, monitor usage, and generate detailed reports. This helps businesses make informed decisions, identify cost-saving opportunities, and optimize their telecom spend.
- Contract and Vendor Management: RadiusPoint helps businesses manage telecom contracts and relationships with service providers. They negotiate favorable contract terms, monitor contract compliance, and ensure that businesses are getting the best value for their money.
- Cost Allocation and Chargeback: ExpenseLogic enables businesses to allocate telecom expenses to different cost centers or departments, making tracking and managing telecom spending across the organization easier. This feature is particularly useful for businesses with multiple locations or complex organizational structures
The benefits of outsourcing telecom expense management services
RadiusPoint has helped numerous businesses achieve significant cost savings through their TEM services. Let’s take a look at a few real-life success stories:
- RadiusPoint assisted a multi-location nonprofit by identifying the existing local telecom service utilized across six locations, meeting specific landline requirements. They successfully identified all needs and found a superior service at a reduced monthly cost, resulting in a $12K reduction in total monthly expenses across the six locations.
- RadiusPoint’s software, ExpenseLogic, found a contract overcharge on local phone lines for a discount retailer, ongoing for months. RadiusPoint collaborated with the carrier to secure an $82K credit and prevent a $12,000 monthly expense.
- ExpenseLogic discovered services billed for three months despite being closed and disconnected for a restaurant group. RadiusPoint collaborated with the vendor, resulting in a $5,761 credit from the vendor.
The future of cost optimization in TEM
Outsourcing telecom expense management to RadiusPoint offers several key benefits for businesses:
- Expertise and Industry Knowledge: RadiusPoint’s team of experts has extensive experience in the telecom industry. They are well-versed in the latest technologies, services, and pricing plans, enabling them to provide valuable insights and recommendations to optimize telecom expenses.
- Time and Resource Savings: Managing telecom expenses in-house can be a time-consuming and resource-intensive task. By outsourcing to RadiusPoint, businesses can free up their internal resources and focus on core business activities, while leaving the complexities of TEM to the experts.
- Cost Savings: RadiusPoint’s cost optimization strategies and negotiation skills help businesses achieve significant cost savings. By identifying inefficiencies, eliminating unnecessary expenses, and negotiating better rates, businesses can reduce their telecom spend and improve their bottom line.
- Improved Visibility and Control: ExpenseLogic provides businesses with real-time visibility into their telecom expenses, allowing them to track costs, monitor usage, and generate detailed reports. This improved visibility and control enable businesses to make informed decisions, identify cost-saving opportunities, and optimize their telecom spend.
How RadiusPoint is leading the way in telecom expense management services
The future of cost optimization in telecom expenses looks promising, with technological advancements and the rise of innovative solutions. As businesses continue to rely on telecommunications for their operations, the need for effective cost optimization will only grow.
One key trend in cost optimization is the increasing use of artificial intelligence (AI) and machine learning (ML) technologies. These technologies can analyze large volumes of data, identify patterns, and make intelligent recommendations for cost savings. By leveraging AI and ML, businesses can automate the process of identifying cost-saving opportunities and implementing optimization strategies.
Another trend is the integration of TEM with other business systems. By integrating TEM with enterprise resource planning (ERP) systems, businesses can gain a holistic view of their expenses and improve overall cost control. This integration allows for better coordination between different departments and ensures that telecom expenses are aligned with business objectives.
Conclusion
RadiusPoint is at the forefront of telecom expense management services, leading the way in cost optimization for businesses. Their innovative EXpenseLogic software, experienced team, and customer-centric approach set them apart from other providers in the industry.
RadiusPoint’s proactive approach to cost optimization helps businesses stay ahead of the game. They continuously monitor the telecom industry for new technologies, services, and pricing plans, ensuring that their clients are getting the best value for their money. Their team of experts works closely with clients to understand their unique needs and develop customized cost-optimization strategies that deliver tangible results.
By leveraging RadiusPoint’s expertise and innovative software, businesses can streamline their telecom expenses, identify cost-saving opportunities, and implement effective strategies to optimize their telecom spend.
Healthcare Case Study: Telecom Expenses Down by 26% in Healthcare
Reducing Telecom Expenses by 26% in Healthcare
RadiusPoint collaborated with an Assisted Living and Nursing Home organization to enhance their oversight of telecom, IT, and wireless expenses. Serving as their telecom expense management (TEM) partner, RadiusPoint offered comprehensive insight into their invoices and spending and the range of services and equipment deployed across each site. This detailed visibility enabled RadiusPoint to identify and deactivate over 700 dormant business lines at various locations leading to a 26% reduction of their annual spend or $475k once the lines were disconnected and removed from the invoices.
Background
Given the healthcare industry’s focus on emergency preparedness, there’s a constant demand for reliable access to emergency personnel. Landlines play a critical role in ensuring immediate response in case of facility emergencies. Each location is mandated to have two copper lines for direct fire notification, with the option to add more lines for direct point-to-point access to the fire department. Safety for patients and staff is the top priority for this organization, necessitating RadiusPoint to meticulously validate vendor-provided information at every site.
Issues
The organization lacked previous inventory and audits of its telecom, IT, and wireless services. The service introduced detailed identification of each service type on vendor invoices, outlining all features, fees, taxes, and surcharges billed for each phone number. Various telecom vendors used different billing formats, with some providing only the total amount due without specific service descriptions or associated phone numbers. This limited visibility hindered effective decision-making regarding service removal or cost reduction through optimization.
As the costs of regular business lines escalated with vendors, the organization faced pressure to cut expenses. However, stringent regulations and safety protocols concerning patient well-being posed a challenge. Over the past two years, regular business line costs surged significantly, soaring from $50.00 to over $200.00 per line. Although newer, more cost-effective technology existed, regulatory restrictions prevented its use for regular business lines, prioritizing security measures.
Solution
RadiusPoint conducted an audit and inventory, yielding crucial information for eliminating unnecessary lines. This initiative validated services and phone lines across all sites, uncovering errors and overcharges in invoices. Some invoices continued to bill for services canceled years ago, obscured by invoice complexity or consolidation. RadiusPoint’s scrutiny pinpointed erroneous charges like features and taxes on phone lines canceled five years prior, prompting requests for credits from the vendor. In one case, even after an account was disconnected, circuits associated with it continued to bill due to a failed disconnection request.
The inventory and audit process began by verifying each phone line’s use through multiple calls and on-site visits for lines without responses. This process revealed over 700 unused regular business lines, some unconnected even in the phone rooms at various locations. Additionally, RadiusPoint offered recommendations to reduce line counts and optimize necessary lines. This enhanced visibility into remaining monthly expenses, enabling contract negotiations with vendors, and resulting in a further 10% cost reduction.
Results
Now equipped with ExpenseLogic, RadiusPoint’s proprietary software, this organization possesses comprehensive visibility into its telecom invoices and a complete inventory management system. In the Site Manager section of ExpenseLogic, a single click grants their team access to detailed invoice images, individual phone lines, circuits, wireless numbers, service features, and monthly costs for each location. Their annual savings exceeding $500k, alongside the elimination of 700 unnecessary lines, have led to reduced costs, improved services, and heightened accuracy in their monthly telecom billing.
Fraud Case Study: Tales of Fraud in the IT Department
Tales of Fraud in the IT Department
Fraud is a significant concern for organizations, with reported cases and financial losses steadily increasing according to the Federal Trade Commission. In 2021, consumers reported losses exceeding $5.8 billion, a staggering 70% increase from the previous year. 2022 numbers are still being calculated, but the trend of rising fraud cases persists annually.
Employee fraud spans various forms, ranging from small instances like expense report manipulation to larger-scale embezzlement. Instances of fraud can persist over extended periods, leaving businesses perplexed about its onset and duration. Often, fraudsters are caught not by the act itself, but due to their escalating greed for increased gains.
RadiusPoint, specializing in Telecom and Utility Expense Management, has encountered numerous instances of fraud. Some cases have been proven and prosecuted by authorities, while in others, suspicions of employee fraud have led to discreet dismissals once RadiusPoint delves into telecom and IT expenses and contracts. The company has also provided documentation and insights to prevent fraud within IT departments or telecom services.
What Kind of Fraud Can Be Lurking in Your IT Department?
Wireless device usage continues to surge annually, fueled by wearable devices and remote work policies that often provide employees with wireless phones, iPads, or similar devices. For large organizations, adding wireless devices is routine, facilitated by negotiated contracts offering discounted purchases and waivers for early termination fees.
In a striking case, RadiusPoint uncovered internal fraud amounting to over $350k tied to monthly wireless device purchases at a healthcare organization. An IT employee exploited the system by purchasing Apple iPhones and iPads through the company account, setting up monthly services under the corporate account, and then selling these devices for personal gain. The scheme involved ordering devices, arranging services, and coding the costs to a specific Cost Center with the manager’s approval. The employee then canceled these accounts without incurring early termination fees, leveraging the negotiated contract terms. The fraudulent activity went unnoticed until RadiusPoint raised concerns about unassigned devices and an outsider inquiring about the excessive device offloading. More than 700 devices were ordered in a short span, resulting in losses for the company, including device costs, the first month’s service, and the ETF. The case gained traction with the involvement of the Department of Justice, leading to the prosecution of the former employee.
Another form of fraud, albeit harder to substantiate, involves a recurring pattern where the approving party consistently selects the same vendor for significant contracts and receives kickbacks in return. This type of fraud poses challenges in proof and often leads to the discreet dismissal of the involved employee. In a recent case of this form of fraud, RadiusPoint conducted an audit for a multi-location healthcare equipment organization, examining data circuits, invoices, and contracts. This revealed multiple contract violations spanning various years and locations, encompassing data circuits, Sonet rings across cities, and an MPLS platform. Initially, the audit led to recovering $300K in contract violations and overcharges from the vendor. Subsequent audits expanded to other services and contracts, uncovering an additional $250K in discrepancies. The employee responsible for negotiating and approving these contracts discreetly vanished from the company.
How Can You Bolster your IT Department’s Defenses Against Fraud?
Establishing a standardized workflow would have significantly mitigated fraud and theft risks. However, several additional policies could reinforce the legitimacy of vendor orders:
- Implementing a uniform Workflow for ordering new services.
- Mandating cost center and individual assignments on vendor order forms.
- Introducing a secondary approval process for equipment orders.
- Verifying equipment purchases through monthly reporting by your TEM provider.
- Ensuring monthly documentation from vendors for new equipment or services approval.
- Sending RFPs to multiple vendors for side-by-side evaluations of proposals.
- Sharing agreed-upon contract rates with the team handling monthly invoice validation.
- Requiring Quarterly Business Reviews to validate billed rates accuracy.
While no plan is foolproof, adhering to specific purchasing and contracting policies can significantly diminish the risk of fraud. RadiusPoint can assist by scrutinizing your invoices and contracts for any potential concerns.
UEM Collaboration Saves Over $1 Million
UEM Collaboration Saves National Home Builder Over $1 Million
RadiusPoint recently collaborated with a national home builder to simplify the process of utility ordering and ensuring installations for more than 5,000 new home projects yearly. During this collaboration, RadiusPoint uncovered monthly billing exceeding $25,000 for homes sold two years earlier and identified over $100,000 in refunds from vendors holding funds for closed locations. The anticipated annual cost savings for this client are estimated to surpass $1 million, based solely on the initial six months of RadiusPoint’s services.
Background
A national home builder faced significant challenges in various areas, particularly in handling utility vendors, invoices, and expenses. With multiple divisions under corporate management and an annual workload of over 5,000 new home projects, each division independently managed meter installations but directed the resulting invoices to the corporate office for payment. This decentralized process led to numerous problems, including multiple service outages that required division intervention to restore services.
Issues
The initial challenge for the home builder revolved around service setup. Several individuals in each division handled order placements, causing delays in meter installation and service initiation, consequently impacting the start of construction projects. Additionally, the lack of a standardized process and the involvement of multiple individuals led to vendors not sending invoices to the corporate office. Often, invoices were mistakenly delivered to empty lots without mailboxes, resulting in returns. Subsequently, vendors would disconnect services, further delaying the work of trade workers on the homes. These complications collectively resulted in significant losses, amounting to thousands of dollars due to decreased productivity.
The subsequent problem concerned accurately tracking expenses related to meter usage. Typically, builders assign charges for individual homes to different accounting codes, enabling corporate oversight across various completion stages. This accounting system also offers insights into the completion date and turnover to the Sales department. However, while the corporate office had a daily method for monitoring home progress and stages, there was no established process to align this information with monthly utility expenses.
Adding to the list of issues was the discontinuation of services after home sales. Although each division was responsible for disconnecting services, this task was often neglected. The process of transferring services to the new homeowner’s name relied on the homeowner, but due to consistent confusion around final permit approvals and multiple contacts required with the vendor, ensuring that the homeowner completed this step was frequently overlooked.
Solutions
Service Order Placement
In their initial interaction with the Accounts Payable department, RadiusPoint pinpointed various issues that could be resolved through their Invoice Processing services, offering improved invoice management and cost allocation. While assessing the current service order process, RadiusPoint identified a fundamental issue underlying most of the problems faced. Leveraging their proprietary software, ExpenseLogic, the RadiusPoint team developed a streamlined service order process for each division. This involved creating a customized order form tailored to the builder’s requirements. The form also featured a link accessible on the builder’s tablet, enabling on-site service order placements.
Another valuable feature contributing to the process streamlining was the capability for the builder and their team to include permits or necessary documents when placing orders with utility vendors for future needs. Many utility vendors require a city government-issued permit before setting up a meter at a property. RadiusPoint incorporated this ability to attach documents to the order forms tailored for each builder’s requirements. These documents are centralized in the Site Manager Dashboard within ExpenseLogic, ensuring easy access not only for the division but also for anyone within the corporate structure. This customized addition significantly reduced the hours spent searching for documents previously held by one individual.
Timely order placement and ensuring prompt meter setups were crucial, and RadiusPoint facilitated this by collaborating with vendors through ExpenseLogic’s Moves, Adds, Changes & Disconnect (MACD) module. This module provided comprehensive tracking of the ordering process and seamlessly connected with the Invoice Processing section to guarantee proper invoice setup and allocation to the correct Cost Center, ready for the first invoice. One significant corporate benefit was the RadiusPoint team’s ability to track missing invoices. Daily Missing Bill reports were generated to identify vendor invoices that hadn’t been received. RadiusPoint then contacted the vendors to retrieve and process these invoices. Prior to RadiusPoint’s involvement, missing invoices could result in the property receiving the invoice after service disconnection, causing site downtime and productivity loss.
Proper Accounting and Allocation
ExpenseLogic functions as comprehensive accounting software, enabling the allocation of invoices to Cost Centers or project codes. Leveraging the builder’s daily report illustrating the 12 stages of home completion, RadiusPoint easily devised a solution for accurate allocation. They implemented a daily import system into ExpenseLogic, aligning Cost Centers with invoice expenses. This method ensured precise monthly expense allocation corresponding to each home’s building stage, facilitating accurate chargebacks and providing enhanced visibility into expenses. Additionally, it offered improved forecasting capabilities for total costs, adding value to the process.
Disconnecting Utility Services
One frequently overlooked aspect was the essential follow-up required after home sales. Divisions were responsible for contacting the vendor two weeks post-sale to confirm the new homeowner’s transfer of electric, gas, and water services into their name. Due to difficulties in tracking the home-building stage, these follow-ups often slipped through the cracks. Compounding the issue, vendors sometimes hesitate to change the account name due to pending permits or final inspections, necessitating additional follow-ups after inspection completion. Failures in inspections further prolonged the process. These hurdles transformed what should have been straightforward into a complicated and time-consuming procedure.
RadiusPoint established a clear timeline for vendor follow-up. By utilizing the MACD module in ExpenseLogic for service orders, the follow-up, including any required documentation, became more efficient. With all stages meticulously tracked, upon receiving subsequent invoices, RadiusPoint ensured the final bill accuracy and requested any outstanding credits, streamlining the process.
Results
The custom processes established by RadiusPoint through ExpenseLogic enabled numerous end users to not just initiate orders but also track home stages, offering clearer insights into utility expenses for each home build. This innovative approach empowered the home builder to reassign staff and, within the initial six months, achieve nearly $1M in savings.
Streamlining UEM Operations with Expense Management Software
Streamlining Operations: The Role of Expense Management Software in Utility Expense Management
In today’s dynamic business environment, where every penny counts, efficient expense management is paramount. One often underestimated aspect of this financial jigsaw is Utility Expense Management (UEM). Fortunately, the advent of technology has given rise to powerful tools, with expense management software leading the charge. In this article, we explore the benefits of leveraging expense management software for UEM, shedding light on how these digital solutions can revolutionize the way businesses handle their utility expenses.
The Complexity of Utility Expense Management
Utility expenses pose a unique challenge for businesses. The dynamic nature of utility costs, fluctuating rates, and the need for meticulous tracking make UEM a complex task. Manually managing utility expenses not only consumes valuable time but is also prone to errors, making it imperative for businesses to seek more streamlined solutions.
Expense management software has evolved to become an indispensable tool for organizations looking to optimize their financial processes. When it comes to UEM, these digital solutions offer a range of features that simplify the entire utility expense management lifecycle.
Benefits of Expense Management Software in UEM
- Automated Data Capture: Expense management software automates the collection and recording of utility expense data. This reduces the likelihood of human error, ensuring that businesses have accurate and up-to-date information at their fingertips.
- Real-Time Monitoring and Reporting: With expense management software, businesses can monitor utility expenses in real-time. This capability provides a clear overview of usage patterns, allowing for quick identification of anomalies and the prompt implementation of cost-saving measures.
- Integration with Utility Providers: Many expense management software solutions offer integrations with utility providers. This facilitates seamless data exchange, enabling businesses to access billing information, track consumption, and reconcile invoices directly within the software.
- Policy Enforcement: Expense management software allows businesses to enforce spending policies related to utility expenses. This ensures that employees adhere to guidelines, preventing unnecessary expenses and promoting responsible resource usage.
- Customized Reporting and Analytics: Businesses can generate customized reports and analytics related to their utility expenses. This empowers decision-makers with valuable insights, helping them identify areas for improvement and make informed choices to optimize costs.
- Streamlined Approval Workflows: Automating approval workflows is a key feature of expense management software. This streamlines the process of approving utility-related expenses, reducing delays and ensuring that payments are made on time.
- Mobile Accessibility: Many expense management solutions offer mobile applications, allowing users to manage utility expenses on the go. This accessibility is especially beneficial for businesses with remote or traveling employees.
- Scalability: As businesses grow, so do their utility expenses. Expense management software is scalable, accommodating the evolving needs of organizations regardless of their size.
Conclusion
In the realm of Utility Expense Management, embracing technology is not just a choice; it’s a strategic imperative. Expense management software has emerged as a game-changer, offering a comprehensive solution to the challenges posed by utility expenses. By automating processes, providing real-time insights, and promoting responsible spending, these digital tools empower businesses to take control of their utility expenses, fostering financial health and operational efficiency in the ever-evolving landscape of modern business. As organizations strive for excellence in expense management, integrating software solutions into their UEM strategy is a step towards a more agile, informed, and cost-effective future.
The Perfect Storm
The Perfect Storm for Business Operation Disruptions
Accounts Payable reps in multi-location corporations, such as retail chains and QSRs, encounter numerous disruptive challenges. Despite their diligent efforts, they are often held responsible for these issues. As a CFO, Comptroller, or Accounting Director in a large multi-location business, mitigating disruptive events, especially during challenging economic periods, is a significant concern.
Power Disruption: Impact on Hospice Operations
One of our hospice industry clients recently faced a significant challenge when their office lost power one January morning. Janice, the office manager, discovered the issue when she couldn’t switch the lights on and noticed the cold temperature inside. The power outage meant they couldn’t receive or treat patients. Realizing the neighboring businesses had power, she called the utility company and found out their power was disconnected due to non-payment. Calling corporate, Janice sought answers from Accounts Payable regarding the oversight of the unpaid electricity bill that led to a complete disruption of their daily operations.
In the last two years, this recurring scenario has unfolded in businesses of all sizes throughout the US. Accounts Payable staff are frequently held accountable, despite various factors contributing to disruptions that are unrelated to their department. These circumstances have escalated, becoming increasingly systemic and consistently disruptive to regular business operations.
What are these systemic factors?
Factor #1 – Utility Vendor Invoice Delivery Practices
Utility companies often rely on traditional mail for invoice delivery instead of providing convenient online options, which may sometimes be inadequate for businesses. These invoices are complex, containing service details, meter readings, due dates, and various taxes, ranging from one to multiple pages. While some allow downloads, the process has drawbacks. Businesses must manually remember to retrieve invoices monthly, as there’s often no email notification. Additionally, setting up an account for electronic billing relies on specific personnel, risking missed invoices if they leave or are unavailable, potentially leading to service interruptions due to non-payment.
Factor #2 – Utility Vendor Due Dates
Utility companies often provide payment due dates set between 10 to 20 days from the invoice mailing date. Smaller municipalities usually lack online invoice options, leading to the shortest payment windows. Considering a 5-7 day mail delivery, and additional processing time for payment checks, meeting these deadlines becomes challenging. Even with a 20-day due date, internal payment approval processes can impede timely payments.
Factor #3 – Utility Disconnect Notices
Some utilities issue a Disconnect Notice that warns the business that they will be disconnected on a certain date if payment isn’t received. In theory, this is a good fallback to ensure that services are not disconnected. But when you consider that this Disconnect Notice is mailed out and takes 5-7 days to arrive in the mail, there is a risk that service is disconnected before the notice even arrives.
Factor #4 –Postal Service Delays
The US Post Office, a regular contributor to mail delays, has exhibited this issue for years, even as stamp costs rise. In 2021, they further extended delivery times by 2-5 days, leaving Accounts Payable with very little margin for late payment errors.
Factor #5 – Work-from-Home Policies
Pandemic-related lockdowns have compounded delays in utility invoice payments, leading to prolonged phone wait times for Accounts Payable due to remote work. Representatives often cannot email invoices, opting to reprint and mail, causing a 5-7 day delay, compounded by potential mail delivery lateness. The shift to remote work has significantly disrupted utility and telecom companies’ billing and accounting functions, burdening Accounts Payable, especially in larger companies with multiple locations. For instance, a single location can demand about 4.5 hours monthly for Accounts Payable, escalating to over 100 hours for corporations with 25 locations, posing a significant workload solely to prevent service interruptions, a challenge faced by many departments since 2020.
Future Outlook and Conclusion
We foresee no improvement in that situation moving forward. During a recession, customer-facing and administrative personnel are typically the first to face layoffs. Banks are reducing branches to cut staff costs, while tech companies like Amazon are downsizing significantly, affecting customer service representatives (CSRs). The trend of poor CSR support in the last two years appears unlikely to change in 2023.
RadiusPoint, like other leading utility and telecom expense management service providers, exists to deliver efficient solutions that ensure a measurable positive ROI for clients. Clients outsource invoice processing to us, tasking us with a cost-cutting mission. We handle all tasks, from invoice receipt and auditing to disputing charges, obtaining credits and refunds, and ensuring timely payments to avoid fees and service disruptions. Our role is to cut costs and alleviate the burden on Accounts Payable departments. If interested, reach out to us to discuss how we can assist you in optimizing your expenses. Unlock the power of effective expense management today!
The Role of MMS in Remote Work Enablement
In the wake of a rapidly changing work landscape, remote work has become the new norm. Businesses across the globe are adapting to a more flexible approach to work, with the help of technology.
Managed Mobility Services (MMS) play a pivotal role in this shift, enabling organizations to seamlessly transition to remote work while maintaining efficiency, security, and collaboration.
In this article, we’ll delve into the essential role of MMS in remote work enablement.
Empowering the Remote Workforce with Mobile Devices
One of the fundamental aspects of remote work is providing employees with the necessary tools to work from anywhere.
Managed Mobility Services ensure that remote employees have access to mobile devices, such as smartphones and tablets, equipped with the essential applications and data to carry out their tasks efficiently.
This empowers the remote workforce, allowing them to work from the comfort of their homes or while on the go, without any hindrance.
Seamless Communication and Collaboration
Communication is the lifeblood of remote work, and MMS plays a significant role in ensuring seamless connectivity. MMS providers offer solutions that facilitate video conferencing, messaging, and file sharing, allowing remote teams to collaborate effectively.
Whether it’s a virtual team meeting or sharing critical project documents, MMS fosters the flow of information and ideas, regardless of location.
Mobile Device Management (MDM) for Security
Security is a top concern in remote work environments. With employees using their own devices and working from potentially unsecured networks, data breaches are a constant threat.
Managed Mobility Services offer robust Mobile Device Management (MDM) solutions that allow businesses to enforce security policies, remotely wipe data from lost devices, and encrypt sensitive information.
This ensures that company data remains safe, even in the hands of remote workers.
Data Accessibility and Productivity
For remote workers, accessing company data and applications is paramount to maintaining productivity. MMS ensures that remote employees have secure and uninterrupted access to the information they need.
This means that important documents, customer records, and other data can be retrieved and modified from remote locations, enhancing productivity while reducing delays associated with in-office work.
Scalability and Flexibility
Remote work may necessitate changes in the number of mobile devices and data plans a business requires. MMS offers scalability and flexibility, allowing organizations to adjust their services as needed.
Whether you need to onboard new remote employees or downsize your operations, MMS can easily adapt to your changing business requirements.
Compliance and Regulation
Many industries have specific regulatory requirements for data handling, even in remote work scenarios. MMS can help organizations ensure that they remain compliant with industry-specific regulations.
This is particularly important for businesses in healthcare, finance, or legal sectors where data privacy and security are highly regulated.
Cost-Efficiency
Remote work can significantly reduce overhead costs associated with maintaining a physical office space.
MMS further contributes to cost savings by optimizing data plans, reducing unnecessary expenses, and providing predictable monthly budgets, allowing businesses to allocate their resources more efficiently.
Conclusion
In a world where remote work is no longer a luxury but a necessity, Managed Mobility Services are the linchpin that enables organizations to thrive.
By empowering remote workers with mobile devices, ensuring data security and compliance, and providing seamless communication and collaboration, MMS ensures that businesses can maintain their productivity and efficiency, regardless of their employees’ locations.
The role of MMS in remote work enablement is not just about adapting to change; it’s about embracing a new era of work where flexibility, connectivity, and security go hand in hand.
As businesses continue to evolve and adapt to the demands of the modern work environment, Managed Mobility Services will remain an essential tool for success in the remote work era.
Deep Dive Eliminates Telephone Overcharges
Most organizations with multiple locations will have many telephone vendors that they must deal with daily. Each Telecom vendor will have different service offerings that will create confusion and ambiguous monthly invoices.
How do you keep your organization from overpaying for your services or having the wrong ones in place at each location?
Organizations require telecom services at each location for several reasons:
- Regulatory – fire alarm and elevator lines
- Security – alarm lines for the security system
- Order Management – Point of Sale (POS) over data circuits
- Customer Access – Direct Lines to departments for customers
- Connectivity for location to corporate – Data circuits
- Long distance – Connecting the location to the outside world for long-distance calls
- Wireless Service – Wireless devices for employees
These services will be provided by multiple vendors, which means that there will be multiple invoices for each location, each month. Identifying the best vendor with the best rates is not the beginning of the quest to eliminate overcharges. The beginning is the deep dive that is required to identify what services are already in place and how those services are used.
Most organizations have specific telephone needs that require circuits and copper lines for each location. Keeping up with the circuit numbers, each copper line phone number, and what it is used for is a cumbersome task.
For one retailer, not ensuring that services and equipment were properly cataloged and monitored created an embarrassing situation for the telecom and IT team and overcharges of over $62k paid needlessly by the retailer.
Retailers must have telephone numbers that allow a patron to call a specific department such as men’s shoes or children’s clothing. To have this type of service a retailer needs to have direct lines to each department.
Keeping an inventory of the circuits and phone numbers may have identified that the services were not canceled when the location closed. The other issue that created this overcharge situation was the ambiguous invoice from the telephone vendor.
The billing did not break down the services with enough detail to allow the telecom and IT team to realize that when they requested the services to be disconnected, not all services were disconnected. This oversight caused a 2 year overpayment period of $62k.
So, beyond the obvious of making sure your company is not overpaying for services, why is this deep dive needed?
In the Telecom industry, this deep dive is referred to as an inventory and audit of the telecom and IT services. This inventory and audit should create a baseline of service types, costs, contracts, and invoices.
It should also validate what services you have, the location address, and the department or personnel using the services. Identifying errors, overcharges and inefficiencies in your environment will bring the entire process together to cut costs and increase efficiency.
Having this information detailed by location would have saved this retailer over $60k because when the services were no longer needed and a disconnect request was made, it would have been quickly identified that the services continued to bill.
Identifying the right partner to work with to perform the inventory and audit is a must. There are many organizations that will “audit” your telephone invoices, some only charging for a portion of the savings however, defining exactly what will be audited and what the deliverables should be the first questions asked of your potential partner.
If you need this deep dive to identify very detailed information about your current telecom environment, you will most likely not receive that with a contingency-based model as often these are quick looks at the services to identify the low-hanging fruit.
The deep dive needed to specifically identify all services and their purpose will need to be performed by a project-based company that defines the deliverables with multiple steps and a very detailed work product.
Identifying the information that will be included in the inventory and audit is one of the first steps in gathering the information required and a timeline that will produce cost-saving results. One of the most frequent inventory and audits performed is for copper lines or Plain Old Telephone System (POTS) lines.
These lines are often required for businesses for alarm or elevator lines. Several years ago, this was the best and most cost-effective solution, however, innovation has created new types of services that work better and are much more cost-effective.
A business can transition over to these new services. However, if you do not have an inventory of all of your current services and phone lines, you run the risk of not disconnecting all of the POTS lines and you will keep paying for them.
A recent inventory and audit identified over 600 POTS phone lines that should have been canceled years before, however, the locations continued to pay for the lines because they had no idea the lines still existed.
The services had moved to a more modern service at a much lower cost, but the telecom team performing the work did not realize that the lines continued to bill. This oversight cost this company over $30k per month.
How can your chosen partner prevent this type of oversight from occurring? Identifying all the current services is the best place to start by ensuring that you’re only paying for what you need.
A successful project consists of a framework for managing fixed telecom environments that focuses on people, processes, and tools/technology. The inventory and audit establish a contract, invoice, service detail, and cost baseline.
The visibility gained through the project supports technology selection, budgeting, contract negotiations, vendor relationships, change management, and other integral telecom activities.
What type of information is needed to complete an inventory and audit?
- Location address
- Service contracts
- Invoices
- Customer Service Records
- Organizational information
- Service ordering process
Identifying the services and lines or circuits is one of the most important areas of the project as this is where most of the hidden services are found. Ensuring that an organization is only paying for the services that they want, and need is an integral part of the process and can uncover thousands in savings.
During an inventory and audit for an auto parts after-market organization, it was uncovered that there were 25 toll-free lines billing long-distance calls however the lines did not belong to them.
The lines were billed through the long-distance carrier and were on an invoice that was billed monthly; however, the total invoice cost was over $500k monthly and was more than 1,000 pages in length.
The only way this type of overcharge is identified is by calling each phone line to ask who the line belongs to. Once this occurred, the lines were moved from the organization’s account, saving them $10k per month.
Verifying ownership of the services is the first part of the process and once the services are verified as belonging to your organization, it is necessary to ensure that the monthly charges are accurate.
Identifying where contracts exist for each location is time-consuming but a required part of performing the inventory and audit steps. A quick-service restaurant learned the hard way that obtaining a global contract does not mean that you can set it up and forget about it.
For their 280 locations, the Internet Service Provider (ISP) set up services under contract, however, they set up an incorrect rate plan that caused this client to bill at a higher rate for each location’s Internet service.
The higher rate cost them $16,000.00 for the year, something that they had not budgeted for, and the overage caused financial reporting issues for their locations.
With the various types of services telephone or landlines, wireless, internet, long distance, etc. the steps to complete the inventory and audit are different for each type of service.
Ensuring that your partner is fully versed on each type of service and understanding what steps will be taken to audit each type of service will eliminate issues during the deliverable phase.
Upon completion of the project, you should have a set of these discoveries. It will also give you the baseline of information you need to effectively manage your environment on an ongoing basis, optimizing cost-effectiveness and efficiency.
Completion of this project will provide key insights, revealing what services are installed, where services are installed, what services are invoiced, and how much services cost.
This project will provide you with the comfort of a complete inventory of your telecom environment and will give you the baseline of information needed to manage your telecom environment in the most efficient and cost-effective manner.
With the skyrocketing costs for telecom services and the need for fiscal responsibility in the face of inflation and possible recession, it is imperative that a business consistently monitors their telecom and IT invoices and services.
Unlock Cost Savings Through Telecom Expense Management
Unlocking Cost Savings: How Telecom Expense Management Can Benefit Your Business
In today’s fast-paced business landscape, optimizing costs is a top priority for organizations across industries. One area where significant cost savings can be unlocked is telecom expenses. However, managing telecom expenses efficiently can be a complex and time-consuming task for businesses of all sizes. This is where Telecom Expense Management (TEM) comes into play.
With TEM, businesses can streamline their telecom expenses, reduce unnecessary costs, and regain control over their telecom budget. By leveraging advanced software solutions, TEM provides businesses with real-time visibility into their telecom spend, helping them identify areas of inefficiency and take corrective actions.
By implementing a robust TEM strategy, businesses can benefit in multiple ways. From negotiating better contracts with telecom service providers to identifying and eliminating billing errors and unauthorized charges, TEM helps organizations optimize their telecom costs while ensuring compliance and improving overall efficiency.
In this article, we will delve into the key benefits of telecom expense management and explore how businesses can leverage it to unlock significant cost savings. So, buckle up and get ready to discover the power of effective telecom expense management.
The importance of managing telecom expenses
Telecom expenses are a significant part of an organization’s budget. With the rise of remote work and the need for constant connectivity, businesses are spending more on their telecom expenses than ever before. However, managing these expenses efficiently can be a daunting task, given the complexity of telecom billing and the number of service providers involved.
That’s where telecom expense management comes in. By implementing a TEM strategy, businesses can gain better visibility into their telecom expenses, identify areas of inefficiency, and take corrective actions to optimize their costs. TEM helps businesses streamline their telecom expenses, reduce unnecessary costs, and regain control over their telecom budget.
In today’s competitive business landscape, managing telecom expenses is more critical than ever before. Organizations that fail to optimize their telecom spending risk losing out on cost savings and falling behind their competitors.
Telecom expense management statistics
Telecom expense management is becoming increasingly popular among businesses of all sizes. According to a report by MarketsandMarkets, the global telecom expense management market is expected to grow from $2.78 billion in 2020 to $5.99 billion by 2025, at a Compound Annual Growth Rate (CAGR) of 16.6% during the forecast period.
Another report by Gartner suggests that TEM can help organizations reduce their telecom expenses by up to 40%.
Furthermore, a survey conducted by Aberdeen Group found that businesses that implement a TEM strategy can reduce their telecom spend by an average of 15% to 20%.
These statistics highlight the significant cost savings that can be unlocked by implementing a robust TEM strategy.
Understanding the components of telecom expenses
Telecom expenses consist of various components, including voice, data, and mobile services. These services are provided by multiple service providers, making telecom billing complex and challenging to manage. Understanding the components of telecom expenses is crucial for businesses looking to optimize their telecom costs.
Voice services are typically provided by traditional landline providers or Voice over Internet Protocol (VoIP) providers. Data services include internet connectivity and networking solutions, while mobile services include voice and data plans for mobile devices. Other components of telecom expenses include hardware, software, maintenance, and support services.
Without proper management, these components can quickly add up, resulting in unnecessary costs and inefficiencies. By implementing a TEM strategy, businesses can gain better visibility into their telecom expenses and identify areas of inefficiency to optimize their costs.
Benefits of implementing telecom expense management
Implementing a robust TEM strategy can benefit businesses in multiple ways. Here are some of the key advantages of telecom expense management:
- Cost Savings – One of the primary benefits of TEM is cost savings. By gaining better visibility into their telecom expenses, businesses can identify areas of inefficiency and take corrective actions to optimize their costs. TEM helps businesses negotiate better contracts with service providers, identify and eliminate billing errors and unauthorized charges, and optimize their telecom spending to maximize cost savings.
- Improved Operational Efficiency – TEM helps businesses streamline their telecom expenses, reducing the time and effort required to manage them. With real-time visibility into their telecom spend, businesses can identify areas of inefficiency and take corrective actions to improve their overall efficiency.
- Increased Visibility and Control – TEM provides businesses with real-time visibility into their telecom spend, enabling them to monitor their expenses and identify areas of inefficiency. This improved visibility and control help businesses regain control over their telecom budget and make informed decisions regarding their telecom expenses.
- Compliance – TEM helps businesses ensure compliance with regulatory requirements and internal policies. By monitoring their telecom expenses, businesses can identify and eliminate unauthorized charges and ensure that their telecom spend is in line with regulatory requirements and internal policies.
- Scalability – TEM solutions can be scaled to meet the needs of businesses of all sizes. Whether a business has a few dozen or several thousand telecom devices, TEM can be tailored to meet their specific needs, providing them with the scalability they need to manage their telecom expenses effectively.
Steps to implement telecom expense management
Implementing a TEM strategy requires careful planning and execution. Here are some of the key steps involved in implementing a telecom expense management strategy:
- Conduct a Telecom Audit – The first step in implementing a TEM strategy is to conduct a telecom audit. This audit helps businesses gain better visibility into their telecom spend, identify areas of inefficiency, and develop a plan to optimize their costs.
- Develop a TEM Strategy – Based on the audit results, businesses can develop a TEM strategy that outlines their goals, objectives, and action plans. This strategy should include a plan to optimize their telecom spend, negotiate better contracts with service providers, and eliminate billing errors and unauthorized charges.
- Choose a TEM Solution – Choosing the right TEM solution is crucial for the success of a TEM strategy. Businesses should consider factors such as scalability, customization, and integration capabilities when choosing a TEM solution.
- Implement the TEM Solution – Once a TEM solution has been chosen, it’s time to implement it. This involves integrating the TEM solution with existing systems, training employees on its use, and developing processes to ensure its effective implementation.
- Monitor and Optimize – Finally, businesses should monitor their telecom expenses regularly and optimize their TEM strategy as needed. This involves identifying areas of inefficiency, taking corrective actions, and continuously monitoring their telecom spend to ensure compliance and cost savings.
Best practices for telecom expense management
Implementing a TEM strategy requires careful planning and execution. Here are some best practices to consider when implementing a telecom expense management strategy:
- Conduct Regular Audits – Regular audits help businesses gain better visibility into their telecom spend and identify areas of inefficiency. Conducting audits regularly can help businesses optimize their telecom costs and maximize cost savings.
- Implement Automated Systems – Automated systems can help businesses streamline their telecom expenses, reducing the time and effort required to manage them. By automating tasks such as invoice processing and payment, businesses can improve their overall efficiency and reduce the risk of errors.
- Establish Clear Policies and Procedures – Establishing clear policies and procedures for managing telecom expenses is crucial for ensuring compliance and cost savings. These policies should outline how telecom expenses are managed, who is responsible for managing them, and how disputes are resolved.
- Train Employees – Training employees on the use of TEM solutions and the company’s policies and procedures for managing telecom expenses is crucial for the success of a TEM strategy. Employees should be educated on the importance of managing telecom expenses and the role they play in optimizing costs.
- Continuously Monitor and Optimize – TEM is an ongoing process that requires continuous monitoring and optimization. Businesses should regularly review their telecom expenses, identify areas of inefficiency, and take corrective actions to optimize their costs and ensure compliance.
Common challenges in telecom expense management and how to overcome them
Implementing a TEM strategy can be challenging, given the complexity of telecom billing and the number of service providers involved. Here are some common challenges in telecom expense management and how to overcome them:
- Complexity of Telecom Billing – Telecom billing is complex, involving multiple service providers and various components. This complexity can make it challenging to gain visibility into telecom expenses and optimize costs. To overcome this challenge, businesses should consider implementing a TEM solution that provides real-time visibility into their telecom spend.
- Disparate Systems and Processes – Managing telecom expenses can involve multiple systems and processes, making it challenging to streamline and optimize costs. To overcome this challenge, businesses should consider integrating their systems and processes and implementing an automated TEM solution.
- Lack of Resources – Managing telecom expenses can be time-consuming and require specialized knowledge and expertise. To overcome this challenge, businesses should consider outsourcing their TEM needs to a third-party provider that specializes in telecom expense management.
- Lack of Visibility – Without proper visibility into their telecom expenses, businesses cannot identify areas of inefficiency and take corrective actions. To overcome this challenge, businesses should consider implementing a TEM solution that provides real-time visibility into their telecom spend.
- Difficulty in Negotiating Contracts – Negotiating contracts with service providers can be challenging, given the complexity of telecom billing and the number of service providers involved. To overcome this challenge, businesses should consider leveraging the expertise of a TEM provider to negotiate better contracts and optimize their telecom spend.
Choosing the right TEM solution for your business
Choosing the right TEM solution is crucial for the success of a TEM strategy. Here are some factors to consider when choosing a TEM solution:
- Scalability – The TEM solution should be scalable and able to meet the needs of businesses of all sizes.
- Customization – The TEM solution should be customizable, allowing businesses to tailor it to their specific needs.
- Integration Capabilities – The TEM solution should be able to integrate with existing systems, such as Enterprise Resource Planning (ERP) systems and Customer Relationship Management (CRM) systems.
- Reporting Capabilities – The TEM solution should provide robust reporting capabilities, allowing businesses to gain real-time visibility into their telecom spend and identify areas of inefficiency.
- Support and Training – The TEM solution provider should offer comprehensive support and training to ensure the effective implementation and use of the solution.
Conclusion: Maximizing cost savings with telecom expense management
In today’s fast-paced business landscape, optimizing costs is a top priority for organizations across industries. Telecom expenses are a significant part of an organization’s budget, and managing them efficiently can be a complex and time-consuming task. However, by implementing a robust telecom expense management strategy, businesses can unlock significant cost savings, improve operational efficiency, and ensure compliance.
From negotiating better contracts with service providers to identifying and eliminating billing errors and unauthorized charges, TEM helps businesses optimize their telecom spend and regain control over their telecom budget. By following best practices and choosing the right TEM solution, businesses can maximize cost savings and gain a competitive edge in today’s business landscape. So, what are you waiting for? Unlock the power of effective telecom expense management and start optimizing your telecom costs today!
RadiusPoint in Gartner’s 2023 Market Guide for TEM Services
Orlando, FL September 25, 2023 – The 2023 Gartner Market Guide for Telecom Expense Management Services recognizes RadiusPoint as a Representative Vendor, affirming its position as a premier single-source SaaS platform and BPO service provider in the TEM services sector, a testament to its over three decades of market presence.Read More
ESG Reporting: Eliminating 800 Man-Hours of Data Gathering
Many organizations have a workable Corporate Social Responsibility (CSR) plan in place. However, Environmental Social Governance (ESG) will be the new benchmark going forward to ensure that both your organization and brand stay relevant and socially acceptable. How does your organization get ready and stay ready for this very intricate and detailed reporting that is required for electric, gas, and water consumption?
Challenge
A nationwide retailer with over 1,600 locations has required reporting for the electric, gas and water consumption for each one of their locations. The information required must be gathered from the monthly invoices. The time to gather this information manually would have taken over 800 hours which would have involved someone reviewing each invoice for each month and contacting the vendor for the necessary information that was missing from the invoice.
Issues to Resolve
- Time constraints – the reporting is needed during the 1st quarter of the year for the previous year
- Personnel constraints – The Accounts Payable team did not have time which required temporary staff to be hired
- Knowledge Gap – the vendor’s invoices vary from vendor to vendor so being able to read an electric, gas, or water invoice was necessary to get the work completed timely
- Invoice Availability – the invoices for a portion of the required review had been moved off-site and had to be recalled for this review.
Opportunity
Identifying the requirements early in the relationship with RadiusPoint and this client created the perfect opportunity for this client to have the required reporting in advance of the need. RadiusPoint provides the monthly utility expense management services for each of the 1,600 locations from receipt of the invoice to the bill pay portion of the process. This utility expense management also involves energy expense management that identifies the usage in kWh, therms, and gallons to create more detailed reporting. Using the information that was already being gathered from the invoices and adding the additional required information, RadiusPoint was able to ensure that this client had the required reporting by location for each type of service.
Solutions
The data usage that is needed from each invoice is compiled by the chosen ESG company that creates the client’s overall ESG report. Having this accurate data when it is needed was paramount to the client. The data is required during the first quarter of the next year for the previous year which puts a large burden on an already busy Accounts Payable department. RadiusPoint was able to pull together the reporting and provided an ongoing report solution so that the following year, the report would be completed by the last week of January for the entire previous year. This solution allows the RadiusPoint team to review the data and add any missing components on a monthly basis to ensure that all data is reported for the year by the beginning of the following year. This solution alone eliminated the normal delays of trying to identify who would be pulling together this information and when it would be provided.
Once the client looked at hiring temporary staff to pull the additional required data from the invoice, it was determined that this project would involve over 800 man-hours for the 1,600 locations. RadiusPoint’s solution provided most of the required usage data and the RadiusPoint team was able to go through and identify the missing information quickly to populate as required.
Utility invoices are not easily deciphered and having staff to read the invoices and gather the necessary data was a stumbling block for this client. Trying to find the staff that could perform this data gathering task that was knowledgeable about the electric, gas and water services was problematic. RadiusPoint’s team has an ESG department with knowledgeable personnel that easily filled this knowledge and personnel gap for the client.
Having the invoices on hand presented a problem for this client but it was one that was easily resolved by RadiusPoint. All invoices processed by RadiusPoint are electronically attached to the account number and the digital image is saved for up to seven (7) years. Reviewing past invoices was made easy with the information readily available at the click of a mouse.
The Results
Most ESG programs make provisions for reducing the cost of those services, but the “how” to achieve these cost reductions can be hard to predict. Measuring consumption is the first step in the right direction to reducing usage and monthly costs. The monthly ESG management services allow for the client to see the usage information on a monthly basis which in turn allows for necessary pivots that could result in a reduction of usage.
RadiusPoint’s monthly invoice processing and expense management services manage the utility invoice from receipt to payment of the invoice. Utility and telecom auditing are also important parts of the monthly service that allows RadiusPoint to fully manage the entire lifecycle of the utility or telecom invoice and service. This client saved over $48k and received their detailed and required ESG reporting on time.
Telecom Expense Management (TEM) – Auditing Telecom Invoices for Saving Opportunities
The telecom expense management (TEM) industry has grown in size over the last few years, concurrent with the evolution of telecom technology, the demand for bandwidth, and the rising use of wireless devices and video conference services during the pandemic.
As a result of these trends, medium-sized and large corporations have resorted to using the services of third-party providers specializing in the analysis of telecom vendor services and billing to curb the increasing weight of telecommunication services on their P&L.
As part of their mission, telecom expense management specialists like RadiusPoint audit the invoices issued by telecom and internet service providers, to detect cost-saving opportunities and erroneous charges driving up the cost of the lines.
TEM Auditing Terms Definitions
To do their invoice analysis, telecom expense management specialists must gather specific data points from the client and the telecom operators billing the client. Here are 11 data points that the TEM specialist always must collect. The TEM specialist provides the client with the 12th one in the following table.
Some definitions are necessary:
| DATA POINT | WHAT IT IS |
| Service Address / Identifier | The physical location or unique identification of the client’s telecom service |
| Service Provider | The company that provides telecom services to the client |
| Master Account Number | The main account number associated with the client’s services from the service provider |
| Sub-Account Number | Secondary account numbers tied to the master account often used to track usage and costs for specific departments or locations |
| Circuit ID/Number | A unique identifier for each circuit or line that connects the client’s service location to the service provider’s network |
| Circuit Type | The technology used for the circuit, such as T1, E1, DSL, MPLS, or Ethernet |
| Port Size | The bandwidth capacity of the port (measured in Mbps or Gbps) used to connect the client’s equipment to the service provider’s network |
| PVC (Permanent Virtual Circuit) | A virtual connection between two points on a network that simulates a dedicated physical connection |
| DLCI (Data Link Connection Identifier) | A unique number assigned to a PVC in a Frame Relay network, used to identify the virtual connection |
| CIR (Committed Information Rate) | The guaranteed minimum data transfer rate provided by the service provider for a particular circuit |
| Un-Audited MRC (Monthly Recurring Charge) | The monthly cost for the telecom service as billed by the service provider, before the audit |
| Audited MRC | The corrected or optimized monthly cost for the telecom service, identified during the audit process |
Data points: how they are used for Telecom audit
Each of the data points above has a role in the auditing process which will eventually lead to identifying potential savings or billing discrepancies. The table below summarizes the use of these data points.
| Data Point | Auditing Purpose & Identifying Savings/Discrepancies | Reference/Source Document | Flagging Cost-Saving Opportunities or Billing Discrepancies |
| Service Address / Identifier | Verify service locations and validate service usage | Service provider invoices, contracts, and client’s internal records | Compare the service address with the client’s records to identify unused services or locations |
| Service Provider | Ensure appropriate providers and services are being used | Service provider invoices and contract | Look for better rates or service options from alternative providers or negotiate with the current provider |
| Master Account Number | Verify account accuracy and organization | Service provider invoices and contract | Ensure charges are billed to the correct account and identify unauthorized charges |
| Sub-Account Number | Analyze costs and usage by department or location | Service provider invoices and client’s internal records | Identify high-usage areas, reallocate resources, or uncover billing errors |
| Circuit ID/Number | Validate the circuits and their usage | Service provider invoices, contracts, and circuit inventory | Compare circuit IDs with inventory to identify unused circuits or billing discrepancies |
| Circuit Type | Assess if the correct technology is being used | Service provider invoices, contracts, and client’s internal records | Evaluate if a more cost-effective or efficient circuit type is available |
| Port Size | Check if the bandwidth capacity meets the client’s needs | Service provider invoices, contracts, and client’s internal records | Identify underused ports or opportunities to upgrade/downgrade for cost savings |
| PVC | Validate virtual connections between network points | Service provider invoices, contracts, and client’s internal records | Ensure PVCs are correctly billed and identify unused or unnecessary virtual connections |
| DLCI | Confirm Frame Relay network connections | Service provider invoices, contracts, and client’s internal records | Verify DLCIs match the client’s records and identify billing discrepancies |
| CIR | Ensure the guaranteed data transfer rate is being met | Service provider invoices, contracts, and client’s internal records | Monitor actual usage vs. CIR to identify opportunities for negotiation or cost savings |
| Un-Audited MRC | Establish a baseline for monthly telecom expenses | Service provider invoices | Compare with audited MRC to determine cost-saving opportunities |
| Audited MRC | Identify optimized monthly telecom expenses after the audit | Service provider invoices and audit findings | Validate the effectiveness of the audit and track potential savings |
TEM Cost-saving opportunities
Once the information has been collected, and the telecom operators‘ billing has been analyzed, the TEM specialist looks for specific types of cost-savings their client can make on their telecom bills.
Here are 10 types of cost-savings a TEM specialist would look for:
- Unused services: Discontinue services or circuits that are no longer in use, which helps reduce monthly costs.
- Negotiated rates: Renegotiate contracts with the service provider to obtain better service rates or discounts.
- Service bundling: Combine multiple services or features into a bundled package for discounted rates.
- Optimized service plans: Choose service plans that better match usage patterns, such as unlimited plans for high usage, or pay-as-you-go plans for variable usage.
- Technology upgrades: Replace outdated or inefficient circuits with newer, more cost-effective technologies.
- Volume discounts: Leverage the client’s purchasing power to negotiate volume discounts based on the number of lines or the total spending.
- Optimization of port sizes: Adjust port sizes to match the client’s bandwidth requirements more accurately, avoiding over- or under-provisioning.
- Resource reallocation: Identify high-usage areas and redistribute resources or services to better align with the organization’s needs.
- Tax and regulatory fee adjustments: Verify and correct taxes and regulatory fees, which can result in cost savings if errors are found.
- Alternative providers: Research and consider alternative service providers offering better rates or service options.
Typical telecom overcharging situations and billing errors
TEM specialists use proprietary SaaS platforms to automate the analysis and processing of telecom bills. These complex systems compare the client’s current telecom invoices with the vendor’s conditions, the line number, and the device ID when applicable.
The function of these SaaS platforms is to accelerate and systematize the processing of telecom invoices, a big organization with hundreds of retail locations that can quickly become a monthly nightmare for their Accounts Payable department. In fact, it is not uncommon for a large organization to have to process over a thousand telecom invoices in the course of a month. This represents a very large workload, and when reduced by automation, sizable soft-dollar savings for the organization.
The TEM specialist sets up the SaaS platform to flag out any inconsistency in telecom billing, and mismatch with known rates. Here is an example of 10 common overcharges and billing errors found in a telecom operator’s invoice:
- Double billing: Charges for the same service or feature appear multiple times on the invoice.
- Incorrect rates: Charges that do not match the contracted rates or discounts agreed upon with the service provider.
- Unauthorized charges: Charges for services or features not requested or approved by the client.
- Misapplied taxes: Incorrect application of taxes or regulatory fees, resulting in overcharges.
- Billing for disconnected services: Charges for previously disconnected or terminated services.
- Incorrect usage charges: Overstated charges due to metering errors or inaccurate data.
- Billing for non-existent locations: Charges for services at places where the client lacks telecom services.
- Incorrect service plan charges: Charges for a more expensive service plan than agreed upon or requested.
- Incorrect circuit charges: Charges for circuits not in the client’s inventory or assigned incorrect circuit IDs.
- Late payment fees and penalties: Unwarranted late payment fees or penalties that are not justified based on the client’s payment history or the contract terms.
The TEM specialist’s job is to flag these errors and let the Accounts Payable department deal with the vendors to recover credits and refunds.
But TEM specialists like RadiusPoint offer their clients to take over this part of the service, and recover credits and refunds themselves, as well as follow up with billing corrections so that the same errors don’t reappear in the next billing cycle.
By identifying cost-saving opportunities and billing discrepancies, and requesting refunds and credits from telecom operators, Telecom Expense Management specialists ensure their clients can curb the rising costs of telecommunications services, spend no more than what is necessary for their organization to operate, and offer their clients valuable business intelligence about the utilization of their telecom assets and their allocation by cost centers. This enables an organization to make better-informed decisions in procurement, cost allocation, and technology.
$1.3M in Telecom Refunds and Cost Savings: Case Study
In this new case study, CEO Sharon Watkins discusses the telecom refunds and cost saving opportunities discovered by RadiusPoint during an Inventory & Audit of the telecom invoices of a global paper manufacturer. This case study highlights the need for organizations to streamline their telecom invoice processing to avoid overcharges and paying for services that telecom operators add to their billing.
Transcript of the video
Summary
In this video, we will talk about how we were able to assist a paper manufacturer, a Fortune 100 company with a global presence, with their mobility management and telecom expense management needs.
To start with results, RadiusPoint obtained telecom refunds of over $450,000 on their wireless expenses in the first year of service. These refunds matched identified overcharges on wireless invoices. The primary challenge of our client was that they did not have the personnel to manage over 10,000 wireless devices and end-users. This was a global situation, the end-users were spread around the world.
The second major challenge was they could just not manage their telecom billing: at that time, invoices came in a box of over 3 feet high. According to our client, it took six people each month to go through these invoices, flipping through pages and pages to verify costs. So they needed assistance with the invoicing side, as well as with managing the servicing of so many end-users.
Inventory & Audit
We assisted our client with our proprietary platform, ExpenseLogic™, getting them set up to audit and process those invoices each month. We identified billing errors, and went back to the telecom operators to obtain all necessary refunds and reconcile the credits back on the bill.
We did identify over $400,000 in telecom refunds the first year. Those came back to the invoice. Then, still in the first year of service, we reduced costs by identifying services that were not supposed to be on their bill, or that Corporate did not want to pay for or authorize their end-users to have on their company phone. We identified over $850,000 in ongoing telecom savings (cost avoided).
Discoveries during the process
During our Inventory & Audit process, we discovered several major anomalies. For instance, the organization was still paying for phones (and services) for employees no longer on the payroll. Some of them had given their company phone to their children, and our client was still paying for them phones though these ex-employees had not worked there in two years.
We also identified instances when employees were downloading services (apps) — basically almost every phone had paid-app downloads — that were not authorized by company policy. However, since our client had no way to audit the bills, they had no idea their staff had downloaded those extra apps.
Initial TEM mission
Initially, RadiusPoint was hired by this client to perform a one-time audit, Then we continued on with monthly services for Telecom Expense Management and Mobility Expense Management.
Telecom refunds & savings
Q: Where did the $1.3 million in saving come from?
A: The $1.3 million came from two areas. First, we got over $400,000 in telecom refunds. During the first leg of our mission, as we were performing our Inventory & Audit process, we identified what actually belonged to the client, and disconnected what did not belong to them.
Second, going forward, we made recommendations that resulted in another $800,000 in telecom savings. Our recommendations aimed at cutting costs, consolidating the wireless operators, and optimizing contract rates.
That’s where the $800,000 [and ultimately, the $1.3M] came in.
TEM mission follow-up
Q: Does the client continue saving money on their telecom expenses?
A: Our client does continue to save money on an annual basis through our Telecom Expense Management services and the refunds we identify. It’s no longer a historical audit because the service occurs on a monthly basis and as the telecom invoice comes in, it is audited through our ExpenseLogic software platform. We then go to the vendor and reconcile. So yes, they continue to save money on a monthly basis.
Additional resources and references:
These links provide additional relevant information on our services and client feedback.
RadiusPoint and Telecom Expense Management: Our Presence in the Gartner Market Guide
TEM services: One of the two core business lines of RadiusPoint
Next case study:
Click here to discover how a glass manufacturer saved $100K on telecom expenses using RadiusPoint services
In this new video case study, Sharon shares how RadiusPoint helped a global glass manufacturer with large retail operations in the U.S. to overcome a lack of procurement framework, and curb their telecom expenses by $100K+ in Year 1 to get a ROI of 200% on TEM services.
Glass Manufacturer Saves $100K On Telecom Expenses
In this video case study, Sharon shares how RadiusPoint helped a global glass manufacturer with large retail operations in the U.S. to overcome a lack of procurement framework, and curb their telecom expenses by $100K+ in Year 1 to get a ROI of 200% on TEM services.Read More
TEM Process Automation Saves $100K to QSR Chain in Year 1
RadiusPoint helps organizations manage spends quickly and conveniently. In the case details below, learn how RadiusPoint saved a retail client from overspending valuable telecom dollars. Case Background: Nationwide restaurant chain with 240 restaurant locations and…Read More
How Managed Mobility Services Cut Costs 22% ($400K in Year 1)
A food service company with a wide array of locations, distribution facilities, food plants, farms and ranches had hundreds of wireless devices to manage. Unfortunately, our client had no wireless procurement policy framework, and no structure for adding new users to their plans or for procuring new devices. Hence their decision to hire RadiusPoint to rationalize their inventory of devices and lines. This was an MMS mission, a specialty in which we have a long-running experience.Read More
Telecom Service Outages: How to Avoid Them During an Acquisition
Telecom service outages often occur when an organization divest a part of its business…Read More
Does Your Enterprise Face These 5 TEM Challenges?
When selecting a telecom expense management service partner, it is best practice to consider…Read More
Inventory & Audit
In this video about the telecom Inventory & Audit process, Sharon Watkins, CEO…Read More
Cutting Telecom Expenses in a Down Economy: TEM in Focus
Telecommunication services rank amongst the top 5 operating expenses of almost…Read More
Optimization & Cost Cutting in 2023
Because we are experts in expense management and cost cutting, our clients ask…Read More
$100K+ in Cost Savings with TEM & Support Desk Services
This case study shows how a manufacturer succeeded in generating cost savings of…Read More
Divestiture: Inventorying Telecom Assets Avoids Hidden Charges
As part of its core competences in M&A Support Services, RadiusPoint accompanies…Read More
Vendor Managed Services: Why Tread Carefully
Each year, new vendors enter the telecom managed services market, offering what is called…Read More
Loss Prevention Program Cuts Costs at 10,000 Retail Locations
This case study shows how RadiusPoint managed a retailer’s loss prevention…Read More
Wireless Discovery and Optimization Saves $830K Annually
Managing wireless invoices for tens of thousands of users gets complicated and expensive…Read More
Utilities Expense Optimization Saves as Much as 13%
Clients outsource their utility invoices to RadiusPoint to identify savings opportunities they are unaware of…Read More
Overcoming Inflation-Driven Budget Woes With Cost Cutting
Commodity prices have hit historic highs and continue to climb. Businesses are grappling with supply chain disruptions, an energy crisis, and higher wages stemming from labor shortages. Today’s inflationary environment will be with us for some time. This confluence of challenges requires decisive steps to adjust prices, seek new sources of growth, and pursue aggressive cost cutting…Read More
A Due Diligence Process is Essential – M&A Support Services
Already bought and sold twice, a retailer that was on the market again for sale. The third buyer performed…Read More
Driving the Acquisition Transition Phase: Role of M&A Support Services
“Driving the acquisition transition phase” is key to achieving the financial objectives of an M&A…Read More
M&A Support Services: A New Way to Think About Their Role
M&A support services are among the BPO services increasingly used by organizations…Read More
M&A Support Services | Transportation Industry Case Study
This brief case study highlights the role of M&A support services in the transportation industry…Read More
Inventory Management Uncovers Hidden Assets and Services
Inventory management is one of the eight cornerstone functions of ExpenseLogic®…Read More
Vacancy Cost Recovery Decreases Utility Expenses by 12%
Vacancy Cost Recovery is a significant part of the issues faced by property management..Read More
587% ROI on TEM/UEM Services in FY2018
RadiusPoint generated a 587% ROI on TEM/UEM services on average for our clients in FY 2018. ROI is measured and verified…Read More
Cost Cutting & a 400% ROI: TEM/UEM Services in a Growth-by-Acquisitions Scenario
Cost cutting at operations level is more often than not one of the top 3 objectives of…Read More
Managed Mobility Services: Top 3 Differentiators Between Providers
A multitude of managed mobility services (MMS) providers have appeared…Read More
Vendor Billing Audits for a Nationwide Landscaping Company
Technology and utility billing audits remain a primary focus of RadiusPoint’s core expertise as we continue…Read More
Contingency Fee Pricing Model: Beware
If you heard the term “contingency fee pricing model”, did you ever wonder which party…Read More
Utilizing RadiusPoint for Vacant Cost Recovery
A term described to aid property owners in recovering costs associated with tenants…Read More
RadiusPoint in Gartner’s Market Guide for Telecom Expense Management
Orlando, FL June 21st, 2019 [Updated: Nov 2021]– RadiusPoint©, the leading single-source platform, and a major provider of Technology Expense Management services announces its inclusion as aRead More
Facilities Management: 3 Plans to Yield Cost & Energy Savings
Facilities management is the body of knowledge and practices implemented to ensure the functionality…Read More
Cost Reduction Plan Saves 2,000+ Man-Hours
Any cost reduction plan implemented in the context of an acquisition or a divestiture must take into account…Read More
Mergers & Acquisitions: A More Seamless Integration Process
Mergers & acquisitions tend to generate their own margin-depressing cascading effects at Procurement…Read More
Bill Audit + e-Procurement: Cost Savings of 37% on Water Delivery
This case study shows how a bill audit carried out by RadiusPoint, associated with the use of an e-Procurement portal…Read More
Technology Expense Management on a Single Platform: Results
Technology Expense Management service providers like RadiusPoint agree on…Read More
Invoice Audits – Which is More Beneficial: One-off or Monthly?
When evaluating invoice audit frequency requirements in the process…Read More
TEM-UEM Services: 370% ROI for our Clients in 2020
RadiusPoint, a BPO service provider and a leader in the TEM-UEM services industry….Read More
Cost Avoidance & Savings: $40K in UEM Cost Optimization
This case study is about cost avoidance and cost savings in utility expense management…Read More
Shipping Cost Optimization Saves $1.1M Annually
Shipping cost optimization has become a major priority for the logistics, transportation, retail & wholesale…Read More
RadiusPoint Included as a Representative Vendor in Gartner’s 2020 Market Guide for Telecom Expense Management
Orlando, FL October 20th, 2020- RadiusPoint©, the leading single-source platform…Read More
Inventory Management Helps Recovering $174K in Credits
Inventory management is one of the 8 cornerstone functions of our SaaS platform, ExpenseLogic…Read More
Missing Due Diligence Inventory Adds $15K to Acquisition Cost
When making an acquisition, it pays off for the acquiring company to add a due diligence inventory of…Read More
Facilities Benchmarking and Energy Star Programs
Whether you own, manage, or hold properties for investment…Read More
Normalizing Invoice Processing and Payment in Hyper-Growth Phase
This case study focuses on what RadiusPoint did to avoid the straining of the invoice processing and…Read More
Streamlining Invoice Processing for a Healthcare Client
As part of its telecom/utility invoice processing, expense management and process optimization services…Read More
Telecom Expense Management in Healthcare
Implementing best practices in utility and telecom expense management in healthcare organizations…Read More
Utilities Mismanagement Costs $18K in Unnecessary Expenses
Utility management is one of RadiusPoint’s BPO specialties. An eye glass retailer-manufacturerRead More
$1.3M Savings Generated Across 5 Acquisitions
Discussing mergers and acquisitions, accounting and consulting firm Deloitte stated…Read More
Audit Uncovers Unrealized Cost Savings of $250K+
This case study focuses on the potential for cost savings stemming from a…Read More
Vendor Management: 13.6% Savings on Cleaning Services
This vendor management case study is a good example of how RadiusPoint helps large organizations generate…Read More
Social Governance – Distraction or Unavoidable Requirement? An Analysis by RadiusPoint
Social Governance (ESG) will be the new benchmark going forward to ensure that both your organization and brand stay relevant and socially acceptable.Read More
RadiusPoint CEO Sharon Watkins Speaks to UNCAGED
Sharon Watkins interviewed on the Uncaged podcast.Read More
RadiusPoint in the Gartner 2021 Market Guide for TEM
Orlando, FL – January 10, 2022 — The Gartner 2021 Market Guide for Telecom Expense Management…Read More
The Chief Executive Leadership Conference, November 3-4, 2022
solutions for the most pressing challenges facing business leaders today…Read More
BPO: TEM/UEM/MMS Services with a SaaS Platform
Organizations face a slew of factors affecting their employee’s ability to manage successfully the services and…Read More
Go for the Greens Annual Conference, September 22-24, 2022
Walt Disney World Resort…Read More